You are viewing a plain text version of this content. The canonical link for it is here.
Posted to commits@fineract.apache.org by GitBox <gi...@apache.org> on 2021/04/28 03:42:18 UTC
[GitHub] [fineract] BLasan opened a new pull request #1597: Add condition to start TLS (FINERACT-1070)
BLasan opened a new pull request #1597:
URL: https://github.com/apache/fineract/pull/1597
## Description
See [FINERACT-1070](https://issues.apache.org/jira/browse/FINERACT-1070?focusedCommentId=17250886&page=com.atlassian.jira.plugin.system.issuetabpanels%3Acomment-tabpanel#comment-17250886)
Ignore if these details are present on the associated [Apache Fineract JIRA ticket](https://github.com/apache/fineract/pull/1284).
## Checklist
Please make sure these boxes are checked before submitting your pull request - thanks!
- [x] Write the commit message as per https://github.com/apache/fineract/#pull-requests
- [x] Acknowledge that we will not review PRs that are not passing the build _("green")_ - it is your responsibility to get a proposed PR to pass the build, not primarily the project's maintainers.
- [ ] Create/update unit or integration tests for verifying the changes made.
- [x] Follow coding conventions at https://cwiki.apache.org/confluence/display/FINERACT/Coding+Conventions.
- [ ] Add required Swagger annotation and update API documentation at fineract-provider/src/main/resources/static/api-docs/apiLive.htm with details of any API changes
- [x] Submission is not a "code dump". (Large changes can be made "in repository" via a branch. Ask on the developer mailing list for guidance, if required.)
FYI our guidelines for code reviews are at https://cwiki.apache.org/confluence/display/FINERACT/Code+Review+Guide.
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] ptuomola commented on a change in pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
ptuomola commented on a change in pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#discussion_r578790020
##########
File path: fineract-provider/src/main/java/org/apache/fineract/infrastructure/configuration/service/ExternalServicesPropertiesReadPlatformServiceImpl.java
##########
@@ -87,8 +87,6 @@ public SMTPCredentialsData extractData(final ResultSet rs) throws SQLException,
password = value;
} else if (ExternalServicesConstants.SMTP_HOST.equalsIgnoreCase(name)) {
host = value;
- } else if (ExternalServicesConstants.SMTP_PORT.equalsIgnoreCase(name)) {
- port = value;
} else if (ExternalServicesConstants.SMTP_USE_TLS.equalsIgnoreCase(name)) {
Review comment:
Why are we no longer reading the port from the database?
##########
File path: fineract-provider/src/main/java/org/apache/fineract/infrastructure/core/service/GmailBackedPlatformEmailService.java
##########
@@ -55,31 +54,42 @@ public void sendToUserAccount(String organisationName, String contactName, Strin
@Override
public void sendDefinedEmail(EmailDetail emailDetails) {
- final Email email = new SimpleEmail();
final SMTPCredentialsData smtpCredentialsData = this.externalServicesReadPlatformService.getSMTPCredentials();
final String authuser = smtpCredentialsData.getUsername();
final String authpwd = smtpCredentialsData.getPassword();
- // Very Important, Don't use email.setAuthentication()
- email.setAuthenticator(new DefaultAuthenticator(authuser, authpwd));
- email.setDebug(false); // true if you want to debug
- email.setHostName(smtpCredentialsData.getHost());
+ JavaMailSenderImpl mailSender = new JavaMailSenderImpl();
+ mailSender.setHost(smtpCredentialsData.getHost()); // smtp.gmail.com
+ mailSender.setPort(Integer.parseInt(smtpCredentialsData.getPort())); // 587
+
+ // Important: Enable less secure app access for the gmail account used in the following authentication
+
+ mailSender.setUsername(authuser); // use valid gmail address
+ mailSender.setPassword(authpwd); // use password of the above gmail account
+
+ Properties props = mailSender.getJavaMailProperties();
+ props.put("mail.transport.protocol", "smtp");
+ props.put("mail.smtp.auth", "true");
+ props.put("mail.debug", "true");
try {
if (smtpCredentialsData.isUseTLS()) {
- // FINERACT-1070: NOT email.setSSLOnConnect(true); email.setSslSmtpPort(smtpCredentialsData.getPort());
- email.setStartTLSRequired(true);
+ if (smtpCredentialsData.getPort().equals("465")) {
Review comment:
I don't think hardcoding ports is a good idea...
##########
File path: fineract-provider/dependencies.gradle
##########
@@ -80,7 +80,8 @@ dependencies {
'org.webjars:webjars-locator-core',
'com.google.cloud.sql:mysql-socket-factory-connector-j-8:1.2.1',
- 'com.squareup.retrofit2:converter-gson'
+ 'com.squareup.retrofit2:converter-gson',
+ 'com.sun.activation:jakarta.activation:1.2.2'
Review comment:
In addition to adding the implementation jar here, you need to add an exclusion for the API that is brought in by an implied dependency from jakarta-xml.bind-api. Otherwise you get duplicates for the API classes.
##########
File path: fineract-provider/src/main/java/org/apache/fineract/infrastructure/core/service/GmailBackedPlatformEmailService.java
##########
@@ -55,31 +54,42 @@ public void sendToUserAccount(String organisationName, String contactName, Strin
@Override
public void sendDefinedEmail(EmailDetail emailDetails) {
- final Email email = new SimpleEmail();
final SMTPCredentialsData smtpCredentialsData = this.externalServicesReadPlatformService.getSMTPCredentials();
final String authuser = smtpCredentialsData.getUsername();
final String authpwd = smtpCredentialsData.getPassword();
- // Very Important, Don't use email.setAuthentication()
- email.setAuthenticator(new DefaultAuthenticator(authuser, authpwd));
- email.setDebug(false); // true if you want to debug
- email.setHostName(smtpCredentialsData.getHost());
+ JavaMailSenderImpl mailSender = new JavaMailSenderImpl();
+ mailSender.setHost(smtpCredentialsData.getHost()); // smtp.gmail.com
Review comment:
Rather than creating an instance of JavaMailSenderImpl directly here, wouldn't the right solution be to declare JavaMailSender as a bean and let Spring provide it through dependency injection?
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] awasum commented on a change in pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
awasum commented on a change in pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#discussion_r570785195
##########
File path: fineract-provider/src/main/java/org/apache/fineract/infrastructure/core/service/GmailBackedPlatformEmailService.java
##########
@@ -61,6 +64,18 @@ public void sendDefinedEmail(EmailDetail emailDetails) {
final String authuser = smtpCredentialsData.getUsername();
final String authpwd = smtpCredentialsData.getPassword();
+ LOG.info("Use name: ", smtpCredentialsData.getUsername());
+ LOG.info("Use Password: ", smtpCredentialsData.getPassword());
Review comment:
Why are you logging password and some critical information ? You can do this in testing on your Dev environment and then remove these lines as critical information is being exposed here.
##########
File path: fineract-provider/src/main/java/org/apache/fineract/infrastructure/core/service/GmailBackedPlatformEmailService.java
##########
@@ -61,6 +64,18 @@ public void sendDefinedEmail(EmailDetail emailDetails) {
final String authuser = smtpCredentialsData.getUsername();
final String authpwd = smtpCredentialsData.getPassword();
+ LOG.info("Use name: ", smtpCredentialsData.getUsername());
+ LOG.info("Use Password: ", smtpCredentialsData.getPassword());
Review comment:
You can run Fineract on your local machine. Run the front end and test your changes with the default gmail service without setting up your own smtp on your PC. Am I missing something here? advice
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-827816400
@xurror @francisguchie Done
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan closed pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan closed pull request #1597:
URL: https://github.com/apache/fineract/pull/1597
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] awasum commented on a change in pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
awasum commented on a change in pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#discussion_r570799310
##########
File path: fineract-provider/src/main/java/org/apache/fineract/infrastructure/core/service/GmailBackedPlatformEmailService.java
##########
@@ -61,6 +64,18 @@ public void sendDefinedEmail(EmailDetail emailDetails) {
final String authuser = smtpCredentialsData.getUsername();
final String authpwd = smtpCredentialsData.getPassword();
+ LOG.info("Use name: ", smtpCredentialsData.getUsername());
+ LOG.info("Use Password: ", smtpCredentialsData.getPassword());
Review comment:
You can run Fineract on your local machine. Run the front end and test your changes with the default gmail service without setting up your own smtp on your PC. Am I missing something here? advice
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-780775874
> @BLasan look at my closed PR #1625
Have you resolved the version conflicts? Email sending works fine
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-773831280
@francisguchie Please refer the comment [FINERACT-1070](https://issues.apache.org/jira/browse/FINERACT-1070?focusedCommentId=17279365&page=com.atlassian.jira.plugin.system.issuetabpanels%3Acomment-tabpanel#comment-17279365)
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] vorburger commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
vorburger commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-798557309
I've lost track here... is this one good to merge?
@ptuomola would you like to re-review this? Has all of your feedback above been addressed, are you good with this as-is now?
@francisguchie did you functionally test and independently verify this PR - does it solve FINERACT-1070? (Just answer Yes or No.)
@BLasan when we merge this we should "squash" your work of currently 8 commits as 1 single "squashed" clean commit (but don't do it now, because the open review comments would get lost).
PS: See also FINERACT-1335 and FINERACT-1270, but let's not block this anymore, just separate ideas for new future PRs.
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan edited a comment on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan edited a comment on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-780810726
> @BLasan - have u corrected the issue of firstname being taken as the "to-email-address"
Yuh. The name shouldn't be there. It should be an email address. I've removed that. Now works fine
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-775372539
> @BLasan
> I do not get this part clearly
>
> **"Can you try using a gmail to send the email with port=465/587 and host=smtp.gmail.com ? Email domain used in default configurations is not a gmail"**
When you configure email sending there's a configuration for "email from". In FINERACT they use an email which is not a gmail. (Belongs to another email domain). You have already set up the smtp configurations on your machine right? Could you please try by providing a hard coded value for the following configurations.
[email.setFrom()](https://github.com/apache/fineract/pull/1597/files#diff-ff180200f187360b5f3824c6656dcbb79f609f950ef0e90f25cf96df3c47ea96R81) - Replace this with a valid gmail you have (A duplicate one)
[email.addTo()](https://github.com/apache/fineract/blob/bb00c18f274598a02337ad901b2021041c13ccc2/fineract-provider/src/main/java/org/apache/fineract/infrastructure/core/service/GmailBackedPlatformEmailService.java#L86) - Replace email.getAddress() with the email you are going to use for the above email.setFrom() configuration
[email.setAuthenticator()](https://github.com/apache/fineract/blob/bb00c18f274598a02337ad901b2021041c13ccc2/fineract-provider/src/main/java/org/apache/fineract/infrastructure/core/service/GmailBackedPlatformEmailService.java#L65) - Replace with your gmail and the relevant password (Email you are going to use for the above two configurations)
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] francisguchie commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
francisguchie commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-781381243
> Yuh, if we can avoid having the `jakarta.activation/jakarta.activation-api/1.2.2` dependency from javax.mail, we'll be able to resolve this
@BLasan and yet without it we will be getting this error
java.lang.noclassdeffounderror: com/sun/activation/registries/logsupport
i have even tried com.sun.activation:jakarta.activation:1.2.0 as suggested [here] (https://stackoverflow.com/questions/58029104/cant-send-email-using-javamail-and-jdk-12) but i still got an error that 1.2.0 is not available
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] ptuomola commented on a change in pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
ptuomola commented on a change in pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#discussion_r578932732
##########
File path: fineract-provider/src/main/java/org/apache/fineract/infrastructure/core/service/GmailBackedPlatformEmailService.java
##########
@@ -55,31 +54,42 @@ public void sendToUserAccount(String organisationName, String contactName, Strin
@Override
public void sendDefinedEmail(EmailDetail emailDetails) {
- final Email email = new SimpleEmail();
final SMTPCredentialsData smtpCredentialsData = this.externalServicesReadPlatformService.getSMTPCredentials();
final String authuser = smtpCredentialsData.getUsername();
final String authpwd = smtpCredentialsData.getPassword();
- // Very Important, Don't use email.setAuthentication()
- email.setAuthenticator(new DefaultAuthenticator(authuser, authpwd));
- email.setDebug(false); // true if you want to debug
- email.setHostName(smtpCredentialsData.getHost());
+ JavaMailSenderImpl mailSender = new JavaMailSenderImpl();
+ mailSender.setHost(smtpCredentialsData.getHost()); // smtp.gmail.com
+ mailSender.setPort(Integer.parseInt(smtpCredentialsData.getPort())); // 587
+
+ // Important: Enable less secure app access for the gmail account used in the following authentication
+
+ mailSender.setUsername(authuser); // use valid gmail address
+ mailSender.setPassword(authpwd); // use password of the above gmail account
+
+ Properties props = mailSender.getJavaMailProperties();
+ props.put("mail.transport.protocol", "smtp");
+ props.put("mail.smtp.auth", "true");
+ props.put("mail.debug", "true");
try {
if (smtpCredentialsData.isUseTLS()) {
- // FINERACT-1070: NOT email.setSSLOnConnect(true); email.setSslSmtpPort(smtpCredentialsData.getPort());
- email.setStartTLSRequired(true);
+ if (smtpCredentialsData.getPort().equals("465")) {
Review comment:
Hmmm... We should not rely on a port number to decide whether to enable SSL. We should simply have a config parameter to turn it on or off. People can choose to run their mail servers on whatever port they feel like...
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-828282835
Build succeeded. I think now we could go ahead
On Wed, 28 Apr 2021, 03:03 Guchie, ***@***.***> wrote:
> @BLasan <https://github.com/BLasan> the build failed due to some limits
>
> Successfully built 8d6df843f0cf
> Successfully tagged fineract_fineract-server:latest
>
> ERROR: toomanyrequests: You have reached your pull rate limit. You may
> increase the limit by authenticating and upgrading:
> https://www.docker.com/increase-rate-limit
>
> You might want to close and open the PR
>
> —
> You are receiving this because you were mentioned.
> Reply to this email directly, view it on GitHub
> <https://github.com/apache/fineract/pull/1597#issuecomment-827945448>, or
> unsubscribe
> <https://github.com/notifications/unsubscribe-auth/AKI5NS26L2MZ6N3O6ICKMYTTK4USJANCNFSM4WZ7QMLQ>
> .
>
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] francisguchie commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
francisguchie commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-780718173
@BLasan
So i made some thing like this
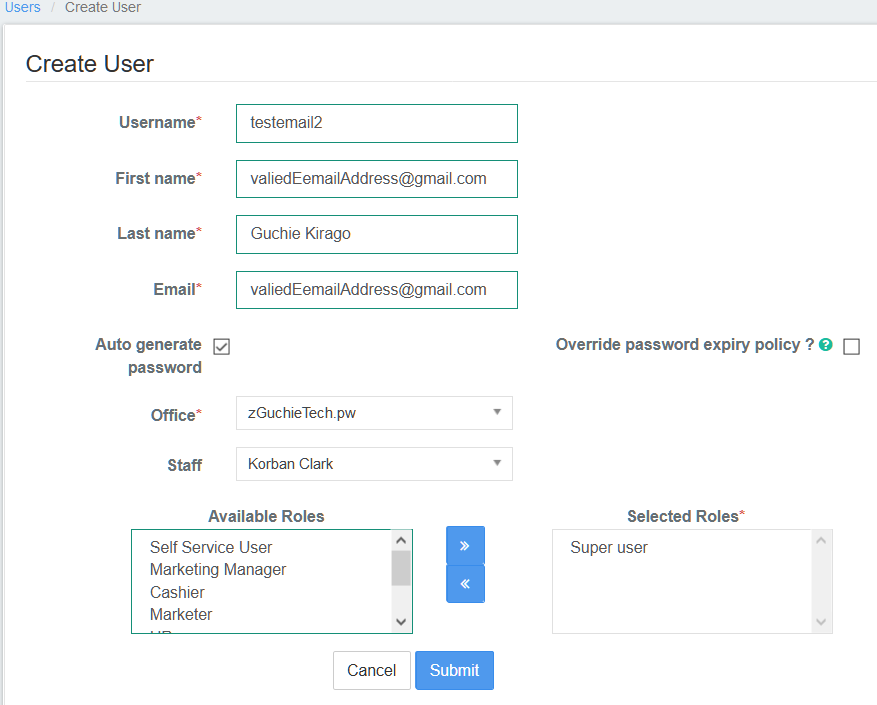
and this worked the password sent and i got the trail below
DEBUG: JavaMail version 1.6.2
DEBUG: successfully loaded resource: /META-INF/javamail.default.address.map
DEBUG: getProvider() returning javax.mail.Provider[TRANSPORT,smtp,com.sun.mail.smtp.SMTPTransport,Oracle]
DEBUG SMTP: useEhlo true, useAuth true
DEBUG SMTP: trying to connect to host "smtp.gmail.com", port 587, isSSL false
220 smtp.gmail.com ESMTP h6sm2819159pfv.84 - gsmtp
DEBUG SMTP: connected to host "smtp.gmail.com", port: 587
EHLO mifosx-18-oldstyle.us-west1-b.c.micro-pilot-276723.internal
250-smtp.gmail.com at your service, [34.105.64.82]
250-SIZE 35882577
250-8BITMIME
250-STARTTLS
250-ENHANCEDSTATUSCODES
250-PIPELINING
250-CHUNKING
250 SMTPUTF8
DEBUG SMTP: Found extension "SIZE", arg "35882577"
DEBUG SMTP: Found extension "8BITMIME", arg ""
DEBUG SMTP: Found extension "STARTTLS", arg ""
DEBUG SMTP: Found extension "ENHANCEDSTATUSCODES", arg ""
DEBUG SMTP: Found extension "PIPELINING", arg ""
DEBUG SMTP: Found extension "CHUNKING", arg ""
DEBUG SMTP: Found extension "SMTPUTF8", arg ""
STARTTLS
220 2.0.0 Ready to start TLS
EHLO mifosx-18-oldstyle.us-west1-b.c.micro-pilot-276723.internal
250-smtp.gmail.com at your service, [34.105.64.82]
250-SIZE 35882577
250-8BITMIME
250-AUTH LOGIN PLAIN XOAUTH2 PLAIN-CLIENTTOKEN OAUTHBEARER XOAUTH
250-ENHANCEDSTATUSCODES
250-PIPELINING
250-CHUNKING
250 SMTPUTF8
DEBUG SMTP: Found extension "SIZE", arg "35882577"
DEBUG SMTP: Found extension "8BITMIME", arg ""
DEBUG SMTP: Found extension "AUTH", arg "LOGIN PLAIN XOAUTH2 PLAIN-CLIENTTOKEN OAUTHBEARER XOAUTH"
DEBUG SMTP: Found extension "ENHANCEDSTATUSCODES", arg ""
DEBUG SMTP: Found extension "PIPELINING", arg ""
DEBUG SMTP: Found extension "CHUNKING", arg ""
DEBUG SMTP: Found extension "SMTPUTF8", arg ""
DEBUG SMTP: protocolConnect login, host=smtp.gmail.com, user=fromemailaddress@gmail.com, password=<non-null>
DEBUG SMTP: Attempt to authenticate using mechanisms: LOGIN PLAIN DIGEST-MD5 NTLM XOAUTH2
DEBUG SMTP: Using mechanism LOGIN
DEBUG SMTP: AUTH LOGIN command trace suppressed
DEBUG SMTP: AUTH LOGIN succeeded
DEBUG SMTP: use8bit false
MAIL FROM:<fr...@gmail.com>
250 2.1.0 OK h6sm2819159pfv.84 - gsmtp
RCPT TO:<va...@gmail.com>
250 2.1.5 OK h6sm2819159pfv.84 - gsmtp
RCPT TO:<va...@gmail.com>
250 2.1.5 OK, duplicate recipients will be consolidated. h6sm2819159pfv.84 - gsmtp
DEBUG SMTP: Verified Addresses
DEBUG SMTP: valiedEmailAddress@gmail.com
DEBUG SMTP: valiedEmailAddress@gmail.com
DATA
354 Go ahead h6sm2819159pfv.84 - gsmtp
Date: Wed, 17 Feb 2021 17:10:05 +0000 (UTC)
From: fromemailaddress@gmail.com
To: valiedEmailAddress@gmail.com, valiedEmailAddress@gmail.com
Message-ID: <11...@mifosx-18-oldstyle.us-west1-b.c.micro-pilot-276723.internal>
Subject: Welcome valiedEmailAddress@gmail.com to zGuchieTech.pw
MIME-Version: 1.0
Content-Type: text/plain; charset=us-ascii
Content-Transfer-Encoding: 7bit
** Email received in the mail box**
You are receiving this email as your email account: valiedEmailAddress@gmail.com has being used to create a user account for an organisation named [zGuchieTech.pw] on Mifos.
You can login using the following credentials:
username: testemail
password: gzyksmjbkgogy
You must change this password upon first log in using Uppercase, Lowercase, number and character.
Thank you and welcome to the organisation.
.
250 2.0.0 OK 1613581806 h6sm2819159pfv.84 - gsmtp
DEBUG SMTP: message successfully delivered to mail server
QUIT
221 2.0.0 closing connection h6sm2819159pfv.84 - gsmtp
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan edited a comment on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan edited a comment on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-780801972
> @BLasan look at my closed PR #1625
You can try out the latest changes by following the above steps I've mentioned. Fixed some minor issues :)
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on a change in pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on a change in pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#discussion_r579044330
##########
File path: fineract-provider/src/main/java/org/apache/fineract/infrastructure/core/service/GmailBackedPlatformEmailService.java
##########
@@ -55,31 +54,42 @@ public void sendToUserAccount(String organisationName, String contactName, Strin
@Override
public void sendDefinedEmail(EmailDetail emailDetails) {
- final Email email = new SimpleEmail();
final SMTPCredentialsData smtpCredentialsData = this.externalServicesReadPlatformService.getSMTPCredentials();
final String authuser = smtpCredentialsData.getUsername();
final String authpwd = smtpCredentialsData.getPassword();
- // Very Important, Don't use email.setAuthentication()
- email.setAuthenticator(new DefaultAuthenticator(authuser, authpwd));
- email.setDebug(false); // true if you want to debug
- email.setHostName(smtpCredentialsData.getHost());
+ JavaMailSenderImpl mailSender = new JavaMailSenderImpl();
+ mailSender.setHost(smtpCredentialsData.getHost()); // smtp.gmail.com
+ mailSender.setPort(Integer.parseInt(smtpCredentialsData.getPort())); // 587
+
+ // Important: Enable less secure app access for the gmail account used in the following authentication
+
+ mailSender.setUsername(authuser); // use valid gmail address
+ mailSender.setPassword(authpwd); // use password of the above gmail account
+
+ Properties props = mailSender.getJavaMailProperties();
+ props.put("mail.transport.protocol", "smtp");
+ props.put("mail.smtp.auth", "true");
+ props.put("mail.debug", "true");
try {
if (smtpCredentialsData.isUseTLS()) {
- // FINERACT-1070: NOT email.setSSLOnConnect(true); email.setSslSmtpPort(smtpCredentialsData.getPort());
- email.setStartTLSRequired(true);
+ if (smtpCredentialsData.getPort().equals("465")) {
Review comment:
Yuh. I think we don't need these changes. The previous implementation was ok. But I think the port number needs to get changed as "587". (For the host: smtp.gmail.com)
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] francisguchie commented on a change in pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
francisguchie commented on a change in pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#discussion_r579084712
##########
File path: fineract-provider/src/main/java/org/apache/fineract/infrastructure/core/service/GmailBackedPlatformEmailService.java
##########
@@ -55,31 +54,42 @@ public void sendToUserAccount(String organisationName, String contactName, Strin
@Override
public void sendDefinedEmail(EmailDetail emailDetails) {
- final Email email = new SimpleEmail();
final SMTPCredentialsData smtpCredentialsData = this.externalServicesReadPlatformService.getSMTPCredentials();
final String authuser = smtpCredentialsData.getUsername();
final String authpwd = smtpCredentialsData.getPassword();
- // Very Important, Don't use email.setAuthentication()
- email.setAuthenticator(new DefaultAuthenticator(authuser, authpwd));
- email.setDebug(false); // true if you want to debug
- email.setHostName(smtpCredentialsData.getHost());
+ JavaMailSenderImpl mailSender = new JavaMailSenderImpl();
+ mailSender.setHost(smtpCredentialsData.getHost()); // smtp.gmail.com
+ mailSender.setPort(Integer.parseInt(smtpCredentialsData.getPort())); // 587
+
+ // Important: Enable less secure app access for the gmail account used in the following authentication
+
+ mailSender.setUsername(authuser); // use valid gmail address
+ mailSender.setPassword(authpwd); // use password of the above gmail account
+
+ Properties props = mailSender.getJavaMailProperties();
+ props.put("mail.transport.protocol", "smtp");
+ props.put("mail.smtp.auth", "true");
+ props.put("mail.debug", "true");
try {
if (smtpCredentialsData.isUseTLS()) {
- // FINERACT-1070: NOT email.setSSLOnConnect(true); email.setSslSmtpPort(smtpCredentialsData.getPort());
- email.setStartTLSRequired(true);
+ if (smtpCredentialsData.getPort().equals("465")) {
Review comment:
> We read the port from smtpCredentials and just check the port number to make sure whether we want to enable ssl or not
yes @BLasan - we are reading if the port is 587 then we set UseSTARTTLS=YES if port 465 then we set it to false and this condition works very well in my view as it avoids un-necessary errors that shall come from the servers
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] francisguchie commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
francisguchie commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-780714878
@BLasan
i have made 2 discoveries
1- i was getting the error
java.lang.NoClassDefFoundError: com/sun/activation/registries/LogSupport so i added an implementation dependency
'com.sun.activation:javax.activation:1.2.0', in dependencies.gradle
AFTER adding the above i discovered that
2- The user name is being considered as the email being sent to thus the message see image below

so i got the error below
DEBUG: JavaMail version 1.6.2
DEBUG: successfully loaded resource: /META-INF/javamail.default.address.map
DEBUG: getProvider() returning javax.mail.Provider[TRANSPORT,smtp,com.sun.mail.smtp.SMTPTransport,Oracle]
DEBUG SMTP: useEhlo true, useAuth true
DEBUG SMTP: trying to connect to host "smtp.gmail.com", port 587, isSSL false
220 smtp.gmail.com ESMTP n1sm3229351pgn.94 - gsmtp
DEBUG SMTP: connected to host "smtp.gmail.com", port: 587
EHLO mifosx-18-oldstyle.us-west1-b.c.micro-pilot-276723.internal
250-smtp.gmail.com at your service, [34.105.64.82]
250-SIZE 35882577
250-8BITMIME
250-STARTTLS
250-ENHANCEDSTATUSCODES
250-PIPELINING
250-CHUNKING
250 SMTPUTF8
DEBUG SMTP: Found extension "SIZE", arg "35882577"
DEBUG SMTP: Found extension "8BITMIME", arg ""
DEBUG SMTP: Found extension "STARTTLS", arg ""
DEBUG SMTP: Found extension "ENHANCEDSTATUSCODES", arg ""
DEBUG SMTP: Found extension "PIPELINING", arg ""
DEBUG SMTP: Found extension "CHUNKING", arg ""
DEBUG SMTP: Found extension "SMTPUTF8", arg ""
STARTTLS
220 2.0.0 Ready to start TLS
EHLO mifosx-18-oldstyle.us-west1-b.c.micro-pilot-276723.internal
250-smtp.gmail.com at your service, [34.105.64.82]
250-SIZE 35882577
250-8BITMIME
250-AUTH LOGIN PLAIN XOAUTH2 PLAIN-CLIENTTOKEN OAUTHBEARER XOAUTH
250-ENHANCEDSTATUSCODES
250-PIPELINING
250-CHUNKING
250 SMTPUTF8
DEBUG SMTP: Found extension "SIZE", arg "35882577"
DEBUG SMTP: Found extension "8BITMIME", arg ""
DEBUG SMTP: Found extension "AUTH", arg "LOGIN PLAIN XOAUTH2 PLAIN-CLIENTTOKEN OAUTHBEARER XOAUTH"
DEBUG SMTP: Found extension "ENHANCEDSTATUSCODES", arg ""
DEBUG SMTP: Found extension "PIPELINING", arg ""
DEBUG SMTP: Found extension "CHUNKING", arg ""
DEBUG SMTP: Found extension "SMTPUTF8", arg ""
DEBUG SMTP: protocolConnect login, host=smtp.gmail.com, user=fromemailaddress@gmail.com, password=<non-null>
DEBUG SMTP: Attempt to authenticate using mechanisms: LOGIN PLAIN DIGEST-MD5 NTLM XOAUTH2
DEBUG SMTP: Using mechanism LOGIN
DEBUG SMTP: AUTH LOGIN command trace suppressed
DEBUG SMTP: AUTH LOGIN succeeded
DEBUG SMTP: use8bit false
MAIL FROM:<fr...@gmail.com>
250 2.1.0 OK n1sm3229351pgn.94 - gsmtp
RCPT TO:<va...@gmail.com>
250 2.1.5 OK n1sm3229351pgn.94 - gsmtp
RCPT TO:<Francois>
553 5.1.3 The recipient address <Francois> is not a valid RFC-5321 address. n1sm3229351pgn.94 - gsmtp
DEBUG SMTP: Valid Unsent Addresses
DEBUG SMTP: valiedEmailAddress@gmail.com
DEBUG SMTP: Invalid Addresses
DEBUG SMTP: Francois
DEBUG SMTP: Sending failed because of invalid destination addresses
RSET
250 2.1.5 Flushed n1sm3229351pgn.94 - gsmtp
DEBUG SMTP: MessagingException while sending, THROW:
javax.mail.SendFailedException: Invalid Addresses;
nested exception is:
com.sun.mail.smtp.SMTPAddressFailedException: 553 5.1.3 The recipient address <Francois> is not a valid RFC-5321 address. n1sm3229351pgn.94 - gsmtp
at com.sun.mail.smtp.SMTPTransport.rcptTo(SMTPTransport.java:2079)
at com.sun.mail.smtp.SMTPTransport.sendMessage(SMTPTransport.java:1301)
at org.springframework.mail.javamail.JavaMailSenderImpl.doSend(JavaMailSenderImpl.java:465)
at org.springframework.mail.javamail.JavaMailSenderImpl.send(JavaMailSenderImpl.java:323)
at org.springframework.mail.javamail.JavaMailSenderImpl.send(JavaMailSenderImpl.java:312)
at org.apache.fineract.infrastructure.core.service.GmailBackedPlatformEmailService.sendDefinedEmail(GmailBackedPlatformEmailService.java:92)
at org.apache.fineract.infrastructure.core.service.GmailBackedPlatformEmailService.sendToUserAccount(GmailBackedPlatformEmailService.java:54)
at org.apache.fineract.useradministration.domain.JpaUserDomainService.create(JpaUserDomainService.java:56)
at org.apache.fineract.useradministration.domain.JpaUserDomainService$$FastClassBySpringCGLIB$$6e9ae4ae.invoke(<generated>)
at org.springframework.cglib.proxy.MethodProxy.invoke(MethodProxy.java:218)
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.invokeJoinpoint(CglibAopProxy.java:771)
at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:163)
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.proceed(CglibAopProxy.java:749)
at org.springframework.transaction.interceptor.TransactionAspectSupport.invokeWithinTransaction(TransactionAspectSupport.java:367)
at org.springframework.transaction.interceptor.TransactionInterceptor.invoke(TransactionInterceptor.java:118)
at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:186)
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.proceed(CglibAopProxy.java:749)
at org.springframework.aop.framework.CglibAopProxy$DynamicAdvisedInterceptor.intercept(CglibAopProxy.java:691)
at org.apache.fineract.useradministration.domain.JpaUserDomainService$$EnhancerBySpringCGLIB$$dad28d42.create(<generated>)
at org.apache.fineract.useradministration.service.AppUserWritePlatformServiceJpaRepositoryImpl.createUser(AppUserWritePlatformServiceJpaRepositoryImpl.java:153)
at org.apache.fineract.useradministration.service.AppUserWritePlatformServiceJpaRepositoryImpl$$FastClassBySpringCGLIB$$fc767456.invoke(<generated>)
at org.springframework.cglib.proxy.MethodProxy.invoke(MethodProxy.java:218)
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.invokeJoinpoint(CglibAopProxy.java:771)
at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:163)
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.proceed(CglibAopProxy.java:749)
at org.springframework.transaction.interceptor.TransactionAspectSupport.invokeWithinTransaction(TransactionAspectSupport.java:367)
at org.springframework.transaction.interceptor.TransactionInterceptor.invoke(TransactionInterceptor.java:118)
at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:186)
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.proceed(CglibAopProxy.java:749)
at org.springframework.aop.framework.CglibAopProxy$DynamicAdvisedInterceptor.intercept(CglibAopProxy.java:691)
at org.apache.fineract.useradministration.service.AppUserWritePlatformServiceJpaRepositoryImpl$$EnhancerBySpringCGLIB$$44a8453a.createUser(<generated>)
at org.apache.fineract.useradministration.handler.CreateUserCommandHandler.processCommand(CreateUserCommandHandler.java:45)
at org.apache.fineract.useradministration.handler.CreateUserCommandHandler$$FastClassBySpringCGLIB$$d7a3d31.invoke(<generated>)
at org.springframework.cglib.proxy.MethodProxy.invoke(MethodProxy.java:218)
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.invokeJoinpoint(CglibAopProxy.java:771)
at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:163)
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.proceed(CglibAopProxy.java:749)
at org.springframework.transaction.interceptor.TransactionAspectSupport.invokeWithinTransaction(TransactionAspectSupport.java:367)
at org.springframework.transaction.interceptor.TransactionInterceptor.invoke(TransactionInterceptor.java:118)
at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:186)
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.proceed(CglibAopProxy.java:749)
at org.springframework.aop.framework.CglibAopProxy$DynamicAdvisedInterceptor.intercept(CglibAopProxy.java:691)
at org.apache.fineract.useradministration.handler.CreateUserCommandHandler$$EnhancerBySpringCGLIB$$fa5e80ab.processCommand(<generated>)
at org.apache.fineract.commands.service.SynchronousCommandProcessingService.processAndLogCommand(SynchronousCommandProcessingService.java:95)
at org.apache.fineract.commands.service.SynchronousCommandProcessingService$$FastClassBySpringCGLIB$$ec92d53f.invoke(<generated>)
at org.springframework.cglib.proxy.MethodProxy.invoke(MethodProxy.java:218)
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.invokeJoinpoint(CglibAopProxy.java:771)
at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:163)
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.proceed(CglibAopProxy.java:749)
at org.springframework.transaction.interceptor.TransactionAspectSupport.invokeWithinTransaction(TransactionAspectSupport.java:367)
at org.springframework.transaction.interceptor.TransactionInterceptor.invoke(TransactionInterceptor.java:118)
at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:186)
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.proceed(CglibAopProxy.java:749)
at org.springframework.aop.framework.CglibAopProxy$DynamicAdvisedInterceptor.intercept(CglibAopProxy.java:691)
at org.apache.fineract.commands.service.SynchronousCommandProcessingService$$EnhancerBySpringCGLIB$$3248c195.processAndLogCommand(<generated>)
at org.apache.fineract.commands.service.PortfolioCommandSourceWritePlatformServiceImpl.logCommandSource(PortfolioCommandSourceWritePlatformServiceImpl.java:99)
at org.apache.fineract.commands.service.PortfolioCommandSourceWritePlatformServiceImpl$$FastClassBySpringCGLIB$$31c15082.invoke(<generated>)
at org.springframework.cglib.proxy.MethodProxy.invoke(MethodProxy.java:218)
at org.springframework.aop.framework.CglibAopProxy$DynamicAdvisedInterceptor.intercept(CglibAopProxy.java:687)
at org.apache.fineract.commands.service.PortfolioCommandSourceWritePlatformServiceImpl$$EnhancerBySpringCGLIB$$8aedd53e.logCommandSource(<generated>)
at org.apache.fineract.useradministration.api.UsersApiResource.create(UsersApiResource.java:185)
at java.base/jdk.internal.reflect.NativeMethodAccessorImpl.invoke0(Native Method)
at java.base/jdk.internal.reflect.NativeMethodAccessorImpl.invoke(NativeMethodAccessorImpl.java:62)
at java.base/jdk.internal.reflect.DelegatingMethodAccessorImpl.invoke(DelegatingMethodAccessorImpl.java:43)
at java.base/java.lang.reflect.Method.invoke(Method.java:566)
at com.sun.jersey.spi.container.JavaMethodInvokerFactory$1.invoke(JavaMethodInvokerFactory.java:60)
at com.sun.jersey.server.impl.model.method.dispatch.AbstractResourceMethodDispatchProvider$TypeOutInvoker._dispatch(AbstractResourceMethodDispatchProvider.java:185)
at com.sun.jersey.server.impl.model.method.dispatch.ResourceJavaMethodDispatcher.dispatch(ResourceJavaMethodDispatcher.java:75)
at com.sun.jersey.server.impl.uri.rules.HttpMethodRule.accept(HttpMethodRule.java:302)
at com.sun.jersey.server.impl.uri.rules.ResourceClassRule.accept(ResourceClassRule.java:108)
at com.sun.jersey.server.impl.uri.rules.RightHandPathRule.accept(RightHandPathRule.java:147)
at com.sun.jersey.server.impl.uri.rules.RootResourceClassesRule.accept(RootResourceClassesRule.java:84)
at com.sun.jersey.server.impl.application.WebApplicationImpl._handleRequest(WebApplicationImpl.java:1542)
at com.sun.jersey.server.impl.application.WebApplicationImpl._handleRequest(WebApplicationImpl.java:1473)
at com.sun.jersey.server.impl.application.WebApplicationImpl.handleRequest(WebApplicationImpl.java:1419)
at com.sun.jersey.server.impl.application.WebApplicationImpl.handleRequest(WebApplicationImpl.java:1409)
at com.sun.jersey.spi.container.servlet.WebComponent.service(WebComponent.java:409)
at com.sun.jersey.spi.container.servlet.ServletContainer.service(ServletContainer.java:558)
at com.sun.jersey.spi.container.servlet.ServletContainer.service(ServletContainer.java:733)
at javax.servlet.http.HttpServlet.service(HttpServlet.java:733)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:231)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166)
at org.apache.tomcat.websocket.server.WsFilter.doFilter(WsFilter.java:53)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166)
at org.springframework.security.web.access.intercept.FilterSecurityInterceptor.invoke(FilterSecurityInterceptor.java:115)
at org.springframework.security.web.access.intercept.FilterSecurityInterceptor.doFilter(FilterSecurityInterceptor.java:90)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:320)
at org.springframework.security.web.access.intercept.FilterSecurityInterceptor.invoke(FilterSecurityInterceptor.java:115)
at org.springframework.security.web.access.intercept.FilterSecurityInterceptor.doFilter(FilterSecurityInterceptor.java:90)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.access.ExceptionTranslationFilter.doFilter(ExceptionTranslationFilter.java:118)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.authentication.AnonymousAuthenticationFilter.doFilter(AnonymousAuthenticationFilter.java:111)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.servletapi.SecurityContextHolderAwareRequestFilter.doFilter(SecurityContextHolderAwareRequestFilter.java:158)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.apache.fineract.infrastructure.security.filter.InsecureTwoFactorAuthenticationFilter.doFilter(InsecureTwoFactorAuthenticationFilter.java:75)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:113)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:113)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:113)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.context.SecurityContextPersistenceFilter.doFilter(SecurityContextPersistenceFilter.java:82)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.access.channel.ChannelProcessingFilter.doFilter(ChannelProcessingFilter.java:157)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.FilterChainProxy.doFilterInternal(FilterChainProxy.java:215)
at org.springframework.security.web.FilterChainProxy.doFilter(FilterChainProxy.java:186)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:320)
at org.springframework.security.web.access.intercept.FilterSecurityInterceptor.invoke(FilterSecurityInterceptor.java:126)
at org.springframework.security.web.access.intercept.FilterSecurityInterceptor.doFilter(FilterSecurityInterceptor.java:90)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.access.ExceptionTranslationFilter.doFilter(ExceptionTranslationFilter.java:118)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.authentication.AnonymousAuthenticationFilter.doFilter(AnonymousAuthenticationFilter.java:111)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.servletapi.SecurityContextHolderAwareRequestFilter.doFilter(SecurityContextHolderAwareRequestFilter.java:158)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.apache.fineract.infrastructure.security.filter.InsecureTwoFactorAuthenticationFilter.doFilter(InsecureTwoFactorAuthenticationFilter.java:75)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.header.HeaderWriterFilter.doHeadersAfter(HeaderWriterFilter.java:92)
at org.springframework.security.web.header.HeaderWriterFilter.doFilterInternal(HeaderWriterFilter.java:77)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:119)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.context.request.async.WebAsyncManagerIntegrationFilter.doFilterInternal(WebAsyncManagerIntegrationFilter.java:56)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:119)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.authentication.www.BasicAuthenticationFilter.doFilterInternal(BasicAuthenticationFilter.java:204)
at org.apache.fineract.infrastructure.security.filter.TenantAwareBasicAuthenticationFilter.doFilterInternal(TenantAwareBasicAuthenticationFilter.java:144)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:119)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.context.SecurityContextPersistenceFilter.doFilter(SecurityContextPersistenceFilter.java:105)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.access.channel.ChannelProcessingFilter.doFilter(ChannelProcessingFilter.java:157)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.FilterChainProxy.doFilterInternal(FilterChainProxy.java:215)
at org.springframework.security.web.FilterChainProxy.doFilter(FilterChainProxy.java:178)
at org.springframework.web.filter.DelegatingFilterProxy.invokeDelegate(DelegatingFilterProxy.java:358)
at org.springframework.web.filter.DelegatingFilterProxy.doFilter(DelegatingFilterProxy.java:271)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166)
at org.springframework.boot.actuate.metrics.web.servlet.WebMvcMetricsFilter.doFilterInternal(WebMvcMetricsFilter.java:93)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:119)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166)
at org.springframework.boot.web.servlet.support.ErrorPageFilter.doFilter(ErrorPageFilter.java:126)
at org.springframework.boot.web.servlet.support.ErrorPageFilter.access$000(ErrorPageFilter.java:64)
at org.springframework.boot.web.servlet.support.ErrorPageFilter$1.doFilterInternal(ErrorPageFilter.java:101)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:119)
at org.springframework.boot.web.servlet.support.ErrorPageFilter.doFilter(ErrorPageFilter.java:119)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166)
at org.springframework.web.filter.CharacterEncodingFilter.doFilterInternal(CharacterEncodingFilter.java:201)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:119)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:103)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166)
at org.apache.catalina.core.StandardWrapperValve.invoke(StandardWrapperValve.java:202)
at org.apache.catalina.core.StandardContextValve.invoke(StandardContextValve.java:96)
at org.apache.catalina.authenticator.AuthenticatorBase.invoke(AuthenticatorBase.java:541)
at org.apache.catalina.core.StandardHostValve.invoke(StandardHostValve.java:139)
at org.apache.catalina.valves.ErrorReportValve.invoke(ErrorReportValve.java:92)
at org.apache.catalina.valves.AbstractAccessLogValve.invoke(AbstractAccessLogValve.java:690)
at org.apache.catalina.core.StandardEngineValve.invoke(StandardEngineValve.java:74)
at org.apache.catalina.connector.CoyoteAdapter.service(CoyoteAdapter.java:343)
at org.apache.coyote.http11.Http11Processor.service(Http11Processor.java:373)
at org.apache.coyote.AbstractProcessorLight.process(AbstractProcessorLight.java:65)
at org.apache.coyote.AbstractProtocol$ConnectionHandler.process(AbstractProtocol.java:868)
at org.apache.tomcat.util.net.NioEndpoint$SocketProcessor.doRun(NioEndpoint.java:1589)
at org.apache.tomcat.util.net.SocketProcessorBase.run(SocketProcessorBase.java:49)
at java.base/java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1128)
at java.base/java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:628)
at org.apache.tomcat.util.threads.TaskThread$WrappingRunnable.run(TaskThread.java:61)
at java.base/java.lang.Thread.run(Thread.java:834)
Caused by: com.sun.mail.smtp.SMTPAddressFailedException: 553 5.1.3 The recipient address <Francois> is not a valid RFC-5321 address. n1sm3229351pgn.94 - gsmtp
at com.sun.mail.smtp.SMTPTransport.rcptTo(SMTPTransport.java:1932)
... 182 more
QUIT
221 2.0.0 closing connection n1sm3229351pgn.94 - gsmtp
2021-02-17 17:06:43.360 ERROR 26113 --- [nio-443-exec-12] serWritePlatformServiceJpaRepositoryImpl : createUser: PlatformEmailSendException
org.apache.fineract.infrastructure.core.service.PlatformEmailSendException: org.springframework.mail.MailSendException: Failed messages: javax.mail.SendFailedException: Invalid Addresses;
nested exception is:
com.sun.mail.smtp.SMTPAddressFailedException: 553 5.1.3 The recipient address <Francois> is not a valid RFC-5321 address. n1sm3229351pgn.94 - gsmtp
; message exceptions (1) are:
Failed message 1: javax.mail.SendFailedException: Invalid Addresses;
nested exception is:
com.sun.mail.smtp.SMTPAddressFailedException: 553 5.1.3 The recipient address <Francois> is not a valid RFC-5321 address. n1sm3229351pgn.94 - gsmtp
at org.apache.fineract.infrastructure.core.service.GmailBackedPlatformEmailService.sendDefinedEmail(GmailBackedPlatformEmailService.java:95)
at org.apache.fineract.infrastructure.core.service.GmailBackedPlatformEmailService.sendToUserAccount(GmailBackedPlatformEmailService.java:54)
at org.apache.fineract.useradministration.domain.JpaUserDomainService.create(JpaUserDomainService.java:56)
at org.apache.fineract.useradministration.domain.JpaUserDomainService$$FastClassBySpringCGLIB$$6e9ae4ae.invoke(<generated>)
at org.springframework.cglib.proxy.MethodProxy.invoke(MethodProxy.java:218)
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.invokeJoinpoint(CglibAopProxy.java:771)
at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:163)
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.proceed(CglibAopProxy.java:749)
at org.springframework.transaction.interceptor.TransactionAspectSupport.invokeWithinTransaction(TransactionAspectSupport.java:367)
at org.springframework.transaction.interceptor.TransactionInterceptor.invoke(TransactionInterceptor.java:118)
at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:186)
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.proceed(CglibAopProxy.java:749)
at org.springframework.aop.framework.CglibAopProxy$DynamicAdvisedInterceptor.intercept(CglibAopProxy.java:691)
at org.apache.fineract.useradministration.domain.JpaUserDomainService$$EnhancerBySpringCGLIB$$dad28d42.create(<generated>)
at org.apache.fineract.useradministration.service.AppUserWritePlatformServiceJpaRepositoryImpl.createUser(AppUserWritePlatformServiceJpaRepositoryImpl.java:153)
at org.apache.fineract.useradministration.service.AppUserWritePlatformServiceJpaRepositoryImpl$$FastClassBySpringCGLIB$$fc767456.invoke(<generated>)
at org.springframework.cglib.proxy.MethodProxy.invoke(MethodProxy.java:218)
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.invokeJoinpoint(CglibAopProxy.java:771)
at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:163)
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.proceed(CglibAopProxy.java:749)
at org.springframework.transaction.interceptor.TransactionAspectSupport.invokeWithinTransaction(TransactionAspectSupport.java:367)
at org.springframework.transaction.interceptor.TransactionInterceptor.invoke(TransactionInterceptor.java:118)
at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:186)
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.proceed(CglibAopProxy.java:749)
at org.springframework.aop.framework.CglibAopProxy$DynamicAdvisedInterceptor.intercept(CglibAopProxy.java:691)
at org.apache.fineract.useradministration.service.AppUserWritePlatformServiceJpaRepositoryImpl$$EnhancerBySpringCGLIB$$44a8453a.createUser(<generated>)
at org.apache.fineract.useradministration.handler.CreateUserCommandHandler.processCommand(CreateUserCommandHandler.java:45)
at org.apache.fineract.useradministration.handler.CreateUserCommandHandler$$FastClassBySpringCGLIB$$d7a3d31.invoke(<generated>)
at org.springframework.cglib.proxy.MethodProxy.invoke(MethodProxy.java:218)
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.invokeJoinpoint(CglibAopProxy.java:771)
at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:163)
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.proceed(CglibAopProxy.java:749)
at org.springframework.transaction.interceptor.TransactionAspectSupport.invokeWithinTransaction(TransactionAspectSupport.java:367)
at org.springframework.transaction.interceptor.TransactionInterceptor.invoke(TransactionInterceptor.java:118)
at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:186)
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.proceed(CglibAopProxy.java:749)
at org.springframework.aop.framework.CglibAopProxy$DynamicAdvisedInterceptor.intercept(CglibAopProxy.java:691)
at org.apache.fineract.useradministration.handler.CreateUserCommandHandler$$EnhancerBySpringCGLIB$$fa5e80ab.processCommand(<generated>)
at org.apache.fineract.commands.service.SynchronousCommandProcessingService.processAndLogCommand(SynchronousCommandProcessingService.java:95)
at org.apache.fineract.commands.service.SynchronousCommandProcessingService$$FastClassBySpringCGLIB$$ec92d53f.invoke(<generated>)
at org.springframework.cglib.proxy.MethodProxy.invoke(MethodProxy.java:218)
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.invokeJoinpoint(CglibAopProxy.java:771)
at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:163)
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.proceed(CglibAopProxy.java:749)
at org.springframework.transaction.interceptor.TransactionAspectSupport.invokeWithinTransaction(TransactionAspectSupport.java:367)
at org.springframework.transaction.interceptor.TransactionInterceptor.invoke(TransactionInterceptor.java:118)
at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:186)
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.proceed(CglibAopProxy.java:749)
at org.springframework.aop.framework.CglibAopProxy$DynamicAdvisedInterceptor.intercept(CglibAopProxy.java:691)
at org.apache.fineract.commands.service.SynchronousCommandProcessingService$$EnhancerBySpringCGLIB$$3248c195.processAndLogCommand(<generated>)
at org.apache.fineract.commands.service.PortfolioCommandSourceWritePlatformServiceImpl.logCommandSource(PortfolioCommandSourceWritePlatformServiceImpl.java:99)
at org.apache.fineract.commands.service.PortfolioCommandSourceWritePlatformServiceImpl$$FastClassBySpringCGLIB$$31c15082.invoke(<generated>)
at org.springframework.cglib.proxy.MethodProxy.invoke(MethodProxy.java:218)
at org.springframework.aop.framework.CglibAopProxy$DynamicAdvisedInterceptor.intercept(CglibAopProxy.java:687)
at org.apache.fineract.commands.service.PortfolioCommandSourceWritePlatformServiceImpl$$EnhancerBySpringCGLIB$$8aedd53e.logCommandSource(<generated>)
at org.apache.fineract.useradministration.api.UsersApiResource.create(UsersApiResource.java:185)
at java.base/jdk.internal.reflect.NativeMethodAccessorImpl.invoke0(Native Method)
at java.base/jdk.internal.reflect.NativeMethodAccessorImpl.invoke(NativeMethodAccessorImpl.java:62)
at java.base/jdk.internal.reflect.DelegatingMethodAccessorImpl.invoke(DelegatingMethodAccessorImpl.java:43)
at java.base/java.lang.reflect.Method.invoke(Method.java:566)
at com.sun.jersey.spi.container.JavaMethodInvokerFactory$1.invoke(JavaMethodInvokerFactory.java:60)
at com.sun.jersey.server.impl.model.method.dispatch.AbstractResourceMethodDispatchProvider$TypeOutInvoker._dispatch(AbstractResourceMethodDispatchProvider.java:185)
at com.sun.jersey.server.impl.model.method.dispatch.ResourceJavaMethodDispatcher.dispatch(ResourceJavaMethodDispatcher.java:75)
at com.sun.jersey.server.impl.uri.rules.HttpMethodRule.accept(HttpMethodRule.java:302)
at com.sun.jersey.server.impl.uri.rules.ResourceClassRule.accept(ResourceClassRule.java:108)
at com.sun.jersey.server.impl.uri.rules.RightHandPathRule.accept(RightHandPathRule.java:147)
at com.sun.jersey.server.impl.uri.rules.RootResourceClassesRule.accept(RootResourceClassesRule.java:84)
at com.sun.jersey.server.impl.application.WebApplicationImpl._handleRequest(WebApplicationImpl.java:1542)
at com.sun.jersey.server.impl.application.WebApplicationImpl._handleRequest(WebApplicationImpl.java:1473)
at com.sun.jersey.server.impl.application.WebApplicationImpl.handleRequest(WebApplicationImpl.java:1419)
at com.sun.jersey.server.impl.application.WebApplicationImpl.handleRequest(WebApplicationImpl.java:1409)
at com.sun.jersey.spi.container.servlet.WebComponent.service(WebComponent.java:409)
at com.sun.jersey.spi.container.servlet.ServletContainer.service(ServletContainer.java:558)
at com.sun.jersey.spi.container.servlet.ServletContainer.service(ServletContainer.java:733)
at javax.servlet.http.HttpServlet.service(HttpServlet.java:733)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:231)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166)
at org.apache.tomcat.websocket.server.WsFilter.doFilter(WsFilter.java:53)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166)
at org.springframework.security.web.access.intercept.FilterSecurityInterceptor.invoke(FilterSecurityInterceptor.java:115)
at org.springframework.security.web.access.intercept.FilterSecurityInterceptor.doFilter(FilterSecurityInterceptor.java:90)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:320)
at org.springframework.security.web.access.intercept.FilterSecurityInterceptor.invoke(FilterSecurityInterceptor.java:115)
at org.springframework.security.web.access.intercept.FilterSecurityInterceptor.doFilter(FilterSecurityInterceptor.java:90)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.access.ExceptionTranslationFilter.doFilter(ExceptionTranslationFilter.java:118)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.authentication.AnonymousAuthenticationFilter.doFilter(AnonymousAuthenticationFilter.java:111)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.servletapi.SecurityContextHolderAwareRequestFilter.doFilter(SecurityContextHolderAwareRequestFilter.java:158)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.apache.fineract.infrastructure.security.filter.InsecureTwoFactorAuthenticationFilter.doFilter(InsecureTwoFactorAuthenticationFilter.java:75)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:113)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:113)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:113)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.context.SecurityContextPersistenceFilter.doFilter(SecurityContextPersistenceFilter.java:82)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.access.channel.ChannelProcessingFilter.doFilter(ChannelProcessingFilter.java:157)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.FilterChainProxy.doFilterInternal(FilterChainProxy.java:215)
at org.springframework.security.web.FilterChainProxy.doFilter(FilterChainProxy.java:186)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:320)
at org.springframework.security.web.access.intercept.FilterSecurityInterceptor.invoke(FilterSecurityInterceptor.java:126)
at org.springframework.security.web.access.intercept.FilterSecurityInterceptor.doFilter(FilterSecurityInterceptor.java:90)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.access.ExceptionTranslationFilter.doFilter(ExceptionTranslationFilter.java:118)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.authentication.AnonymousAuthenticationFilter.doFilter(AnonymousAuthenticationFilter.java:111)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.servletapi.SecurityContextHolderAwareRequestFilter.doFilter(SecurityContextHolderAwareRequestFilter.java:158)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.apache.fineract.infrastructure.security.filter.InsecureTwoFactorAuthenticationFilter.doFilter(InsecureTwoFactorAuthenticationFilter.java:75)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.header.HeaderWriterFilter.doHeadersAfter(HeaderWriterFilter.java:92)
at org.springframework.security.web.header.HeaderWriterFilter.doFilterInternal(HeaderWriterFilter.java:77)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:119)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.context.request.async.WebAsyncManagerIntegrationFilter.doFilterInternal(WebAsyncManagerIntegrationFilter.java:56)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:119)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.authentication.www.BasicAuthenticationFilter.doFilterInternal(BasicAuthenticationFilter.java:204)
at org.apache.fineract.infrastructure.security.filter.TenantAwareBasicAuthenticationFilter.doFilterInternal(TenantAwareBasicAuthenticationFilter.java:144)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:119)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.context.SecurityContextPersistenceFilter.doFilter(SecurityContextPersistenceFilter.java:105)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.access.channel.ChannelProcessingFilter.doFilter(ChannelProcessingFilter.java:157)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.FilterChainProxy.doFilterInternal(FilterChainProxy.java:215)
at org.springframework.security.web.FilterChainProxy.doFilter(FilterChainProxy.java:178)
at org.springframework.web.filter.DelegatingFilterProxy.invokeDelegate(DelegatingFilterProxy.java:358)
at org.springframework.web.filter.DelegatingFilterProxy.doFilter(DelegatingFilterProxy.java:271)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166)
at org.springframework.boot.actuate.metrics.web.servlet.WebMvcMetricsFilter.doFilterInternal(WebMvcMetricsFilter.java:93)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:119)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166)
at org.springframework.boot.web.servlet.support.ErrorPageFilter.doFilter(ErrorPageFilter.java:126)
at org.springframework.boot.web.servlet.support.ErrorPageFilter.access$000(ErrorPageFilter.java:64)
at org.springframework.boot.web.servlet.support.ErrorPageFilter$1.doFilterInternal(ErrorPageFilter.java:101)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:119)
at org.springframework.boot.web.servlet.support.ErrorPageFilter.doFilter(ErrorPageFilter.java:119)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166)
at org.springframework.web.filter.CharacterEncodingFilter.doFilterInternal(CharacterEncodingFilter.java:201)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:119)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:103)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166)
at org.apache.catalina.core.StandardWrapperValve.invoke(StandardWrapperValve.java:202)
at org.apache.catalina.core.StandardContextValve.invoke(StandardContextValve.java:96)
at org.apache.catalina.authenticator.AuthenticatorBase.invoke(AuthenticatorBase.java:541)
at org.apache.catalina.core.StandardHostValve.invoke(StandardHostValve.java:139)
at org.apache.catalina.valves.ErrorReportValve.invoke(ErrorReportValve.java:92)
at org.apache.catalina.valves.AbstractAccessLogValve.invoke(AbstractAccessLogValve.java:690)
at org.apache.catalina.core.StandardEngineValve.invoke(StandardEngineValve.java:74)
at org.apache.catalina.connector.CoyoteAdapter.service(CoyoteAdapter.java:343)
at org.apache.coyote.http11.Http11Processor.service(Http11Processor.java:373)
at org.apache.coyote.AbstractProcessorLight.process(AbstractProcessorLight.java:65)
at org.apache.coyote.AbstractProtocol$ConnectionHandler.process(AbstractProtocol.java:868)
at org.apache.tomcat.util.net.NioEndpoint$SocketProcessor.doRun(NioEndpoint.java:1589)
at org.apache.tomcat.util.net.SocketProcessorBase.run(SocketProcessorBase.java:49)
at java.base/java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1128)
at java.base/java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:628)
at org.apache.tomcat.util.threads.TaskThread$WrappingRunnable.run(TaskThread.java:61)
at java.base/java.lang.Thread.run(Thread.java:834)
Caused by: org.springframework.mail.MailSendException: Failed messages: javax.mail.SendFailedException: Invalid Addresses;
nested exception is:
com.sun.mail.smtp.SMTPAddressFailedException: 553 5.1.3 The recipient address <Francois> is not a valid RFC-5321 address. n1sm3229351pgn.94 - gsmtp
at org.springframework.mail.javamail.JavaMailSenderImpl.doSend(JavaMailSenderImpl.java:491)
at org.springframework.mail.javamail.JavaMailSenderImpl.send(JavaMailSenderImpl.java:323)
at org.springframework.mail.javamail.JavaMailSenderImpl.send(JavaMailSenderImpl.java:312)
at org.apache.fineract.infrastructure.core.service.GmailBackedPlatformEmailService.sendDefinedEmail(GmailBackedPlatformEmailService.java:92)
... 177 common frames omitted
at clicking the submit button i get the error below
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] francisguchie commented on a change in pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
francisguchie commented on a change in pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#discussion_r579078504
##########
File path: fineract-provider/dependencies.gradle
##########
@@ -80,7 +80,8 @@ dependencies {
'org.webjars:webjars-locator-core',
'com.google.cloud.sql:mysql-socket-factory-connector-j-8:1.2.1',
- 'com.squareup.retrofit2:converter-gson'
+ 'com.squareup.retrofit2:converter-gson',
+ 'com.sun.activation:jakarta.activation:1.2.2'
Review comment:
> Great!! . I was in a dilemma on how that duplicate jakarta-api dependency gets installed. I'll try that. First I'll resolve this failing test cases.
@BLasan i excluded and it worked see this https://github.com/apache/fineract/pull/1627/commits/cff63783cd77beb92cb92e5449ad77002e4ac6ad
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] ptuomola commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
ptuomola commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-781371198
Hi - instead of excluding this from the check, you really should look to exclude the duplicate inclusion of the same dependency. It only makes sense to remove it from the check if there is no other way to avoid it - eg if two different jars, which are both required, contain the same class. But that's not the case here, so excluding one of the dependencies would be the right way forward IMHO.
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on a change in pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on a change in pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#discussion_r578989301
##########
File path: fineract-provider/src/main/java/org/apache/fineract/infrastructure/configuration/service/ExternalServicesPropertiesReadPlatformServiceImpl.java
##########
@@ -87,8 +87,6 @@ public SMTPCredentialsData extractData(final ResultSet rs) throws SQLException,
password = value;
} else if (ExternalServicesConstants.SMTP_HOST.equalsIgnoreCase(name)) {
host = value;
- } else if (ExternalServicesConstants.SMTP_PORT.equalsIgnoreCase(name)) {
- port = value;
} else if (ExternalServicesConstants.SMTP_USE_TLS.equalsIgnoreCase(name)) {
Review comment:
Yeah, we could change that. But I need to verify whether these changes are good to proceed.
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on a change in pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on a change in pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#discussion_r570801779
##########
File path: fineract-provider/src/main/java/org/apache/fineract/infrastructure/core/service/GmailBackedPlatformEmailService.java
##########
@@ -61,6 +64,18 @@ public void sendDefinedEmail(EmailDetail emailDetails) {
final String authuser = smtpCredentialsData.getUsername();
final String authpwd = smtpCredentialsData.getPassword();
+ LOG.info("Use name: ", smtpCredentialsData.getUsername());
+ LOG.info("Use Password: ", smtpCredentialsData.getPassword());
Review comment:
Let me try this sir :)
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] vorburger commented on a change in pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
vorburger commented on a change in pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#discussion_r593768189
##########
File path: fineract-provider/dependencies.gradle
##########
@@ -80,7 +80,8 @@ dependencies {
'org.webjars:webjars-locator-core',
'com.google.cloud.sql:mysql-socket-factory-connector-j-8:1.2.1',
- 'com.squareup.retrofit2:converter-gson'
+ 'com.squareup.retrofit2:converter-gson',
+ 'com.sun.activation:jakarta.activation:1.2.2'
Review comment:
@BLasan @ptuomola I've not looked closely here, but it seems to be that using 'com.sun.activation:jakarta.activation:1.2.2' is confusing, because it (probably, not verified) contains the exact same Java classes as the 'jakarta.activation' artifact... we should clean this up IMHO, but that could be done in a future PR.
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-780858198
> @BLasan you have removed the javax dependency (is it because its needed for the import org.slf4j.Logger; import org.slf4j.LoggerFactory; importations ?
> I just want to learn , thanks
I think there's no need of adding dependency for those imports. javax activation is needed in email sending. Some logging issue was coming out btw when we invoke the API
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] francisguchie edited a comment on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
francisguchie edited a comment on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-774112571
> @awasum @francisguchie Default port and the host are 25 and smtp.gmail.com respectively. Is this correct? Gmail smtp server uses 587 & 465 ports to send email. Should we change these values accordingly?
@BLasan
originally, it was set as such , where fineract was ignoring the set port and i created an issue [here](https://issues.apache.org/jira/browse/FINERACT-1070)
Even if use sets the following, MifosX will not send emails
1- Configure the server on which mifos is installed to be able to send Emails - One can do this by installing sSMTP on the server and testing email sending on the command line
2- if using a gmail address only ports 465 and 587 will work because port 25 is by default disabled on google servers This includes very many other VPS / Mail servers
3- Configure the port under the Email External Services Configuration
one will still get the error below
03-Jul-2020 19:59:41.251 SEVERE [https-jsse-nio-443-exec-18]
com.sun.jersey.spi.container.ContainerResponse.mapMappableContainerException
The RuntimeException could not be mapped to a response, re-throwing to the HTTP container
org.apache.fineract.infrastructure.core.service.PlatformEmailSendException:
org.apache.commons.mail.EmailException:
Sending the email to the following server failed : smtp.gmail.com:25
at org.apache.fineract.infrastructure.core.service.GmailBackedPlatformEmailService.sendDefinedEmail(GmailBackedPlatformEmailService.java:81)
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] francisguchie edited a comment on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
francisguchie edited a comment on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-775899245
@BLasan this is what i have used ( with the actual emails of course )
**sudo nano /etc/ssmtp/ssmtp.conf**
## root user email address
root=valiedemail@gmail.com
## The place where the mail goes. The actual machine name is required no
## MX records are consulted. Commonly mailhosts are named mail.domain.com
mailhub=smtp.gmail.com:587
AuthUser=valiedemail@gmail.com
AuthPass=itspassword
UseTLS=YES
UseSTARTTLS=YES
## Where will the mail seem to come from?
## rewriteDomain=
rewriteDomain=gmail.com
**sudo nano /etc/ssmtp/revaliases**
----------------------------------------------------------------------
## sSMTP aliases
#### Format: local_account:outgoing_address:mailhub
## Example: root:your_login@your.domain:mailhub.your.domain[:port]
## where [:port] is an optional port number that defaults to 25.
root:valiedemail@gmail.com:smtp.gmail.com:587
I hope this helps to figure out if i have mixed up something somewhere
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-814011296
@xurror will make the changes ASAP. Thanks for the review :)
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan edited a comment on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan edited a comment on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-774385179
> @BLasan
> before i even test this condition is likely to fail **String port = "465"; boolean useTLS = false;**
>
> please note that for both ports 465 and 587
> boolean useTLS = true; is required for these ports to send mail
>
> but for 587
> boolean setStartTLSRequired= true; must be added
> and for 465
> boolean setStartTLSRequired= true; should be removed
Yeah, those conditions are already added. Can we use smtp.gmail.com to send an email from a non-gmail address to a gmail address? "From" email address is not a gmail address. I checked it inside the mysql container.
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] francisguchie commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
francisguchie commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-774250390
@BLasan
**Change the default port to "465" and prevent loading from mysql. Now smtp.gmail.com will use port 465 for email sending. Can you please try again with these changes?** this option does not work
but i will test with the logging you have added so i can capture the details and i will revert
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] francisguchie commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
francisguchie commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-775751216
@BLasan
Here is my "Hard Code"
if (smtpCredentialsData.isUseTLS()) {
email.setSslSmtpPort(smtpCredentialsData.getPort());
if (smtpCredentialsData.getPort().equals("465")) {
email.setStartTLSRequired(false);
} else if (smtpCredentialsData.getPort().equals("587")) {
email.setStartTLSRequired(true);
}
}
email.setSmtpPort(Integer.parseInt(smtpCredentialsData.getPort()));
email.setFrom("avalidedemail@gmail.com", "the senders Name");
email.setAuthenticator(new DefaultAuthenticator("avalidedemail@gmail.com", "itspassword"));
email.setSubject(emailDetails.getSubject());
email.setMsg(emailDetails.getBody());
email.addTo("avalidedemail@gmail.com", "the senders Name");
email.send();
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-774061604
@awasum @francisguchie Default port and the host are 25 and smtp.gmail.com respectively. Is this correct? Gmail smtp server uses 587 & 465 ports to send email. Should we change these values accordingly?
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan edited a comment on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan edited a comment on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-775372539
> @BLasan
> I do not get this part clearly
>
> **"Can you try using a gmail to send the email with port=465/587 and host=smtp.gmail.com ? Email domain used in default configurations is not a gmail"**
When you configure email sending there's a configuration for "email from". In FINERACT they use an email which is not a gmail. (Belongs to another email domain). You have already set up the smtp configurations on your machine right? Could you please try by providing hard coded values for the following configurations.
[email.setFrom()](https://github.com/apache/fineract/pull/1597/files#diff-ff180200f187360b5f3824c6656dcbb79f609f950ef0e90f25cf96df3c47ea96R81) - Replace this with a valid gmail you have (A duplicate one)
[email.addTo()](https://github.com/apache/fineract/blob/bb00c18f274598a02337ad901b2021041c13ccc2/fineract-provider/src/main/java/org/apache/fineract/infrastructure/core/service/GmailBackedPlatformEmailService.java#L86) - Replace email.getAddress() with the email you are going to use for the above email.setFrom() configuration
[email.setAuthenticator()](https://github.com/apache/fineract/blob/bb00c18f274598a02337ad901b2021041c13ccc2/fineract-provider/src/main/java/org/apache/fineract/infrastructure/core/service/GmailBackedPlatformEmailService.java#L65) - Replace with your gmail and the relevant password (Email you are going to use for the above two configurations)
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-781391887
> > Yuh, if we can avoid having the `jakarta.activation/jakarta.activation-api/1.2.2` dependency from javax.mail, we'll be able to resolve this
>
> @BLasan and yet without it we will be getting this error
> java.lang.noclassdeffounderror: com/sun/activation/registries/logsupport
>
> i have even tried com.sun.activation:jakarta.activation:1.2.0 as suggested [here] (https://stackoverflow.com/questions/58029104/cant-send-email-using-javamail-and-jdk-12) but i still got an error that 1.2.0 is not available
Does the version matter? I tried that approach earlier. But got the same issue. I think we need to remove `jakarta.activation/jakarta.activation-api/1.2.2` . If we could exclude that dependency when installing `javax.mail`, I think we can resolve this issue. If you do have any idea on resolving this, please try and update us here. I'll give a try from my side (already tried multiple approaches) :)
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on a change in pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on a change in pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#discussion_r578924812
##########
File path: fineract-provider/src/main/java/org/apache/fineract/infrastructure/core/service/GmailBackedPlatformEmailService.java
##########
@@ -55,31 +54,42 @@ public void sendToUserAccount(String organisationName, String contactName, Strin
@Override
public void sendDefinedEmail(EmailDetail emailDetails) {
- final Email email = new SimpleEmail();
final SMTPCredentialsData smtpCredentialsData = this.externalServicesReadPlatformService.getSMTPCredentials();
final String authuser = smtpCredentialsData.getUsername();
final String authpwd = smtpCredentialsData.getPassword();
- // Very Important, Don't use email.setAuthentication()
- email.setAuthenticator(new DefaultAuthenticator(authuser, authpwd));
- email.setDebug(false); // true if you want to debug
- email.setHostName(smtpCredentialsData.getHost());
+ JavaMailSenderImpl mailSender = new JavaMailSenderImpl();
+ mailSender.setHost(smtpCredentialsData.getHost()); // smtp.gmail.com
Review comment:
Yuh, we can follow that approach as well. Main intention was to resolve this email sending issue. I'll do that if this changes are approved by the community. Thanks for the idea :)
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] ptuomola commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
ptuomola commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-793309926
Hi @vorburger - the last thing I'm aware of was the question from @BLasan on whether this PR is required - i.e. if you set the port and the server name correctly using the existing configuration parameters, will it not just work?
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] francisguchie commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
francisguchie commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-780834600
@BLasan Yes we are good to go. Test works like a charm
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan edited a comment on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan edited a comment on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-775280345
@vorburger @francisguchie Shall we give a try to resolve this issue?
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on a change in pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on a change in pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#discussion_r578989301
##########
File path: fineract-provider/src/main/java/org/apache/fineract/infrastructure/configuration/service/ExternalServicesPropertiesReadPlatformServiceImpl.java
##########
@@ -87,8 +87,6 @@ public SMTPCredentialsData extractData(final ResultSet rs) throws SQLException,
password = value;
} else if (ExternalServicesConstants.SMTP_HOST.equalsIgnoreCase(name)) {
host = value;
- } else if (ExternalServicesConstants.SMTP_PORT.equalsIgnoreCase(name)) {
- port = value;
} else if (ExternalServicesConstants.SMTP_USE_TLS.equalsIgnoreCase(name)) {
Review comment:
Yeah, we could change that. But I first need to verify whether these changes are good to proceed.
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-825813336
@francisguchie Is this PR ok?
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-781223474
@vorburger Build fails due to the two dependencies javax and jakarta-api. jakarta.activation will automatically add both the dependencies which leads to fail the fineract testing. `com.sun.mail.javax` will also import javax.activation-api & jakarta.activation-api. Would like to hear some suggestions for this PR sir
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-781365843
> @BLasan we will have to add some ignore statements in the duplicates helper file. let me hunt for the section ( i think i did this before for pentaho) my challenge is my limited knowledge in java
Ok. Go ahead. Thanks for taking up that issue :)
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] francisguchie commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
francisguchie commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-781367947
@BLasan we need to add an exclusion in here ClasspathHellDuplicatesChecker.java
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-829854349
> We've stagnated enough on this.
> I'll merge this and we can resolve subsequent problems if they occur separately.
Sure, thanks
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-780810726
> @BLasan - have u corrected the issue of firstname being taken as the "to-email-address"
Yuh. The name cannot be there. It should be an email address. I've removed that. Now works fine
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] francisguchie commented on a change in pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
francisguchie commented on a change in pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#discussion_r579083354
##########
File path: fineract-provider/src/main/java/org/apache/fineract/infrastructure/core/service/GmailBackedPlatformEmailService.java
##########
@@ -55,31 +54,42 @@ public void sendToUserAccount(String organisationName, String contactName, Strin
@Override
public void sendDefinedEmail(EmailDetail emailDetails) {
- final Email email = new SimpleEmail();
final SMTPCredentialsData smtpCredentialsData = this.externalServicesReadPlatformService.getSMTPCredentials();
final String authuser = smtpCredentialsData.getUsername();
final String authpwd = smtpCredentialsData.getPassword();
- // Very Important, Don't use email.setAuthentication()
- email.setAuthenticator(new DefaultAuthenticator(authuser, authpwd));
- email.setDebug(false); // true if you want to debug
- email.setHostName(smtpCredentialsData.getHost());
+ JavaMailSenderImpl mailSender = new JavaMailSenderImpl();
+ mailSender.setHost(smtpCredentialsData.getHost()); // smtp.gmail.com
+ mailSender.setPort(Integer.parseInt(smtpCredentialsData.getPort())); // 587
+
+ // Important: Enable less secure app access for the gmail account used in the following authentication
+
+ mailSender.setUsername(authuser); // use valid gmail address
+ mailSender.setPassword(authpwd); // use password of the above gmail account
+
+ Properties props = mailSender.getJavaMailProperties();
+ props.put("mail.transport.protocol", "smtp");
+ props.put("mail.smtp.auth", "true");
+ props.put("mail.debug", "true");
try {
if (smtpCredentialsData.isUseTLS()) {
- // FINERACT-1070: NOT email.setSSLOnConnect(true); email.setSslSmtpPort(smtpCredentialsData.getPort());
- email.setStartTLSRequired(true);
+ if (smtpCredentialsData.getPort().equals("465")) {
Review comment:
> I don't think hardcoding ports is a good idea...
@ptuomola i do agree with you and that is why i created an issue an the jira about this https://issues.apache.org/jira/browse/FINERACT-1070 which when checked @vorburger agreed
I was thinking that me and @BLasan were trying to get things done (by hard cording) and once we are thoroughly done, we shall make sure that variables are picked from the database as per the users settings
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] francisguchie commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
francisguchie commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-780847480
@BLasan you have removed the javax dependency (is it because its needed for the import org.slf4j.Logger; import org.slf4j.LoggerFactory; importations ?
I just want to learn , thanks
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on a change in pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on a change in pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#discussion_r570796803
##########
File path: fineract-provider/src/main/java/org/apache/fineract/infrastructure/core/service/GmailBackedPlatformEmailService.java
##########
@@ -61,6 +64,18 @@ public void sendDefinedEmail(EmailDetail emailDetails) {
final String authuser = smtpCredentialsData.getUsername();
final String authpwd = smtpCredentialsData.getPassword();
+ LOG.info("Use name: ", smtpCredentialsData.getUsername());
+ LOG.info("Use Password: ", smtpCredentialsData.getPassword());
Review comment:
I haven't configured smtp on my pc. @francisguchie can use these logs to test the scenario in his own machine. This needs to be a draft PR. I'll change this into a draft one :)
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] francisguchie edited a comment on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
francisguchie edited a comment on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-775899245
@BLasan
this is what i have used ( with the actual emails of course )
**sudo nano /etc/ssmtp/ssmtp.conf**
---------------------------------------------------------------------------------------------
## root user email address
root=valiedemail@gmail.com
## The place where the mail goes. The actual machine name is required no
## MX records are consulted. Commonly mailhosts are named mail.domain.com
mailhub=smtp.gmail.com:587
AuthUser=valiedemail@gmail.com
AuthPass=itspassword
UseTLS=YES
UseSTARTTLS=YES
## Where will the mail seem to come from?
## rewriteDomain=
rewriteDomain=gmail.com
**sudo nano /etc/ssmtp/revaliases**
----------------------------------------------------------------------
## sSMTP aliases
##
## Format: local_account:outgoing_address:mailhub
## Example: root:your_login@your.domain:mailhub.your.domain[:port]
## where [:port] is an optional port number that defaults to 25.
root:valiedemail@gmail.com:smtp.gmail.com:587
I hope this helps to figure out if i have mixed up something somewhere
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] xurror merged pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
xurror merged pull request #1597:
URL: https://github.com/apache/fineract/pull/1597
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-773831280
@francisguchie Please refer the comment [FINERACT-1070](https://issues.apache.org/jira/browse/FINERACT-1070?focusedCommentId=17279365&page=com.atlassian.jira.plugin.system.issuetabpanels%3Acomment-tabpanel#comment-17279365)
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] xurror commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
xurror commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-827528245
Also @BLasan, this PR has too many commits. We cannot merge this with all those commits. Can you squash them?
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] francisguchie edited a comment on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
francisguchie edited a comment on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-780714878
@BLasan
**i have made 2 discoveries**
1- i was getting the error initially
java.lang.NoClassDefFoundError: com/sun/activation/registries/LogSupport so i added an implementation dependency
'com.sun.activation:javax.activation:1.2.0', in dependencies.gradle
AFTER adding the above i discovered that
2- The user name is being considered as the email being sent to thus the message see image below

**at clicking the submit button i get the error below**
DEBUG: JavaMail version 1.6.2
DEBUG: successfully loaded resource: /META-INF/javamail.default.address.map
DEBUG: getProvider() returning javax.mail.Provider[TRANSPORT,smtp,com.sun.mail.smtp.SMTPTransport,Oracle]
DEBUG SMTP: useEhlo true, useAuth true
DEBUG SMTP: trying to connect to host "smtp.gmail.com", port 587, isSSL false
220 smtp.gmail.com ESMTP n1sm3229351pgn.94 - gsmtp
DEBUG SMTP: connected to host "smtp.gmail.com", port: 587
EHLO mifosx-18-oldstyle.us-west1-b.c.micro-pilot-276723.internal
250-smtp.gmail.com at your service, [34.105.64.82]
250-SIZE 35882577
250-8BITMIME
250-STARTTLS
250-ENHANCEDSTATUSCODES
250-PIPELINING
250-CHUNKING
250 SMTPUTF8
DEBUG SMTP: Found extension "SIZE", arg "35882577"
DEBUG SMTP: Found extension "8BITMIME", arg ""
DEBUG SMTP: Found extension "STARTTLS", arg ""
DEBUG SMTP: Found extension "ENHANCEDSTATUSCODES", arg ""
DEBUG SMTP: Found extension "PIPELINING", arg ""
DEBUG SMTP: Found extension "CHUNKING", arg ""
DEBUG SMTP: Found extension "SMTPUTF8", arg ""
STARTTLS
220 2.0.0 Ready to start TLS
EHLO mifosx-18-oldstyle.us-west1-b.c.micro-pilot-276723.internal
250-smtp.gmail.com at your service, [34.105.64.82]
250-SIZE 35882577
250-8BITMIME
250-AUTH LOGIN PLAIN XOAUTH2 PLAIN-CLIENTTOKEN OAUTHBEARER XOAUTH
250-ENHANCEDSTATUSCODES
250-PIPELINING
250-CHUNKING
250 SMTPUTF8
DEBUG SMTP: Found extension "SIZE", arg "35882577"
DEBUG SMTP: Found extension "8BITMIME", arg ""
DEBUG SMTP: Found extension "AUTH", arg "LOGIN PLAIN XOAUTH2 PLAIN-CLIENTTOKEN OAUTHBEARER XOAUTH"
DEBUG SMTP: Found extension "ENHANCEDSTATUSCODES", arg ""
DEBUG SMTP: Found extension "PIPELINING", arg ""
DEBUG SMTP: Found extension "CHUNKING", arg ""
DEBUG SMTP: Found extension "SMTPUTF8", arg ""
DEBUG SMTP: protocolConnect login, host=smtp.gmail.com, user=fromemailaddress@gmail.com, password=<non-null>
DEBUG SMTP: Attempt to authenticate using mechanisms: LOGIN PLAIN DIGEST-MD5 NTLM XOAUTH2
DEBUG SMTP: Using mechanism LOGIN
DEBUG SMTP: AUTH LOGIN command trace suppressed
DEBUG SMTP: AUTH LOGIN succeeded
DEBUG SMTP: use8bit false
MAIL FROM:<fr...@gmail.com>
250 2.1.0 OK n1sm3229351pgn.94 - gsmtp
RCPT TO:<va...@gmail.com>
250 2.1.5 OK n1sm3229351pgn.94 - gsmtp
RCPT TO:<Francois>
553 5.1.3 The recipient address <Francois> is not a valid RFC-5321 address. n1sm3229351pgn.94 - gsmtp
DEBUG SMTP: Valid Unsent Addresses
DEBUG SMTP: valiedEmailAddress@gmail.com
DEBUG SMTP: Invalid Addresses
DEBUG SMTP: Francois
DEBUG SMTP: Sending failed because of invalid destination addresses
RSET
250 2.1.5 Flushed n1sm3229351pgn.94 - gsmtp
DEBUG SMTP: MessagingException while sending, THROW:
javax.mail.SendFailedException: Invalid Addresses;
nested exception is:
com.sun.mail.smtp.SMTPAddressFailedException: 553 5.1.3 The recipient address <Francois> is not a valid RFC-5321 address. n1sm3229351pgn.94 - gsmtp
at com.sun.mail.smtp.SMTPTransport.rcptTo(SMTPTransport.java:2079)
at com.sun.mail.smtp.SMTPTransport.sendMessage(SMTPTransport.java:1301)
at org.springframework.mail.javamail.JavaMailSenderImpl.doSend(JavaMailSenderImpl.java:465)
at org.springframework.mail.javamail.JavaMailSenderImpl.send(JavaMailSenderImpl.java:323)
at org.springframework.mail.javamail.JavaMailSenderImpl.send(JavaMailSenderImpl.java:312)
at org.apache.fineract.infrastructure.core.service.GmailBackedPlatformEmailService.sendDefinedEmail(GmailBackedPlatformEmailService.java:92)
at org.apache.fineract.infrastructure.core.service.GmailBackedPlatformEmailService.sendToUserAccount(GmailBackedPlatformEmailService.java:54)
at org.apache.fineract.useradministration.domain.JpaUserDomainService.create(JpaUserDomainService.java:56)
at org.apache.fineract.useradministration.domain.JpaUserDomainService$$FastClassBySpringCGLIB$$6e9ae4ae.invoke(<generated>)
at org.springframework.cglib.proxy.MethodProxy.invoke(MethodProxy.java:218)
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.invokeJoinpoint(CglibAopProxy.java:771)
at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:163)
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.proceed(CglibAopProxy.java:749)
at org.springframework.transaction.interceptor.TransactionAspectSupport.invokeWithinTransaction(TransactionAspectSupport.java:367)
at org.springframework.transaction.interceptor.TransactionInterceptor.invoke(TransactionInterceptor.java:118)
at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:186)
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.proceed(CglibAopProxy.java:749)
at org.springframework.aop.framework.CglibAopProxy$DynamicAdvisedInterceptor.intercept(CglibAopProxy.java:691)
at org.apache.fineract.useradministration.domain.JpaUserDomainService$$EnhancerBySpringCGLIB$$dad28d42.create(<generated>)
at org.apache.fineract.useradministration.service.AppUserWritePlatformServiceJpaRepositoryImpl.createUser(AppUserWritePlatformServiceJpaRepositoryImpl.java:153)
at org.apache.fineract.useradministration.service.AppUserWritePlatformServiceJpaRepositoryImpl$$FastClassBySpringCGLIB$$fc767456.invoke(<generated>)
at org.springframework.cglib.proxy.MethodProxy.invoke(MethodProxy.java:218)
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.invokeJoinpoint(CglibAopProxy.java:771)
at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:163)
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.proceed(CglibAopProxy.java:749)
at org.springframework.transaction.interceptor.TransactionAspectSupport.invokeWithinTransaction(TransactionAspectSupport.java:367)
at org.springframework.transaction.interceptor.TransactionInterceptor.invoke(TransactionInterceptor.java:118)
at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:186)
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.proceed(CglibAopProxy.java:749)
at org.springframework.aop.framework.CglibAopProxy$DynamicAdvisedInterceptor.intercept(CglibAopProxy.java:691)
at org.apache.fineract.useradministration.service.AppUserWritePlatformServiceJpaRepositoryImpl$$EnhancerBySpringCGLIB$$44a8453a.createUser(<generated>)
at org.apache.fineract.useradministration.handler.CreateUserCommandHandler.processCommand(CreateUserCommandHandler.java:45)
at org.apache.fineract.useradministration.handler.CreateUserCommandHandler$$FastClassBySpringCGLIB$$d7a3d31.invoke(<generated>)
at org.springframework.cglib.proxy.MethodProxy.invoke(MethodProxy.java:218)
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.invokeJoinpoint(CglibAopProxy.java:771)
at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:163)
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.proceed(CglibAopProxy.java:749)
at org.springframework.transaction.interceptor.TransactionAspectSupport.invokeWithinTransaction(TransactionAspectSupport.java:367)
at org.springframework.transaction.interceptor.TransactionInterceptor.invoke(TransactionInterceptor.java:118)
at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:186)
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.proceed(CglibAopProxy.java:749)
at org.springframework.aop.framework.CglibAopProxy$DynamicAdvisedInterceptor.intercept(CglibAopProxy.java:691)
at org.apache.fineract.useradministration.handler.CreateUserCommandHandler$$EnhancerBySpringCGLIB$$fa5e80ab.processCommand(<generated>)
at org.apache.fineract.commands.service.SynchronousCommandProcessingService.processAndLogCommand(SynchronousCommandProcessingService.java:95)
at org.apache.fineract.commands.service.SynchronousCommandProcessingService$$FastClassBySpringCGLIB$$ec92d53f.invoke(<generated>)
at org.springframework.cglib.proxy.MethodProxy.invoke(MethodProxy.java:218)
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.invokeJoinpoint(CglibAopProxy.java:771)
at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:163)
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.proceed(CglibAopProxy.java:749)
at org.springframework.transaction.interceptor.TransactionAspectSupport.invokeWithinTransaction(TransactionAspectSupport.java:367)
at org.springframework.transaction.interceptor.TransactionInterceptor.invoke(TransactionInterceptor.java:118)
at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:186)
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.proceed(CglibAopProxy.java:749)
at org.springframework.aop.framework.CglibAopProxy$DynamicAdvisedInterceptor.intercept(CglibAopProxy.java:691)
at org.apache.fineract.commands.service.SynchronousCommandProcessingService$$EnhancerBySpringCGLIB$$3248c195.processAndLogCommand(<generated>)
at org.apache.fineract.commands.service.PortfolioCommandSourceWritePlatformServiceImpl.logCommandSource(PortfolioCommandSourceWritePlatformServiceImpl.java:99)
at org.apache.fineract.commands.service.PortfolioCommandSourceWritePlatformServiceImpl$$FastClassBySpringCGLIB$$31c15082.invoke(<generated>)
at org.springframework.cglib.proxy.MethodProxy.invoke(MethodProxy.java:218)
at org.springframework.aop.framework.CglibAopProxy$DynamicAdvisedInterceptor.intercept(CglibAopProxy.java:687)
at org.apache.fineract.commands.service.PortfolioCommandSourceWritePlatformServiceImpl$$EnhancerBySpringCGLIB$$8aedd53e.logCommandSource(<generated>)
at org.apache.fineract.useradministration.api.UsersApiResource.create(UsersApiResource.java:185)
at java.base/jdk.internal.reflect.NativeMethodAccessorImpl.invoke0(Native Method)
at java.base/jdk.internal.reflect.NativeMethodAccessorImpl.invoke(NativeMethodAccessorImpl.java:62)
at java.base/jdk.internal.reflect.DelegatingMethodAccessorImpl.invoke(DelegatingMethodAccessorImpl.java:43)
at java.base/java.lang.reflect.Method.invoke(Method.java:566)
at com.sun.jersey.spi.container.JavaMethodInvokerFactory$1.invoke(JavaMethodInvokerFactory.java:60)
at com.sun.jersey.server.impl.model.method.dispatch.AbstractResourceMethodDispatchProvider$TypeOutInvoker._dispatch(AbstractResourceMethodDispatchProvider.java:185)
at com.sun.jersey.server.impl.model.method.dispatch.ResourceJavaMethodDispatcher.dispatch(ResourceJavaMethodDispatcher.java:75)
at com.sun.jersey.server.impl.uri.rules.HttpMethodRule.accept(HttpMethodRule.java:302)
at com.sun.jersey.server.impl.uri.rules.ResourceClassRule.accept(ResourceClassRule.java:108)
at com.sun.jersey.server.impl.uri.rules.RightHandPathRule.accept(RightHandPathRule.java:147)
at com.sun.jersey.server.impl.uri.rules.RootResourceClassesRule.accept(RootResourceClassesRule.java:84)
at com.sun.jersey.server.impl.application.WebApplicationImpl._handleRequest(WebApplicationImpl.java:1542)
at com.sun.jersey.server.impl.application.WebApplicationImpl._handleRequest(WebApplicationImpl.java:1473)
at com.sun.jersey.server.impl.application.WebApplicationImpl.handleRequest(WebApplicationImpl.java:1419)
at com.sun.jersey.server.impl.application.WebApplicationImpl.handleRequest(WebApplicationImpl.java:1409)
at com.sun.jersey.spi.container.servlet.WebComponent.service(WebComponent.java:409)
at com.sun.jersey.spi.container.servlet.ServletContainer.service(ServletContainer.java:558)
at com.sun.jersey.spi.container.servlet.ServletContainer.service(ServletContainer.java:733)
at javax.servlet.http.HttpServlet.service(HttpServlet.java:733)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:231)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166)
at org.apache.tomcat.websocket.server.WsFilter.doFilter(WsFilter.java:53)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166)
at org.springframework.security.web.access.intercept.FilterSecurityInterceptor.invoke(FilterSecurityInterceptor.java:115)
at org.springframework.security.web.access.intercept.FilterSecurityInterceptor.doFilter(FilterSecurityInterceptor.java:90)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:320)
at org.springframework.security.web.access.intercept.FilterSecurityInterceptor.invoke(FilterSecurityInterceptor.java:115)
at org.springframework.security.web.access.intercept.FilterSecurityInterceptor.doFilter(FilterSecurityInterceptor.java:90)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.access.ExceptionTranslationFilter.doFilter(ExceptionTranslationFilter.java:118)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.authentication.AnonymousAuthenticationFilter.doFilter(AnonymousAuthenticationFilter.java:111)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.servletapi.SecurityContextHolderAwareRequestFilter.doFilter(SecurityContextHolderAwareRequestFilter.java:158)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.apache.fineract.infrastructure.security.filter.InsecureTwoFactorAuthenticationFilter.doFilter(InsecureTwoFactorAuthenticationFilter.java:75)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:113)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:113)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:113)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.context.SecurityContextPersistenceFilter.doFilter(SecurityContextPersistenceFilter.java:82)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.access.channel.ChannelProcessingFilter.doFilter(ChannelProcessingFilter.java:157)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.FilterChainProxy.doFilterInternal(FilterChainProxy.java:215)
at org.springframework.security.web.FilterChainProxy.doFilter(FilterChainProxy.java:186)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:320)
at org.springframework.security.web.access.intercept.FilterSecurityInterceptor.invoke(FilterSecurityInterceptor.java:126)
at org.springframework.security.web.access.intercept.FilterSecurityInterceptor.doFilter(FilterSecurityInterceptor.java:90)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.access.ExceptionTranslationFilter.doFilter(ExceptionTranslationFilter.java:118)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.authentication.AnonymousAuthenticationFilter.doFilter(AnonymousAuthenticationFilter.java:111)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.servletapi.SecurityContextHolderAwareRequestFilter.doFilter(SecurityContextHolderAwareRequestFilter.java:158)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.apache.fineract.infrastructure.security.filter.InsecureTwoFactorAuthenticationFilter.doFilter(InsecureTwoFactorAuthenticationFilter.java:75)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.header.HeaderWriterFilter.doHeadersAfter(HeaderWriterFilter.java:92)
at org.springframework.security.web.header.HeaderWriterFilter.doFilterInternal(HeaderWriterFilter.java:77)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:119)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.context.request.async.WebAsyncManagerIntegrationFilter.doFilterInternal(WebAsyncManagerIntegrationFilter.java:56)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:119)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.authentication.www.BasicAuthenticationFilter.doFilterInternal(BasicAuthenticationFilter.java:204)
at org.apache.fineract.infrastructure.security.filter.TenantAwareBasicAuthenticationFilter.doFilterInternal(TenantAwareBasicAuthenticationFilter.java:144)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:119)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.context.SecurityContextPersistenceFilter.doFilter(SecurityContextPersistenceFilter.java:105)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.access.channel.ChannelProcessingFilter.doFilter(ChannelProcessingFilter.java:157)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.FilterChainProxy.doFilterInternal(FilterChainProxy.java:215)
at org.springframework.security.web.FilterChainProxy.doFilter(FilterChainProxy.java:178)
at org.springframework.web.filter.DelegatingFilterProxy.invokeDelegate(DelegatingFilterProxy.java:358)
at org.springframework.web.filter.DelegatingFilterProxy.doFilter(DelegatingFilterProxy.java:271)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166)
at org.springframework.boot.actuate.metrics.web.servlet.WebMvcMetricsFilter.doFilterInternal(WebMvcMetricsFilter.java:93)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:119)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166)
at org.springframework.boot.web.servlet.support.ErrorPageFilter.doFilter(ErrorPageFilter.java:126)
at org.springframework.boot.web.servlet.support.ErrorPageFilter.access$000(ErrorPageFilter.java:64)
at org.springframework.boot.web.servlet.support.ErrorPageFilter$1.doFilterInternal(ErrorPageFilter.java:101)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:119)
at org.springframework.boot.web.servlet.support.ErrorPageFilter.doFilter(ErrorPageFilter.java:119)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166)
at org.springframework.web.filter.CharacterEncodingFilter.doFilterInternal(CharacterEncodingFilter.java:201)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:119)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:103)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166)
at org.apache.catalina.core.StandardWrapperValve.invoke(StandardWrapperValve.java:202)
at org.apache.catalina.core.StandardContextValve.invoke(StandardContextValve.java:96)
at org.apache.catalina.authenticator.AuthenticatorBase.invoke(AuthenticatorBase.java:541)
at org.apache.catalina.core.StandardHostValve.invoke(StandardHostValve.java:139)
at org.apache.catalina.valves.ErrorReportValve.invoke(ErrorReportValve.java:92)
at org.apache.catalina.valves.AbstractAccessLogValve.invoke(AbstractAccessLogValve.java:690)
at org.apache.catalina.core.StandardEngineValve.invoke(StandardEngineValve.java:74)
at org.apache.catalina.connector.CoyoteAdapter.service(CoyoteAdapter.java:343)
at org.apache.coyote.http11.Http11Processor.service(Http11Processor.java:373)
at org.apache.coyote.AbstractProcessorLight.process(AbstractProcessorLight.java:65)
at org.apache.coyote.AbstractProtocol$ConnectionHandler.process(AbstractProtocol.java:868)
at org.apache.tomcat.util.net.NioEndpoint$SocketProcessor.doRun(NioEndpoint.java:1589)
at org.apache.tomcat.util.net.SocketProcessorBase.run(SocketProcessorBase.java:49)
at java.base/java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1128)
at java.base/java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:628)
at org.apache.tomcat.util.threads.TaskThread$WrappingRunnable.run(TaskThread.java:61)
at java.base/java.lang.Thread.run(Thread.java:834)
Caused by: com.sun.mail.smtp.SMTPAddressFailedException: 553 5.1.3 The recipient address <Francois> is not a valid RFC-5321 address. n1sm3229351pgn.94 - gsmtp
at com.sun.mail.smtp.SMTPTransport.rcptTo(SMTPTransport.java:1932)
... 182 more
QUIT
221 2.0.0 closing connection n1sm3229351pgn.94 - gsmtp
2021-02-17 17:06:43.360 ERROR 26113 --- [nio-443-exec-12] serWritePlatformServiceJpaRepositoryImpl : createUser: PlatformEmailSendException
org.apache.fineract.infrastructure.core.service.PlatformEmailSendException: org.springframework.mail.MailSendException: Failed messages: javax.mail.SendFailedException: Invalid Addresses;
nested exception is:
com.sun.mail.smtp.SMTPAddressFailedException: 553 5.1.3 The recipient address <Francois> is not a valid RFC-5321 address. n1sm3229351pgn.94 - gsmtp
; message exceptions (1) are:
Failed message 1: javax.mail.SendFailedException: Invalid Addresses;
nested exception is:
com.sun.mail.smtp.SMTPAddressFailedException: 553 5.1.3 The recipient address <Francois> is not a valid RFC-5321 address. n1sm3229351pgn.94 - gsmtp
at org.apache.fineract.infrastructure.core.service.GmailBackedPlatformEmailService.sendDefinedEmail(GmailBackedPlatformEmailService.java:95)
at org.apache.fineract.infrastructure.core.service.GmailBackedPlatformEmailService.sendToUserAccount(GmailBackedPlatformEmailService.java:54)
at org.apache.fineract.useradministration.domain.JpaUserDomainService.create(JpaUserDomainService.java:56)
at org.apache.fineract.useradministration.domain.JpaUserDomainService$$FastClassBySpringCGLIB$$6e9ae4ae.invoke(<generated>)
at org.springframework.cglib.proxy.MethodProxy.invoke(MethodProxy.java:218)
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.invokeJoinpoint(CglibAopProxy.java:771)
at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:163)
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.proceed(CglibAopProxy.java:749)
at org.springframework.transaction.interceptor.TransactionAspectSupport.invokeWithinTransaction(TransactionAspectSupport.java:367)
at org.springframework.transaction.interceptor.TransactionInterceptor.invoke(TransactionInterceptor.java:118)
at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:186)
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.proceed(CglibAopProxy.java:749)
at org.springframework.aop.framework.CglibAopProxy$DynamicAdvisedInterceptor.intercept(CglibAopProxy.java:691)
at org.apache.fineract.useradministration.domain.JpaUserDomainService$$EnhancerBySpringCGLIB$$dad28d42.create(<generated>)
at org.apache.fineract.useradministration.service.AppUserWritePlatformServiceJpaRepositoryImpl.createUser(AppUserWritePlatformServiceJpaRepositoryImpl.java:153)
at org.apache.fineract.useradministration.service.AppUserWritePlatformServiceJpaRepositoryImpl$$FastClassBySpringCGLIB$$fc767456.invoke(<generated>)
at org.springframework.cglib.proxy.MethodProxy.invoke(MethodProxy.java:218)
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.invokeJoinpoint(CglibAopProxy.java:771)
at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:163)
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.proceed(CglibAopProxy.java:749)
at org.springframework.transaction.interceptor.TransactionAspectSupport.invokeWithinTransaction(TransactionAspectSupport.java:367)
at org.springframework.transaction.interceptor.TransactionInterceptor.invoke(TransactionInterceptor.java:118)
at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:186)
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.proceed(CglibAopProxy.java:749)
at org.springframework.aop.framework.CglibAopProxy$DynamicAdvisedInterceptor.intercept(CglibAopProxy.java:691)
at org.apache.fineract.useradministration.service.AppUserWritePlatformServiceJpaRepositoryImpl$$EnhancerBySpringCGLIB$$44a8453a.createUser(<generated>)
at org.apache.fineract.useradministration.handler.CreateUserCommandHandler.processCommand(CreateUserCommandHandler.java:45)
at org.apache.fineract.useradministration.handler.CreateUserCommandHandler$$FastClassBySpringCGLIB$$d7a3d31.invoke(<generated>)
at org.springframework.cglib.proxy.MethodProxy.invoke(MethodProxy.java:218)
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.invokeJoinpoint(CglibAopProxy.java:771)
at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:163)
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.proceed(CglibAopProxy.java:749)
at org.springframework.transaction.interceptor.TransactionAspectSupport.invokeWithinTransaction(TransactionAspectSupport.java:367)
at org.springframework.transaction.interceptor.TransactionInterceptor.invoke(TransactionInterceptor.java:118)
at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:186)
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.proceed(CglibAopProxy.java:749)
at org.springframework.aop.framework.CglibAopProxy$DynamicAdvisedInterceptor.intercept(CglibAopProxy.java:691)
at org.apache.fineract.useradministration.handler.CreateUserCommandHandler$$EnhancerBySpringCGLIB$$fa5e80ab.processCommand(<generated>)
at org.apache.fineract.commands.service.SynchronousCommandProcessingService.processAndLogCommand(SynchronousCommandProcessingService.java:95)
at org.apache.fineract.commands.service.SynchronousCommandProcessingService$$FastClassBySpringCGLIB$$ec92d53f.invoke(<generated>)
at org.springframework.cglib.proxy.MethodProxy.invoke(MethodProxy.java:218)
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.invokeJoinpoint(CglibAopProxy.java:771)
at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:163)
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.proceed(CglibAopProxy.java:749)
at org.springframework.transaction.interceptor.TransactionAspectSupport.invokeWithinTransaction(TransactionAspectSupport.java:367)
at org.springframework.transaction.interceptor.TransactionInterceptor.invoke(TransactionInterceptor.java:118)
at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:186)
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.proceed(CglibAopProxy.java:749)
at org.springframework.aop.framework.CglibAopProxy$DynamicAdvisedInterceptor.intercept(CglibAopProxy.java:691)
at org.apache.fineract.commands.service.SynchronousCommandProcessingService$$EnhancerBySpringCGLIB$$3248c195.processAndLogCommand(<generated>)
at org.apache.fineract.commands.service.PortfolioCommandSourceWritePlatformServiceImpl.logCommandSource(PortfolioCommandSourceWritePlatformServiceImpl.java:99)
at org.apache.fineract.commands.service.PortfolioCommandSourceWritePlatformServiceImpl$$FastClassBySpringCGLIB$$31c15082.invoke(<generated>)
at org.springframework.cglib.proxy.MethodProxy.invoke(MethodProxy.java:218)
at org.springframework.aop.framework.CglibAopProxy$DynamicAdvisedInterceptor.intercept(CglibAopProxy.java:687)
at org.apache.fineract.commands.service.PortfolioCommandSourceWritePlatformServiceImpl$$EnhancerBySpringCGLIB$$8aedd53e.logCommandSource(<generated>)
at org.apache.fineract.useradministration.api.UsersApiResource.create(UsersApiResource.java:185)
at java.base/jdk.internal.reflect.NativeMethodAccessorImpl.invoke0(Native Method)
at java.base/jdk.internal.reflect.NativeMethodAccessorImpl.invoke(NativeMethodAccessorImpl.java:62)
at java.base/jdk.internal.reflect.DelegatingMethodAccessorImpl.invoke(DelegatingMethodAccessorImpl.java:43)
at java.base/java.lang.reflect.Method.invoke(Method.java:566)
at com.sun.jersey.spi.container.JavaMethodInvokerFactory$1.invoke(JavaMethodInvokerFactory.java:60)
at com.sun.jersey.server.impl.model.method.dispatch.AbstractResourceMethodDispatchProvider$TypeOutInvoker._dispatch(AbstractResourceMethodDispatchProvider.java:185)
at com.sun.jersey.server.impl.model.method.dispatch.ResourceJavaMethodDispatcher.dispatch(ResourceJavaMethodDispatcher.java:75)
at com.sun.jersey.server.impl.uri.rules.HttpMethodRule.accept(HttpMethodRule.java:302)
at com.sun.jersey.server.impl.uri.rules.ResourceClassRule.accept(ResourceClassRule.java:108)
at com.sun.jersey.server.impl.uri.rules.RightHandPathRule.accept(RightHandPathRule.java:147)
at com.sun.jersey.server.impl.uri.rules.RootResourceClassesRule.accept(RootResourceClassesRule.java:84)
at com.sun.jersey.server.impl.application.WebApplicationImpl._handleRequest(WebApplicationImpl.java:1542)
at com.sun.jersey.server.impl.application.WebApplicationImpl._handleRequest(WebApplicationImpl.java:1473)
at com.sun.jersey.server.impl.application.WebApplicationImpl.handleRequest(WebApplicationImpl.java:1419)
at com.sun.jersey.server.impl.application.WebApplicationImpl.handleRequest(WebApplicationImpl.java:1409)
at com.sun.jersey.spi.container.servlet.WebComponent.service(WebComponent.java:409)
at com.sun.jersey.spi.container.servlet.ServletContainer.service(ServletContainer.java:558)
at com.sun.jersey.spi.container.servlet.ServletContainer.service(ServletContainer.java:733)
at javax.servlet.http.HttpServlet.service(HttpServlet.java:733)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:231)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166)
at org.apache.tomcat.websocket.server.WsFilter.doFilter(WsFilter.java:53)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166)
at org.springframework.security.web.access.intercept.FilterSecurityInterceptor.invoke(FilterSecurityInterceptor.java:115)
at org.springframework.security.web.access.intercept.FilterSecurityInterceptor.doFilter(FilterSecurityInterceptor.java:90)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:320)
at org.springframework.security.web.access.intercept.FilterSecurityInterceptor.invoke(FilterSecurityInterceptor.java:115)
at org.springframework.security.web.access.intercept.FilterSecurityInterceptor.doFilter(FilterSecurityInterceptor.java:90)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.access.ExceptionTranslationFilter.doFilter(ExceptionTranslationFilter.java:118)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.authentication.AnonymousAuthenticationFilter.doFilter(AnonymousAuthenticationFilter.java:111)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.servletapi.SecurityContextHolderAwareRequestFilter.doFilter(SecurityContextHolderAwareRequestFilter.java:158)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.apache.fineract.infrastructure.security.filter.InsecureTwoFactorAuthenticationFilter.doFilter(InsecureTwoFactorAuthenticationFilter.java:75)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:113)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:113)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:113)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.context.SecurityContextPersistenceFilter.doFilter(SecurityContextPersistenceFilter.java:82)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.access.channel.ChannelProcessingFilter.doFilter(ChannelProcessingFilter.java:157)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.FilterChainProxy.doFilterInternal(FilterChainProxy.java:215)
at org.springframework.security.web.FilterChainProxy.doFilter(FilterChainProxy.java:186)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:320)
at org.springframework.security.web.access.intercept.FilterSecurityInterceptor.invoke(FilterSecurityInterceptor.java:126)
at org.springframework.security.web.access.intercept.FilterSecurityInterceptor.doFilter(FilterSecurityInterceptor.java:90)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.access.ExceptionTranslationFilter.doFilter(ExceptionTranslationFilter.java:118)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.authentication.AnonymousAuthenticationFilter.doFilter(AnonymousAuthenticationFilter.java:111)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.servletapi.SecurityContextHolderAwareRequestFilter.doFilter(SecurityContextHolderAwareRequestFilter.java:158)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.apache.fineract.infrastructure.security.filter.InsecureTwoFactorAuthenticationFilter.doFilter(InsecureTwoFactorAuthenticationFilter.java:75)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.header.HeaderWriterFilter.doHeadersAfter(HeaderWriterFilter.java:92)
at org.springframework.security.web.header.HeaderWriterFilter.doFilterInternal(HeaderWriterFilter.java:77)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:119)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.context.request.async.WebAsyncManagerIntegrationFilter.doFilterInternal(WebAsyncManagerIntegrationFilter.java:56)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:119)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.authentication.www.BasicAuthenticationFilter.doFilterInternal(BasicAuthenticationFilter.java:204)
at org.apache.fineract.infrastructure.security.filter.TenantAwareBasicAuthenticationFilter.doFilterInternal(TenantAwareBasicAuthenticationFilter.java:144)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:119)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.context.SecurityContextPersistenceFilter.doFilter(SecurityContextPersistenceFilter.java:105)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.access.channel.ChannelProcessingFilter.doFilter(ChannelProcessingFilter.java:157)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334)
at org.springframework.security.web.FilterChainProxy.doFilterInternal(FilterChainProxy.java:215)
at org.springframework.security.web.FilterChainProxy.doFilter(FilterChainProxy.java:178)
at org.springframework.web.filter.DelegatingFilterProxy.invokeDelegate(DelegatingFilterProxy.java:358)
at org.springframework.web.filter.DelegatingFilterProxy.doFilter(DelegatingFilterProxy.java:271)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166)
at org.springframework.boot.actuate.metrics.web.servlet.WebMvcMetricsFilter.doFilterInternal(WebMvcMetricsFilter.java:93)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:119)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166)
at org.springframework.boot.web.servlet.support.ErrorPageFilter.doFilter(ErrorPageFilter.java:126)
at org.springframework.boot.web.servlet.support.ErrorPageFilter.access$000(ErrorPageFilter.java:64)
at org.springframework.boot.web.servlet.support.ErrorPageFilter$1.doFilterInternal(ErrorPageFilter.java:101)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:119)
at org.springframework.boot.web.servlet.support.ErrorPageFilter.doFilter(ErrorPageFilter.java:119)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166)
at org.springframework.web.filter.CharacterEncodingFilter.doFilterInternal(CharacterEncodingFilter.java:201)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:119)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:103)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166)
at org.apache.catalina.core.StandardWrapperValve.invoke(StandardWrapperValve.java:202)
at org.apache.catalina.core.StandardContextValve.invoke(StandardContextValve.java:96)
at org.apache.catalina.authenticator.AuthenticatorBase.invoke(AuthenticatorBase.java:541)
at org.apache.catalina.core.StandardHostValve.invoke(StandardHostValve.java:139)
at org.apache.catalina.valves.ErrorReportValve.invoke(ErrorReportValve.java:92)
at org.apache.catalina.valves.AbstractAccessLogValve.invoke(AbstractAccessLogValve.java:690)
at org.apache.catalina.core.StandardEngineValve.invoke(StandardEngineValve.java:74)
at org.apache.catalina.connector.CoyoteAdapter.service(CoyoteAdapter.java:343)
at org.apache.coyote.http11.Http11Processor.service(Http11Processor.java:373)
at org.apache.coyote.AbstractProcessorLight.process(AbstractProcessorLight.java:65)
at org.apache.coyote.AbstractProtocol$ConnectionHandler.process(AbstractProtocol.java:868)
at org.apache.tomcat.util.net.NioEndpoint$SocketProcessor.doRun(NioEndpoint.java:1589)
at org.apache.tomcat.util.net.SocketProcessorBase.run(SocketProcessorBase.java:49)
at java.base/java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1128)
at java.base/java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:628)
at org.apache.tomcat.util.threads.TaskThread$WrappingRunnable.run(TaskThread.java:61)
at java.base/java.lang.Thread.run(Thread.java:834)
Caused by: org.springframework.mail.MailSendException: Failed messages: javax.mail.SendFailedException: Invalid Addresses;
nested exception is:
com.sun.mail.smtp.SMTPAddressFailedException: 553 5.1.3 The recipient address <Francois> is not a valid RFC-5321 address. n1sm3229351pgn.94 - gsmtp
at org.springframework.mail.javamail.JavaMailSenderImpl.doSend(JavaMailSenderImpl.java:491)
at org.springframework.mail.javamail.JavaMailSenderImpl.send(JavaMailSenderImpl.java:323)
at org.springframework.mail.javamail.JavaMailSenderImpl.send(JavaMailSenderImpl.java:312)
at org.apache.fineract.infrastructure.core.service.GmailBackedPlatformEmailService.sendDefinedEmail(GmailBackedPlatformEmailService.java:92)
... 177 common frames omitted
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] xurror commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
xurror commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-829493854
We've stagnated enough on this.
I'll merge this and we can resolve subsequent problems if they occur separately.
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan removed a comment on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan removed a comment on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-780775874
> @BLasan look at my closed PR #1625
Have you resolved the version conflicts? Email sending works fine
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on a change in pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on a change in pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#discussion_r570930004
##########
File path: fineract-provider/src/main/java/org/apache/fineract/infrastructure/core/service/GmailBackedPlatformEmailService.java
##########
@@ -61,6 +64,18 @@ public void sendDefinedEmail(EmailDetail emailDetails) {
final String authuser = smtpCredentialsData.getUsername();
final String authpwd = smtpCredentialsData.getPassword();
+ LOG.info("Use name: ", smtpCredentialsData.getUsername());
+ LOG.info("Use Password: ", smtpCredentialsData.getPassword());
Review comment:
@awasum Would you mind explaining the way those system configurations(smtp) were done?
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] vorburger commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
vorburger commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-793151717
@ptuomola @xurror is this good to merge?
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-774385179
> @BLasan
> before i even test this condition is likely to fail **String port = "465"; boolean useTLS = false;**
>
> please note that for both ports 465 and 587
> boolean useTLS = true; is required for these ports to send mail
>
> but for 587
> boolean setStartTLSRequired= true; must be added
> and for 465
> boolean setStartTLSRequired= true; should be removed
Yeah, those conditions are already added. Can we use smtp.gmail.com to send an email from a non-gmail address to a gmail address? "From" email address is not a gmail address. I checked it in mysql container.
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] francisguchie commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
francisguchie commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-780809541
@BLasan - have u corrected the issue of firstname being taken as the "to-email-address"
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on a change in pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on a change in pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#discussion_r579600551
##########
File path: fineract-provider/dependencies.gradle
##########
@@ -80,7 +80,8 @@ dependencies {
'org.webjars:webjars-locator-core',
'com.google.cloud.sql:mysql-socket-factory-connector-j-8:1.2.1',
- 'com.squareup.retrofit2:converter-gson'
+ 'com.squareup.retrofit2:converter-gson',
+ 'com.sun.activation:jakarta.activation:1.2.2'
Review comment:
I've tried these changes earlier. Didn't work for me. Let me try this by clearing the gradle dependencies first :)
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on a change in pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on a change in pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#discussion_r579602434
##########
File path: fineract-provider/dependencies.gradle
##########
@@ -80,7 +80,8 @@ dependencies {
'org.webjars:webjars-locator-core',
'com.google.cloud.sql:mysql-socket-factory-connector-j-8:1.2.1',
- 'com.squareup.retrofit2:converter-gson'
+ 'com.squareup.retrofit2:converter-gson',
+ 'com.sun.activation:jakarta.activation:1.2.2'
Review comment:
> Ok - what did not work when you tried it? At least it built fine for me, no issues with duplicates etc.
Would you mind taking a look at this PR too? https://github.com/apache/fineract/pull/1611
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on a change in pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on a change in pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#discussion_r578923764
##########
File path: fineract-provider/src/main/java/org/apache/fineract/infrastructure/configuration/service/ExternalServicesPropertiesReadPlatformServiceImpl.java
##########
@@ -87,8 +87,6 @@ public SMTPCredentialsData extractData(final ResultSet rs) throws SQLException,
password = value;
} else if (ExternalServicesConstants.SMTP_HOST.equalsIgnoreCase(name)) {
host = value;
- } else if (ExternalServicesConstants.SMTP_PORT.equalsIgnoreCase(name)) {
- port = value;
} else if (ExternalServicesConstants.SMTP_USE_TLS.equalsIgnoreCase(name)) {
Review comment:
To send gmails it requires either port 587 or 465. The port stored in database is 25.
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on a change in pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on a change in pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#discussion_r579119188
##########
File path: fineract-provider/dependencies.gradle
##########
@@ -80,7 +80,8 @@ dependencies {
'org.webjars:webjars-locator-core',
'com.google.cloud.sql:mysql-socket-factory-connector-j-8:1.2.1',
- 'com.squareup.retrofit2:converter-gson'
+ 'com.squareup.retrofit2:converter-gson',
+ 'com.sun.activation:jakarta.activation:1.2.2'
Review comment:
Yuh. Your approach is ok @francisguchie . But instead of excluding that path, @ptuomola suggested to an exclusion for this particular dependency. I tried by adding it. But didn't work.
```
implementation ('com.sun.activation:jakarta.activation:1.2.2') {
exclude group: 'jakarta.activation', module: 'jakarta.activation-api'
exclude group: 'javax.activation', module: 'javax.activation-api'
}
```
Am I missing something in here ? @ptuomola
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-778781557
@vorburger Please review
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] ptuomola commented on a change in pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
ptuomola commented on a change in pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#discussion_r579598849
##########
File path: fineract-provider/dependencies.gradle
##########
@@ -80,7 +80,8 @@ dependencies {
'org.webjars:webjars-locator-core',
'com.google.cloud.sql:mysql-socket-factory-connector-j-8:1.2.1',
- 'com.squareup.retrofit2:converter-gson'
+ 'com.squareup.retrofit2:converter-gson',
+ 'com.sun.activation:jakarta.activation:1.2.2'
Review comment:
That's not quite what I meant. See my commit da73689bf498905752c592cdabf1e24300142448 as an example - or the patch below. Works at least for me. And no need to add any exclusions to ClasspathDuplicates checker.
```
diff --git a/fineract-provider/dependencies.gradle b/fineract-provider/dependencies.gradle
index 4024ce12a..7a83a941c 100644
--- a/fineract-provider/dependencies.gradle
+++ b/fineract-provider/dependencies.gradle
@@ -68,9 +68,6 @@ dependencies {
'com.github.spullara.mustache.java:compiler',
'com.jayway.jsonpath:json-path',
- // JAX-B dependencies for JDK 9+
- 'jakarta.xml.bind:jakarta.xml.bind-api',
-
'org.dom4j:dom4j',
'javax.cache:cache-api',
@@ -83,6 +80,9 @@ dependencies {
'com.squareup.retrofit2:converter-gson',
'com.sun.activation:jakarta.activation:1.2.2'
)
+ implementation ('jakarta.xml.bind:jakarta.xml.bind-api') {
+ exclude group: 'jakarta.activation'
+ }
implementation ('org.apache.activemq:activemq-broker') {
exclude group: 'org.apache.geronimo.specs'
}
```
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on a change in pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on a change in pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#discussion_r579123309
##########
File path: fineract-provider/dependencies.gradle
##########
@@ -80,7 +80,8 @@ dependencies {
'org.webjars:webjars-locator-core',
'com.google.cloud.sql:mysql-socket-factory-connector-j-8:1.2.1',
- 'com.squareup.retrofit2:converter-gson'
+ 'com.squareup.retrofit2:converter-gson',
+ 'com.sun.activation:jakarta.activation:1.2.2'
Review comment:
> As I mentioned in my original comment, I'd suggest excluding the dependency brought in by jakarta-xml.bind-api and keeping this package intact. Otherwise you might end up with incompatible api and impl
```
implementation ('com.sun.activation:jakarta.activation:1.2.2') {
exclude group: 'jakarta.activation', module: 'jakarta.activation-api'
exclude group: 'javax.activation', module: 'javax.activation-api'
}
```
Can you verify this? Have I missed something?
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] francisguchie commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
francisguchie commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-771555604
I hope to look into tonight @BLasan
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan edited a comment on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan edited a comment on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-819568942
@xurror @ptuomola Please take a look :)
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] xurror commented on a change in pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
xurror commented on a change in pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#discussion_r607691730
##########
File path: fineract-provider/src/main/java/org/apache/fineract/infrastructure/configuration/service/ExternalServicesPropertiesReadPlatformServiceImpl.java
##########
@@ -87,8 +87,6 @@ public SMTPCredentialsData extractData(final ResultSet rs) throws SQLException,
password = value;
} else if (ExternalServicesConstants.SMTP_HOST.equalsIgnoreCase(name)) {
host = value;
- } else if (ExternalServicesConstants.SMTP_PORT.equalsIgnoreCase(name)) {
- port = value;
} else if (ExternalServicesConstants.SMTP_USE_TLS.equalsIgnoreCase(name)) {
Review comment:
@BLasan,, perhaps you want to set the port in the database as @ptuomola suggested.
##########
File path: fineract-provider/src/main/java/org/apache/fineract/infrastructure/core/service/GmailBackedPlatformEmailService.java
##########
@@ -55,31 +54,42 @@ public void sendToUserAccount(String organisationName, String contactName, Strin
@Override
public void sendDefinedEmail(EmailDetail emailDetails) {
- final Email email = new SimpleEmail();
final SMTPCredentialsData smtpCredentialsData = this.externalServicesReadPlatformService.getSMTPCredentials();
final String authuser = smtpCredentialsData.getUsername();
final String authpwd = smtpCredentialsData.getPassword();
- // Very Important, Don't use email.setAuthentication()
- email.setAuthenticator(new DefaultAuthenticator(authuser, authpwd));
- email.setDebug(false); // true if you want to debug
- email.setHostName(smtpCredentialsData.getHost());
+ JavaMailSenderImpl mailSender = new JavaMailSenderImpl();
+ mailSender.setHost(smtpCredentialsData.getHost()); // smtp.gmail.com
+ mailSender.setPort(Integer.parseInt(smtpCredentialsData.getPort())); // 587
+
+ // Important: Enable less secure app access for the gmail account used in the following authentication
+
+ mailSender.setUsername(authuser); // use valid gmail address
+ mailSender.setPassword(authpwd); // use password of the above gmail account
+
+ Properties props = mailSender.getJavaMailProperties();
+ props.put("mail.transport.protocol", "smtp");
+ props.put("mail.smtp.auth", "true");
+ props.put("mail.debug", "true");
try {
if (smtpCredentialsData.isUseTLS()) {
- // FINERACT-1070: NOT email.setSSLOnConnect(true); email.setSslSmtpPort(smtpCredentialsData.getPort());
- email.setStartTLSRequired(true);
+ if (smtpCredentialsData.getPort().equals("465")) {
Review comment:
If this is the case, maybe you can indicate with a comment why this check was done like this so it's clear for anyone going through the code in the future.
##########
File path: fineract-provider/src/main/java/org/apache/fineract/infrastructure/core/service/GmailBackedPlatformEmailService.java
##########
@@ -55,31 +54,42 @@ public void sendToUserAccount(String organisationName, String contactName, Strin
@Override
public void sendDefinedEmail(EmailDetail emailDetails) {
- final Email email = new SimpleEmail();
final SMTPCredentialsData smtpCredentialsData = this.externalServicesReadPlatformService.getSMTPCredentials();
final String authuser = smtpCredentialsData.getUsername();
final String authpwd = smtpCredentialsData.getPassword();
- // Very Important, Don't use email.setAuthentication()
- email.setAuthenticator(new DefaultAuthenticator(authuser, authpwd));
- email.setDebug(false); // true if you want to debug
- email.setHostName(smtpCredentialsData.getHost());
+ JavaMailSenderImpl mailSender = new JavaMailSenderImpl();
+ mailSender.setHost(smtpCredentialsData.getHost()); // smtp.gmail.com
Review comment:
Can you bring this to standard too as per @ptuomola suggestion?
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] francisguchie commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
francisguchie commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-780848793
i see the build failed due to
············'com.squareup.retrofit2:converter-gson', this comma
-···········//·'com.sun.activation:javax.activation:1.2.0'
+············//·'com.sun.activation:javax.activation:1.2.0'
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-782694719
> Looks like for the testRuntimeClasspath, the activation-api is brought in by spring-boot-starter-test. So you need to add the same exclusion there. After that, activation-api is gone and so are the duplicates.
> Looks like for the testRuntimeClasspath, the activation-api is brought in by spring-boot-starter-test. So you need to add the same exclusion there. After that, activation-api is gone and so are the duplicates.
Thanks. It worked :)
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-781370795
> @BLasan we need to add an exclusion in here ClasspathHellDuplicatesChecker.java
Can you add the change?
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] francisguchie commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
francisguchie commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-781364944
@BLasan we will have to add some ignore statements in the duplicates helper file. let me hunt for the section ( i think i did this before for pentaho) my challenge is my limited knowledge in java
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on a change in pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on a change in pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#discussion_r579119188
##########
File path: fineract-provider/dependencies.gradle
##########
@@ -80,7 +80,8 @@ dependencies {
'org.webjars:webjars-locator-core',
'com.google.cloud.sql:mysql-socket-factory-connector-j-8:1.2.1',
- 'com.squareup.retrofit2:converter-gson'
+ 'com.squareup.retrofit2:converter-gson',
+ 'com.sun.activation:jakarta.activation:1.2.2'
Review comment:
Yuh. Your approach is ok @francisguchie . But instead of excluding that path, @ptuomola suggested to an exclusion for this particular dependency. I tried by adding it. But didn't work.
```
implementation ('com.sun.activation:jakarta.activation:1.2.2') {
exclude group: 'jakarta.activation', module: 'jakarta.activation-api'
exclude group: 'javax.activation', module: 'javax.activation-api'
}
```
Am I missing something there ? @ptuomola
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-781375531
> Hi - instead of excluding this from the check, you really should look to exclude the duplicate inclusion of the same dependency. It only makes sense to remove it from the check if there is no other way to avoid it - eg if two different jars, which are both required, contain the same class. But that's not the case here, so excluding one of the dependencies would be the right way forward IMHO.
Tried to avoid having the duplicated jar. But if we could only add com/sun/activation/resources/ as a dependency we would be able to run the tests successfully. But I couldn't find a solution for that. If you could point me where the `com.sun.mail.javax.mail` dependency gets installed, I would be able to come with some good solution. I didn't find any imports for javax mail.
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on a change in pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on a change in pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#discussion_r579605624
##########
File path: fineract-provider/dependencies.gradle
##########
@@ -80,7 +80,8 @@ dependencies {
'org.webjars:webjars-locator-core',
'com.google.cloud.sql:mysql-socket-factory-connector-j-8:1.2.1',
- 'com.squareup.retrofit2:converter-gson'
+ 'com.squareup.retrofit2:converter-gson',
+ 'com.sun.activation:jakarta.activation:1.2.2'
Review comment:
@ptuomola Thanks. It worked !!!
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-782005936
> > > @BLasan we need to add an exclusion in here ClasspathHellDuplicatesChecker.java
> >
> >
> > Can you add the change?
> > @BLasan
> > [cff6378](https://github.com/apache/fineract/commit/cff63783cd77beb92cb92e5449ad77002e4ac6ad)
I'll add this. Thanks !!
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-782663640
> @BLasan looks like u have a classpath duplicat again
>
> ClasspathHellDuplicatesCheckRuleTest > testIfThereAreAnyDuplicatesOnTheClasspath() FAILED
> org.opentest4j.AssertionFailedError: 31 Classpath duplicates detected:
> javax/activation/CommandInfo$Beans$1.class
>
> ```
> javax/activation/DataContentHandlerFactory.class
>
> etc etc
> ```
@ptuomola Not worked for me. I forgot to remove the @francisguchie 's changes before start running the tests.
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on a change in pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on a change in pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#discussion_r570875151
##########
File path: fineract-provider/src/main/java/org/apache/fineract/infrastructure/core/service/GmailBackedPlatformEmailService.java
##########
@@ -61,6 +64,18 @@ public void sendDefinedEmail(EmailDetail emailDetails) {
final String authuser = smtpCredentialsData.getUsername();
final String authpwd = smtpCredentialsData.getPassword();
+ LOG.info("Use name: ", smtpCredentialsData.getUsername());
+ LOG.info("Use Password: ", smtpCredentialsData.getPassword());
Review comment:
@awasum @francisguchie I tested this by creating a new user. All configuration values were null. Those values are getting from mysql database.
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-786390444
@xurror Would you mind taking a look at this issue? I think this PR is not needed. If you know how to setup a smtp server properly to send emails via java, could you please try out that? As me and @francisguchie were not able to send emails by using out smtp configurations via java. As mentioned in the comments we were able to send emails via the linux commands
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] ptuomola commented on a change in pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
ptuomola commented on a change in pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#discussion_r579120921
##########
File path: fineract-provider/dependencies.gradle
##########
@@ -80,7 +80,8 @@ dependencies {
'org.webjars:webjars-locator-core',
'com.google.cloud.sql:mysql-socket-factory-connector-j-8:1.2.1',
- 'com.squareup.retrofit2:converter-gson'
+ 'com.squareup.retrofit2:converter-gson',
+ 'com.sun.activation:jakarta.activation:1.2.2'
Review comment:
As I mentioned in my original comment, I'd suggest excluding the dependency brought in by jakarta-xml.bind-api and keeping this package intact. Otherwise you might end up with incompatible api and impl
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] francisguchie edited a comment on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
francisguchie edited a comment on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-775899245
@BLasan this is what i have used ( with the actual emails of course )
**sudo nano /etc/ssmtp/ssmtp.conf**
root=valiedemail@gmail.com
mailhub=smtp.gmail.com:587
AuthUser=valiedemail@gmail.com
AuthPass=itspassword
UseTLS=YES
UseSTARTTLS=YES
rewriteDomain=gmail.com
**sudo nano /etc/ssmtp/revaliases**
root:valiedemail@gmail.com:smtp.gmail.com:587
I hope this helps to figure out if i have mixed up something somewhere
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-770349884
@vorburger @francisguchie Please review and try these changes. I haven't tried these changes in my machine. :)
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] francisguchie edited a comment on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
francisguchie edited a comment on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-775382127
> > @BLasan
> > I do not get this part clearly
> > **"Can you try using a gmail to send the email with port=465/587 and host=smtp.gmail.com ? Email domain used in default configurations is not a gmail"**
>
> When you configure email sending there's a configuration for "email from". In FINERACT they use an email which is not a gmail. (Belongs to another email domain). You have already set up the smtp configurations on your machine right? Could you please try by providing hard coded values for the following configurations.
>
> [email.setFrom()](https://github.com/apache/fineract/pull/1597/files#diff-ff180200f187360b5f3824c6656dcbb79f609f950ef0e90f25cf96df3c47ea96R81) - Replace this with a valid gmail you have (A duplicate one)
> [email.addTo()](https://github.com/apache/fineract/blob/bb00c18f274598a02337ad901b2021041c13ccc2/fineract-provider/src/main/java/org/apache/fineract/infrastructure/core/service/GmailBackedPlatformEmailService.java#L86) - Replace email.getAddress() with the email you are going to use for the above email.setFrom() configuration
> [email.setAuthenticator()](https://github.com/apache/fineract/blob/bb00c18f274598a02337ad901b2021041c13ccc2/fineract-provider/src/main/java/org/apache/fineract/infrastructure/core/service/GmailBackedPlatformEmailService.java#L65) - Replace with your gmail and the relevant password (Email you are going to use for the above two configurations)
cool
this is simpler for me to understand let me try this
**You have already set up the smtp configurations on your machine right?** YES i have
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] ptuomola commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
ptuomola commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-782689932
Looks like for the testRuntimeClasspath, the activation-api is brought in by spring-boot-starter-test. So you need to add the same exclusion there. After that, activation-api is gone and so are the duplicates.
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-798560104
> I've lost track here... is this one good to merge?
>
> @ptuomola would you like to re-review this? Has all of your feedback above been addressed, are you good with this as-is now?
>
> @francisguchie did you functionally test and independently verify this PR - does it solve [FINERACT-1070](https://issues.apache.org/jira/browse/FINERACT-1070)? (Just answer Yes or No.)
>
> @BLasan when we merge this we should "squash" your work of currently 8 commits as 1 single "squashed" clean commit (but don't do it now, because the open review comments would get lost).
>
> PS: See also [FINERACT-1335](https://issues.apache.org/jira/browse/FINERACT-1335) and [FINERACT-1270](https://issues.apache.org/jira/browse/FINERACT-1270), but let's not block this anymore, just separate ideas for new future PRs.
Sorry sir, my bad. Will keep this in mind. Thanks :)
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-781392847
> > Yuh, if we can avoid having the `jakarta.activation/jakarta.activation-api/1.2.2` dependency from javax.mail, we'll be able to resolve this
>
> @BLasan and yet without it we will be getting this error
> java.lang.noclassdeffounderror: com/sun/activation/registries/logsupport
>
> i have even tried com.sun.activation:jakarta.activation:1.2.0 as suggested [here] (https://stackoverflow.com/questions/58029104/cant-send-email-using-javamail-and-jdk-12) but i still got an error that 1.2.0 is not available
You can check the directories inside the jar file. If you are using intelliJ please check under` External Libraries` directory.
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan removed a comment on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan removed a comment on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-774140979
> > @awasum @francisguchie Default port and the host are 25 and smtp.gmail.com respectively. Is this correct? Gmail smtp server uses 587 & 465 ports to send email. Should we change these values accordingly?
>
> @BLasan
> originally, it was set as such , where fineract was ignoring the set port and i created an issue [here](https://issues.apache.org/jira/browse/FINERACT-1070)
>
> Even if use sets the following, MifosX will not send emails
> 1- Configure the server on which mifos is installed to be able to send Emails - One can do this by installing sSMTP on the server and testing email sending on the command line
>
> 2- if using a gmail address only ports 465 and 587 will work because port 25 is by default disabled on google servers This includes very many other VPS / Mail servers
>
> 3- Configure the port under the Email External Services Configuration
>
> one will still get the error below
>
> 03-Jul-2020 19:59:41.251 SEVERE [https-jsse-nio-443-exec-18]
> com.sun.jersey.spi.container.ContainerResponse.mapMappableContainerException
> The RuntimeException could not be mapped to a response, re-throwing to the HTTP container
>
> org.apache.fineract.infrastructure.core.service.PlatformEmailSendException:
> org.apache.commons.mail.EmailException:
> Sending the email to the following server failed : smtp.gmail.com:25
> at org.apache.fineract.infrastructure.core.service.GmailBackedPlatformEmailService.sendDefinedEmail(GmailBackedPlatformEmailService.java:81)
Yes, those configurations are read from mysql database. You can runthe command and get the output of the configurations for smtp. Default port is 25. I think we need to change that. Or else we need to hard code the value for now. Can you try by changing the port number in the following lines?
- https://github.com/apache/fineract/pull/1597/files#diff-ff180200f187360b5f3824c6656dcbb79f609f950ef0e90f25cf96df3c47ea96R87
- https://github.com/apache/fineract/pull/1597/files#diff-ff180200f187360b5f3824c6656dcbb79f609f950ef0e90f25cf96df3c47ea96R95
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on a change in pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on a change in pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#discussion_r570930004
##########
File path: fineract-provider/src/main/java/org/apache/fineract/infrastructure/core/service/GmailBackedPlatformEmailService.java
##########
@@ -61,6 +64,18 @@ public void sendDefinedEmail(EmailDetail emailDetails) {
final String authuser = smtpCredentialsData.getUsername();
final String authpwd = smtpCredentialsData.getPassword();
+ LOG.info("Use name: ", smtpCredentialsData.getUsername());
+ LOG.info("Use Password: ", smtpCredentialsData.getPassword());
Review comment:
@awasum Would you mind explaining the way those system configurations(smtp) were done?
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on a change in pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on a change in pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#discussion_r570875151
##########
File path: fineract-provider/src/main/java/org/apache/fineract/infrastructure/core/service/GmailBackedPlatformEmailService.java
##########
@@ -61,6 +64,18 @@ public void sendDefinedEmail(EmailDetail emailDetails) {
final String authuser = smtpCredentialsData.getUsername();
final String authpwd = smtpCredentialsData.getPassword();
+ LOG.info("Use name: ", smtpCredentialsData.getUsername());
+ LOG.info("Use Password: ", smtpCredentialsData.getPassword());
Review comment:
@awasum @francisguchie I tested this by creating a new user. All configuration values were null. Those values are getting from mysql database.
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on a change in pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on a change in pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#discussion_r579601036
##########
File path: fineract-provider/dependencies.gradle
##########
@@ -80,7 +80,8 @@ dependencies {
'org.webjars:webjars-locator-core',
'com.google.cloud.sql:mysql-socket-factory-connector-j-8:1.2.1',
- 'com.squareup.retrofit2:converter-gson'
+ 'com.squareup.retrofit2:converter-gson',
+ 'com.sun.activation:jakarta.activation:1.2.2'
Review comment:
Avoid installing jakarta-api. I'm trying again by clearing all caches. Will update you ASAP
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-828118820
Will close and open this again as @francisguchie suggested
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] francisguchie commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
francisguchie commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-775751993
@BLasan i still get the error below -- I am thinking there is a conflict between my smtp configuration and what FINERACT is sending
2021-02-09 08:00:42.553 ERROR 16465 --- [nio-443-exec-10] serWritePlatformServiceJpaRepositoryImpl : createUser: PlatformEmailSendException
org.apache.fineract.infrastructure.core.service.PlatformEmailSendException: org.apache.commons.mail.EmailException: Sending the email to the following server failed : smtp.gmail.com:587
at org.apache.fineract.infrastructure.core.service.GmailBackedPlatformEmailService.sendDefinedEmail(GmailBackedPlatformEmailService.java:108) ~[classes/:na]
at org.apache.fineract.infrastructure.core.service.GmailBackedPlatformEmailService.sendToUserAccount(GmailBackedPlatformEmailService.java:55) ~[classes/:na]
at org.apache.fineract.useradministration.domain.JpaUserDomainService.create(JpaUserDomainService.java:56) ~[classes/:na]
at org.apache.fineract.useradministration.domain.JpaUserDomainService$$FastClassBySpringCGLIB$$6e9ae4ae.invoke(<generated>) ~[classes/:na]
at org.springframework.cglib.proxy.MethodProxy.invoke(MethodProxy.java:218) ~[spring-core-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.invokeJoinpoint(CglibAopProxy.java:771) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:163) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.proceed(CglibAopProxy.java:749) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.springframework.transaction.interceptor.TransactionAspectSupport.invokeWithinTransaction(TransactionAspectSupport.java:367) ~[spring-tx-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.springframework.transaction.interceptor.TransactionInterceptor.invoke(TransactionInterceptor.java:118) ~[spring-tx-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:186) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.proceed(CglibAopProxy.java:749) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.springframework.aop.framework.CglibAopProxy$DynamicAdvisedInterceptor.intercept(CglibAopProxy.java:691) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.apache.fineract.useradministration.domain.JpaUserDomainService$$EnhancerBySpringCGLIB$$ac899949.create(<generated>) ~[classes/:na]
at org.apache.fineract.useradministration.service.AppUserWritePlatformServiceJpaRepositoryImpl.createUser(AppUserWritePlatformServiceJpaRepositoryImpl.java:153) ~[classes/:na]
at org.apache.fineract.useradministration.service.AppUserWritePlatformServiceJpaRepositoryImpl$$FastClassBySpringCGLIB$$fc767456.invoke(<generated>) ~[classes/:na]
at org.springframework.cglib.proxy.MethodProxy.invoke(MethodProxy.java:218) ~[spring-core-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.invokeJoinpoint(CglibAopProxy.java:771) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:163) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.proceed(CglibAopProxy.java:749) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.springframework.transaction.interceptor.TransactionAspectSupport.invokeWithinTransaction(TransactionAspectSupport.java:367) ~[spring-tx-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.springframework.transaction.interceptor.TransactionInterceptor.invoke(TransactionInterceptor.java:118) ~[spring-tx-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:186) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.proceed(CglibAopProxy.java:749) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.springframework.aop.framework.CglibAopProxy$DynamicAdvisedInterceptor.intercept(CglibAopProxy.java:691) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.apache.fineract.useradministration.service.AppUserWritePlatformServiceJpaRepositoryImpl$$EnhancerBySpringCGLIB$$165f5141.createUser(<generated>) ~[classes/:na]
at org.apache.fineract.useradministration.handler.CreateUserCommandHandler.processCommand(CreateUserCommandHandler.java:45) ~[classes/:na]
at org.apache.fineract.useradministration.handler.CreateUserCommandHandler$$FastClassBySpringCGLIB$$d7a3d31.invoke(<generated>) ~[classes/:na]
at org.springframework.cglib.proxy.MethodProxy.invoke(MethodProxy.java:218) ~[spring-core-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.invokeJoinpoint(CglibAopProxy.java:771) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:163) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.proceed(CglibAopProxy.java:749) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.springframework.transaction.interceptor.TransactionAspectSupport.invokeWithinTransaction(TransactionAspectSupport.java:367) ~[spring-tx-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.springframework.transaction.interceptor.TransactionInterceptor.invoke(TransactionInterceptor.java:118) ~[spring-tx-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:186) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.proceed(CglibAopProxy.java:749) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.springframework.aop.framework.CglibAopProxy$DynamicAdvisedInterceptor.intercept(CglibAopProxy.java:691) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.apache.fineract.useradministration.handler.CreateUserCommandHandler$$EnhancerBySpringCGLIB$$cc158cb2.processCommand(<generated>) ~[classes/:na]
at org.apache.fineract.commands.service.SynchronousCommandProcessingService.processAndLogCommand(SynchronousCommandProcessingService.java:95) ~[classes/:na]
at org.apache.fineract.commands.service.SynchronousCommandProcessingService$$FastClassBySpringCGLIB$$ec92d53f.invoke(<generated>) ~[classes/:na]
at org.springframework.cglib.proxy.MethodProxy.invoke(MethodProxy.java:218) ~[spring-core-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.invokeJoinpoint(CglibAopProxy.java:771) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:163) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.proceed(CglibAopProxy.java:749) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.springframework.transaction.interceptor.TransactionAspectSupport.invokeWithinTransaction(TransactionAspectSupport.java:367) ~[spring-tx-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.springframework.transaction.interceptor.TransactionInterceptor.invoke(TransactionInterceptor.java:118) ~[spring-tx-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:186) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.proceed(CglibAopProxy.java:749) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.springframework.aop.framework.CglibAopProxy$DynamicAdvisedInterceptor.intercept(CglibAopProxy.java:691) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.apache.fineract.commands.service.SynchronousCommandProcessingService$$EnhancerBySpringCGLIB$$3ffcd9c.processAndLogCommand(<generated>) ~[classes/:na]
at org.apache.fineract.commands.service.PortfolioCommandSourceWritePlatformServiceImpl.logCommandSource(PortfolioCommandSourceWritePlatformServiceImpl.java:99) ~[classes/:na]
at org.apache.fineract.commands.service.PortfolioCommandSourceWritePlatformServiceImpl$$FastClassBySpringCGLIB$$31c15082.invoke(<generated>) ~[classes/:na]
at org.springframework.cglib.proxy.MethodProxy.invoke(MethodProxy.java:218) ~[spring-core-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.springframework.aop.framework.CglibAopProxy$DynamicAdvisedInterceptor.intercept(CglibAopProxy.java:687) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.apache.fineract.commands.service.PortfolioCommandSourceWritePlatformServiceImpl$$EnhancerBySpringCGLIB$$5ca4e145.logCommandSource(<generated>) ~[classes/:na]
at org.apache.fineract.useradministration.api.UsersApiResource.create(UsersApiResource.java:185) ~[classes/:na]
at java.base/jdk.internal.reflect.NativeMethodAccessorImpl.invoke0(Native Method) ~[na:na]
at java.base/jdk.internal.reflect.NativeMethodAccessorImpl.invoke(NativeMethodAccessorImpl.java:62) ~[na:na]
at java.base/jdk.internal.reflect.DelegatingMethodAccessorImpl.invoke(DelegatingMethodAccessorImpl.java:43) ~[na:na]
at java.base/java.lang.reflect.Method.invoke(Method.java:566) ~[na:na]
at com.sun.jersey.spi.container.JavaMethodInvokerFactory$1.invoke(JavaMethodInvokerFactory.java:60) ~[jersey-server-1.19.4.jar:1.19.4]
at com.sun.jersey.server.impl.model.method.dispatch.AbstractResourceMethodDispatchProvider$TypeOutInvoker._dispatch(AbstractResourceMethodDispatchProvider.java:185) ~[jersey-server-1.19.4.jar:1.19.4]
at com.sun.jersey.server.impl.model.method.dispatch.ResourceJavaMethodDispatcher.dispatch(ResourceJavaMethodDispatcher.java:75) ~[jersey-server-1.19.4.jar:1.19.4]
at com.sun.jersey.server.impl.uri.rules.HttpMethodRule.accept(HttpMethodRule.java:302) ~[jersey-server-1.19.4.jar:1.19.4]
at com.sun.jersey.server.impl.uri.rules.ResourceClassRule.accept(ResourceClassRule.java:108) ~[jersey-server-1.19.4.jar:1.19.4]
at com.sun.jersey.server.impl.uri.rules.RightHandPathRule.accept(RightHandPathRule.java:147) ~[jersey-server-1.19.4.jar:1.19.4]
at com.sun.jersey.server.impl.uri.rules.RootResourceClassesRule.accept(RootResourceClassesRule.java:84) ~[jersey-server-1.19.4.jar:1.19.4]
at com.sun.jersey.server.impl.application.WebApplicationImpl._handleRequest(WebApplicationImpl.java:1542) ~[jersey-server-1.19.4.jar:1.19.4]
at com.sun.jersey.server.impl.application.WebApplicationImpl._handleRequest(WebApplicationImpl.java:1473) ~[jersey-server-1.19.4.jar:1.19.4]
at com.sun.jersey.server.impl.application.WebApplicationImpl.handleRequest(WebApplicationImpl.java:1419) ~[jersey-server-1.19.4.jar:1.19.4]
at com.sun.jersey.server.impl.application.WebApplicationImpl.handleRequest(WebApplicationImpl.java:1409) ~[jersey-server-1.19.4.jar:1.19.4]
at com.sun.jersey.spi.container.servlet.WebComponent.service(WebComponent.java:409) ~[jersey-servlet-1.19.4.jar:1.19.4]
at com.sun.jersey.spi.container.servlet.ServletContainer.service(ServletContainer.java:558) ~[jersey-servlet-1.19.4.jar:1.19.4]
at com.sun.jersey.spi.container.servlet.ServletContainer.service(ServletContainer.java:733) ~[jersey-servlet-1.19.4.jar:1.19.4]
at javax.servlet.http.HttpServlet.service(HttpServlet.java:733) ~[servlet-api.jar:4.0.FR]
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:231) ~[catalina.jar:9.0.37]
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166) ~[catalina.jar:9.0.37]
at org.apache.tomcat.websocket.server.WsFilter.doFilter(WsFilter.java:53) ~[tomcat-websocket.jar:9.0.37]
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193) ~[catalina.jar:9.0.37]
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166) ~[catalina.jar:9.0.37]
at org.springframework.security.web.access.intercept.FilterSecurityInterceptor.invoke(FilterSecurityInterceptor.java:115) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
at org.springframework.security.web.access.intercept.FilterSecurityInterceptor.doFilter(FilterSecurityInterceptor.java:90) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193) ~[catalina.jar:9.0.37]
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166) ~[catalina.jar:9.0.37]
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:320) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
at org.springframework.security.web.access.intercept.FilterSecurityInterceptor.invoke(FilterSecurityInterceptor.java:115) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
at org.springframework.security.web.access.intercept.FilterSecurityInterceptor.doFilter(FilterSecurityInterceptor.java:90) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
at org.springframework.security.web.access.ExceptionTranslationFilter.doFilter(ExceptionTranslationFilter.java:118) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
at org.springframework.security.web.authentication.AnonymousAuthenticationFilter.doFilter(AnonymousAuthenticationFilter.java:111) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
at org.springframework.security.web.servletapi.SecurityContextHolderAwareRequestFilter.doFilter(SecurityContextHolderAwareRequestFilter.java:158) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
at org.apache.fineract.infrastructure.security.filter.InsecureTwoFactorAuthenticationFilter.doFilter(InsecureTwoFactorAuthenticationFilter.java:75) ~[classes/:na]
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:113) ~[spring-web-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:113) ~[spring-web-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:113) ~[spring-web-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
at org.springframework.security.web.context.SecurityContextPersistenceFilter.doFilter(SecurityContextPersistenceFilter.java:82) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
at org.springframework.security.web.access.channel.ChannelProcessingFilter.doFilter(ChannelProcessingFilter.java:157) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
at org.springframework.security.web.FilterChainProxy.doFilterInternal(FilterChainProxy.java:215) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
at org.springframework.security.web.FilterChainProxy.doFilter(FilterChainProxy.java:186) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193) ~[catalina.jar:9.0.37]
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166) ~[catalina.jar:9.0.37]
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:320) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
at org.springframework.security.web.access.intercept.FilterSecurityInterceptor.invoke(FilterSecurityInterceptor.java:126) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
at org.springframework.security.web.access.intercept.FilterSecurityInterceptor.doFilter(FilterSecurityInterceptor.java:90) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
at org.springframework.security.web.access.ExceptionTranslationFilter.doFilter(ExceptionTranslationFilter.java:118) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
at org.springframework.security.web.authentication.AnonymousAuthenticationFilter.doFilter(AnonymousAuthenticationFilter.java:111) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
at org.springframework.security.web.servletapi.SecurityContextHolderAwareRequestFilter.doFilter(SecurityContextHolderAwareRequestFilter.java:158) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
at org.apache.fineract.infrastructure.security.filter.InsecureTwoFactorAuthenticationFilter.doFilter(InsecureTwoFactorAuthenticationFilter.java:75) ~[classes/:na]
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
at org.springframework.security.web.header.HeaderWriterFilter.doHeadersAfter(HeaderWriterFilter.java:92) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
at org.springframework.security.web.header.HeaderWriterFilter.doFilterInternal(HeaderWriterFilter.java:77) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:119) ~[spring-web-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
at org.springframework.security.web.context.request.async.WebAsyncManagerIntegrationFilter.doFilterInternal(WebAsyncManagerIntegrationFilter.java:56) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:119) ~[spring-web-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
at org.springframework.security.web.authentication.www.BasicAuthenticationFilter.doFilterInternal(BasicAuthenticationFilter.java:204) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
at org.apache.fineract.infrastructure.security.filter.TenantAwareBasicAuthenticationFilter.doFilterInternal(TenantAwareBasicAuthenticationFilter.java:144) ~[classes/:na]
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:119) ~[spring-web-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
at org.springframework.security.web.context.SecurityContextPersistenceFilter.doFilter(SecurityContextPersistenceFilter.java:105) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
at org.springframework.security.web.access.channel.ChannelProcessingFilter.doFilter(ChannelProcessingFilter.java:157) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
at org.springframework.security.web.FilterChainProxy.doFilterInternal(FilterChainProxy.java:215) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
at org.springframework.security.web.FilterChainProxy.doFilter(FilterChainProxy.java:178) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
at org.springframework.web.filter.DelegatingFilterProxy.invokeDelegate(DelegatingFilterProxy.java:358) ~[spring-web-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.springframework.web.filter.DelegatingFilterProxy.doFilter(DelegatingFilterProxy.java:271) ~[spring-web-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193) ~[catalina.jar:9.0.37]
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166) ~[catalina.jar:9.0.37]
at org.springframework.boot.actuate.metrics.web.servlet.WebMvcMetricsFilter.doFilterInternal(WebMvcMetricsFilter.java:93) ~[spring-boot-actuator-2.3.5.RELEASE.jar:2.3.5.RELEASE]
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:119) ~[spring-web-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193) ~[catalina.jar:9.0.37]
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166) ~[catalina.jar:9.0.37]
at org.springframework.boot.web.servlet.support.ErrorPageFilter.doFilter(ErrorPageFilter.java:126) ~[spring-boot-2.3.5.RELEASE.jar:2.3.5.RELEASE]
at org.springframework.boot.web.servlet.support.ErrorPageFilter.access$000(ErrorPageFilter.java:64) ~[spring-boot-2.3.5.RELEASE.jar:2.3.5.RELEASE]
at org.springframework.boot.web.servlet.support.ErrorPageFilter$1.doFilterInternal(ErrorPageFilter.java:101) ~[spring-boot-2.3.5.RELEASE.jar:2.3.5.RELEASE]
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:119) ~[spring-web-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.springframework.boot.web.servlet.support.ErrorPageFilter.doFilter(ErrorPageFilter.java:119) ~[spring-boot-2.3.5.RELEASE.jar:2.3.5.RELEASE]
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193) ~[catalina.jar:9.0.37]
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166) ~[catalina.jar:9.0.37]
at org.springframework.web.filter.CharacterEncodingFilter.doFilterInternal(CharacterEncodingFilter.java:201) ~[spring-web-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:119) ~[spring-web-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193) ~[catalina.jar:9.0.37]
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166) ~[catalina.jar:9.0.37]
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:103) ~[spring-web-5.2.10.RELEASE.jar:5.2.10.RELEASE]
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193) ~[catalina.jar:9.0.37]
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166) ~[catalina.jar:9.0.37]
at org.apache.catalina.core.StandardWrapperValve.invoke(StandardWrapperValve.java:202) ~[catalina.jar:9.0.37]
at org.apache.catalina.core.StandardContextValve.invoke(StandardContextValve.java:96) ~[catalina.jar:9.0.37]
at org.apache.catalina.authenticator.AuthenticatorBase.invoke(AuthenticatorBase.java:541) ~[catalina.jar:9.0.37]
at org.apache.catalina.core.StandardHostValve.invoke(StandardHostValve.java:139) ~[catalina.jar:9.0.37]
at org.apache.catalina.valves.ErrorReportValve.invoke(ErrorReportValve.java:92) ~[catalina.jar:9.0.37]
at org.apache.catalina.valves.AbstractAccessLogValve.invoke(AbstractAccessLogValve.java:690) ~[catalina.jar:9.0.37]
at org.apache.catalina.core.StandardEngineValve.invoke(StandardEngineValve.java:74) ~[catalina.jar:9.0.37]
at org.apache.catalina.connector.CoyoteAdapter.service(CoyoteAdapter.java:343) ~[catalina.jar:9.0.37]
at org.apache.coyote.http11.Http11Processor.service(Http11Processor.java:373) ~[tomcat-coyote.jar:9.0.37]
at org.apache.coyote.AbstractProcessorLight.process(AbstractProcessorLight.java:65) ~[tomcat-coyote.jar:9.0.37]
at org.apache.coyote.AbstractProtocol$ConnectionHandler.process(AbstractProtocol.java:868) ~[tomcat-coyote.jar:9.0.37]
at org.apache.tomcat.util.net.NioEndpoint$SocketProcessor.doRun(NioEndpoint.java:1589) ~[tomcat-coyote.jar:9.0.37]
at org.apache.tomcat.util.net.SocketProcessorBase.run(SocketProcessorBase.java:49) ~[tomcat-coyote.jar:9.0.37]
at java.base/java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1128) ~[na:na]
at java.base/java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:628) ~[na:na]
at org.apache.tomcat.util.threads.TaskThread$WrappingRunnable.run(TaskThread.java:61) ~[tomcat-util.jar:9.0.37]
at java.base/java.lang.Thread.run(Thread.java:834) ~[na:na]
Caused by: org.apache.commons.mail.EmailException: Sending the email to the following server failed : smtp.gmail.com:587
at org.apache.commons.mail.Email.sendMimeMessage(Email.java:1469) ~[commons-email-1.5.jar:1.5]
at org.apache.commons.mail.Email.send(Email.java:1496) ~[commons-email-1.5.jar:1.5]
at org.apache.fineract.infrastructure.core.service.GmailBackedPlatformEmailService.sendDefinedEmail(GmailBackedPlatformEmailService.java:106) ~[classes/:na]
... 177 common frames omitted
Caused by: java.lang.NoClassDefFoundError: com/sun/activation/registries/LogSupport
at javax.activation.MailcapCommandMap.<init>(MailcapCommandMap.java:149) ~[jakarta.activation-api-1.2.2.jar:1.2.2]
at javax.activation.CommandMap.getDefaultCommandMap(CommandMap.java:55) ~[jakarta.activation-api-1.2.2.jar:1.2.2]
at javax.activation.DataHandler.getCommandMap(DataHandler.java:137) ~[jakarta.activation-api-1.2.2.jar:1.2.2]
at javax.activation.DataHandler.getDataContentHandler(DataHandler.java:599) ~[jakarta.activation-api-1.2.2.jar:1.2.2]
at javax.activation.DataHandler.writeTo(DataHandler.java:299) ~[jakarta.activation-api-1.2.2.jar:1.2.2]
at javax.mail.internet.MimeUtility.getEncoding(MimeUtility.java:340) ~[javax.mail-1.6.2.jar:1.6.2]
at javax.mail.internet.MimeBodyPart.updateHeaders(MimeBodyPart.java:1575) ~[javax.mail-1.6.2.jar:1.6.2]
at javax.mail.internet.MimeMessage.updateHeaders(MimeMessage.java:2271) ~[javax.mail-1.6.2.jar:1.6.2]
at javax.mail.internet.MimeMessage.saveChanges(MimeMessage.java:2231) ~[javax.mail-1.6.2.jar:1.6.2]
at javax.mail.Transport.send(Transport.java:123) ~[javax.mail-1.6.2.jar:1.6.2]
at org.apache.commons.mail.Email.sendMimeMessage(Email.java:1459) ~[commons-email-1.5.jar:1.5]
... 179 common frames omitted
Caused by: java.lang.ClassNotFoundException: com.sun.activation.registries.LogSupport
at org.apache.catalina.loader.WebappClassLoaderBase.loadClass(WebappClassLoaderBase.java:1365) ~[catalina.jar:9.0.37]
at org.apache.catalina.loader.WebappClassLoaderBase.loadClass(WebappClassLoaderBase.java:1188) ~[catalina.jar:9.0.37]
... 190 common frames omitted
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-819568942
@xurror Please take a look :)
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] francisguchie commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
francisguchie commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-781373097
@ptuomola thanks
@BLasan my experience levels gives me some limitations
Its a +1 from me for @ptuomola 's suggestion
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-780824614
Build fails due to the `com.sun.activation:javax.activation:1.2.0` import
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-775280345
@vorburger @francisguchie Shall we try to resolve this issue?
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] ptuomola commented on a change in pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
ptuomola commented on a change in pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#discussion_r579598849
##########
File path: fineract-provider/dependencies.gradle
##########
@@ -80,7 +80,8 @@ dependencies {
'org.webjars:webjars-locator-core',
'com.google.cloud.sql:mysql-socket-factory-connector-j-8:1.2.1',
- 'com.squareup.retrofit2:converter-gson'
+ 'com.squareup.retrofit2:converter-gson',
+ 'com.sun.activation:jakarta.activation:1.2.2'
Review comment:
That's not quite what I meant. See my commit da73689bf498905752c592cdabf1e24300142448 as an example - or the patch below. Works at least for me.
diff --git a/fineract-provider/dependencies.gradle b/fineract-provider/dependencies.gradle
index 4024ce12a..7a83a941c 100644
--- a/fineract-provider/dependencies.gradle
+++ b/fineract-provider/dependencies.gradle
@@ -68,9 +68,6 @@ dependencies {
'com.github.spullara.mustache.java:compiler',
'com.jayway.jsonpath:json-path',
- // JAX-B dependencies for JDK 9+
- 'jakarta.xml.bind:jakarta.xml.bind-api',
-
'org.dom4j:dom4j',
'javax.cache:cache-api',
@@ -83,6 +80,9 @@ dependencies {
'com.squareup.retrofit2:converter-gson',
'com.sun.activation:jakarta.activation:1.2.2'
)
+ implementation ('jakarta.xml.bind:jakarta.xml.bind-api') {
+ exclude group: 'jakarta.activation'
+ }
implementation ('org.apache.activemq:activemq-broker') {
exclude group: 'org.apache.geronimo.specs'
}
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] francisguchie commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
francisguchie commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-780720900
@BLasan look at my closed PR https://github.com/apache/fineract/pull/1625
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-780801972
> @BLasan look at my closed PR #1625
You can try the latest changes by following the above steps I've mentioned. Fixed some minor issues :)
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] ptuomola commented on a change in pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
ptuomola commented on a change in pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#discussion_r579600661
##########
File path: fineract-provider/dependencies.gradle
##########
@@ -80,7 +80,8 @@ dependencies {
'org.webjars:webjars-locator-core',
'com.google.cloud.sql:mysql-socket-factory-connector-j-8:1.2.1',
- 'com.squareup.retrofit2:converter-gson'
+ 'com.squareup.retrofit2:converter-gson',
+ 'com.sun.activation:jakarta.activation:1.2.2'
Review comment:
Ok - what did not work when you tried it? At least it built fine for me, no issues with duplicates etc. W
##########
File path: fineract-provider/dependencies.gradle
##########
@@ -80,7 +80,8 @@ dependencies {
'org.webjars:webjars-locator-core',
'com.google.cloud.sql:mysql-socket-factory-connector-j-8:1.2.1',
- 'com.squareup.retrofit2:converter-gson'
+ 'com.squareup.retrofit2:converter-gson',
+ 'com.sun.activation:jakarta.activation:1.2.2'
Review comment:
Ok - what did not work when you tried it? At least it built fine for me, no issues with duplicates etc.
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-780821254
> @BLasan thanks am testing already , i saw it at line 87 after sending the question
So are we able to proceed with this solution?
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] francisguchie edited a comment on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
francisguchie edited a comment on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-775899245
@BLasan
this is what i have used ( with the actual emails of course )
**sudo nano /etc/ssmtp/ssmtp.conf**
---------------------------------------------------------------------------------------------
# root user email address
root=valiedemail@gmail.com
# The place where the mail goes. The actual machine name is required no
# MX records are consulted. Commonly mailhosts are named mail.domain.com
mailhub=smtp.gmail.com:587
AuthUser=valiedemail@gmail.com
AuthPass=itspassword
UseTLS=YES
UseSTARTTLS=YES
# Where will the mail seem to come from?
# rewriteDomain=
rewriteDomain=gmail.com
**sudo nano /etc/ssmtp/revaliases**
----------------------------------------------------------------------
# sSMTP aliases
#
# Format: local_account:outgoing_address:mailhub
#
# Example: root:your_login@your.domain:mailhub.your.domain[:port]
# where [:port] is an optional port number that defaults to 25.
root:valiedemail@gmail.com:smtp.gmail.com:587
I hope this helps to figure out if i have mixed up something somewhere
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-826273693
> @BLasan I have been waiting for a merge for this PR. I did my functional tests and the issues where solved. I have waited for your changes as requested by @ptuomola & @xurror and i followed the trail and saw the changes you made.
>
> To me the PR is ok AFAIK
Made the requested changes. @ptuomola @vorburger please take a look
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] francisguchie commented on a change in pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
francisguchie commented on a change in pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#discussion_r579657899
##########
File path: fineract-provider/dependencies.gradle
##########
@@ -80,7 +80,8 @@ dependencies {
'org.webjars:webjars-locator-core',
'com.google.cloud.sql:mysql-socket-factory-connector-j-8:1.2.1',
- 'com.squareup.retrofit2:converter-gson'
+ 'com.squareup.retrofit2:converter-gson',
+ 'com.sun.activation:jakarta.activation:1.2.2'
Review comment:
@ptuomola and @BLasan thanks, i am learning and becoming better from this great community
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] francisguchie commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
francisguchie commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-775382127
> > @BLasan
> > I do not get this part clearly
> > **"Can you try using a gmail to send the email with port=465/587 and host=smtp.gmail.com ? Email domain used in default configurations is not a gmail"**
>
> When you configure email sending there's a configuration for "email from". In FINERACT they use an email which is not a gmail. (Belongs to another email domain). You have already set up the smtp configurations on your machine right? Could you please try by providing hard coded values for the following configurations.
>
> [email.setFrom()](https://github.com/apache/fineract/pull/1597/files#diff-ff180200f187360b5f3824c6656dcbb79f609f950ef0e90f25cf96df3c47ea96R81) - Replace this with a valid gmail you have (A duplicate one)
> [email.addTo()](https://github.com/apache/fineract/blob/bb00c18f274598a02337ad901b2021041c13ccc2/fineract-provider/src/main/java/org/apache/fineract/infrastructure/core/service/GmailBackedPlatformEmailService.java#L86) - Replace email.getAddress() with the email you are going to use for the above email.setFrom() configuration
> [email.setAuthenticator()](https://github.com/apache/fineract/blob/bb00c18f274598a02337ad901b2021041c13ccc2/fineract-provider/src/main/java/org/apache/fineract/infrastructure/core/service/GmailBackedPlatformEmailService.java#L65) - Replace with your gmail and the relevant password (Email you are going to use for the above two configurations)
cool
this is simpler for me to understand let me try this
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan edited a comment on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan edited a comment on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-778779076
Hi @francisguchie . I was able to send the email successfully with these changes I've done. You need to replace `authuser` with a valid gmail and `authpwd` with the corresponding password. Also needs to replace the `fromEmail()` with the email you are going to use in the authentication method. Try port `587`. Don't forget to enable the less secure app access in the gmail account you'll be using for the authentication. (I've put some comments on those ponts)
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] francisguchie commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
francisguchie commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-782660629
@BLasan looks like u have a classpath duplicat again
ClasspathHellDuplicatesCheckRuleTest > testIfThereAreAnyDuplicatesOnTheClasspath() FAILED
org.opentest4j.AssertionFailedError: 31 Classpath duplicates detected:
javax/activation/CommandInfo$Beans$1.class
javax/activation/DataContentHandlerFactory.class
etc etc
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] francisguchie commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
francisguchie commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-780817562
@BLasan thanks am testing already , i saw it at line 87 after sending the question
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] francisguchie commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
francisguchie commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-775339388
@BLasan
I do not get this part clearly
**"Can you try using a gmail to send the email with port=465/587 and host=smtp.gmail.com ? Email domain used in default configurations is not a gmail"**
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan edited a comment on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan edited a comment on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-781223474
@vorburger Build fails due to the two dependencies jakarta and jakarta-api. `com.sun.activation:jakarta.activation:1.2.2 `will automatically add both the dependencies which leads to fail the fineract testing. `com.sun.mail.javax` will also import jakarta.activation-api. Would like to hear some suggestions for this PR sir
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on a change in pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on a change in pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#discussion_r613296434
##########
File path: fineract-provider/src/main/java/org/apache/fineract/infrastructure/core/service/GmailBackedPlatformEmailService.java
##########
@@ -55,31 +54,42 @@ public void sendToUserAccount(String organisationName, String contactName, Strin
@Override
public void sendDefinedEmail(EmailDetail emailDetails) {
- final Email email = new SimpleEmail();
final SMTPCredentialsData smtpCredentialsData = this.externalServicesReadPlatformService.getSMTPCredentials();
final String authuser = smtpCredentialsData.getUsername();
final String authpwd = smtpCredentialsData.getPassword();
- // Very Important, Don't use email.setAuthentication()
- email.setAuthenticator(new DefaultAuthenticator(authuser, authpwd));
- email.setDebug(false); // true if you want to debug
- email.setHostName(smtpCredentialsData.getHost());
+ JavaMailSenderImpl mailSender = new JavaMailSenderImpl();
+ mailSender.setHost(smtpCredentialsData.getHost()); // smtp.gmail.com
Review comment:
Is this necessary? As JavaMailSenderImpl is a class to send emails via the spring boot. (Not a customize one but you can have it after installing the necessary dependencies). I think this line is similar to this one `final Email email = new SimpleEmail();` (Needs to define this object as final)
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-778779076
Hi @francisguchie . I was able to send the email successfully for these changes I've done. You need to replace `authuser` with a valid gmail and `authpwd` with the corresponding password. Also needs to replace the `fromEmail()` with the email you are going to use in the authentication method. Try port `587`. Don't forget to enable the less secure app access in the gmail account you'll be using for the authentication. (I've put some comments on those ponts)
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] ptuomola commented on a change in pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
ptuomola commented on a change in pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#discussion_r579598849
##########
File path: fineract-provider/dependencies.gradle
##########
@@ -80,7 +80,8 @@ dependencies {
'org.webjars:webjars-locator-core',
'com.google.cloud.sql:mysql-socket-factory-connector-j-8:1.2.1',
- 'com.squareup.retrofit2:converter-gson'
+ 'com.squareup.retrofit2:converter-gson',
+ 'com.sun.activation:jakarta.activation:1.2.2'
Review comment:
That's not quite what I meant. See my commit da73689bf498905752c592cdabf1e24300142448 as an example - or the patch below. Works at least for me.
```
diff --git a/fineract-provider/dependencies.gradle b/fineract-provider/dependencies.gradle
index 4024ce12a..7a83a941c 100644
--- a/fineract-provider/dependencies.gradle
+++ b/fineract-provider/dependencies.gradle
@@ -68,9 +68,6 @@ dependencies {
'com.github.spullara.mustache.java:compiler',
'com.jayway.jsonpath:json-path',
- // JAX-B dependencies for JDK 9+
- 'jakarta.xml.bind:jakarta.xml.bind-api',
-
'org.dom4j:dom4j',
'javax.cache:cache-api',
@@ -83,6 +80,9 @@ dependencies {
'com.squareup.retrofit2:converter-gson',
'com.sun.activation:jakarta.activation:1.2.2'
)
+ implementation ('jakarta.xml.bind:jakarta.xml.bind-api') {
+ exclude group: 'jakarta.activation'
+ }
implementation ('org.apache.activemq:activemq-broker') {
exclude group: 'org.apache.geronimo.specs'
}
```
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] awasum commented on a change in pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
awasum commented on a change in pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#discussion_r570785195
##########
File path: fineract-provider/src/main/java/org/apache/fineract/infrastructure/core/service/GmailBackedPlatformEmailService.java
##########
@@ -61,6 +64,18 @@ public void sendDefinedEmail(EmailDetail emailDetails) {
final String authuser = smtpCredentialsData.getUsername();
final String authpwd = smtpCredentialsData.getPassword();
+ LOG.info("Use name: ", smtpCredentialsData.getUsername());
+ LOG.info("Use Password: ", smtpCredentialsData.getPassword());
Review comment:
Why are you logging password and some critical information ? You can do this in testing on your Dev environment and then remove these lines as critical information is being exposed here.
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] francisguchie commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
francisguchie commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-781430155
I have listed all the 31 classpath duplicates below
javax/activation/ActivationDataFlavor.class
--
javax/activation/CommandInfo$Beans$1.class
javax/activation/CommandInfo$Beans.class
javax/activation/CommandInfo.class
javax/activation/CommandMap.class
javax/activation/CommandObject.class
javax/activation/DataContentHandler.class
javax/activation/DataContentHandlerFactory.class
javax/activation/DataHandler$1.class
javax/activation/DataHandler.class
javax/activation/DataHandlerDataSource.class
javax/activation/DataSource.class
javax/activation/DataSourceDataContentHandler.class
javax/activation/FileDataSource.class
javax/activation/FileTypeMap.class
javax/activation/MailcapCommandMap$1.class
javax/activation/MailcapCommandMap.class
javax/activation/MimeType.class
javax/activation/MimeTypeParameterList.class
javax/activation/MimeTypeParseException.class
javax/activation/MimetypesFileTypeMap$1.class
javax/activation/MimetypesFileTypeMap.class
javax/activation/ObjectDataContentHandler.class
javax/activation/SecuritySupport$1.class
javax/activation/SecuritySupport$2.class
javax/activation/SecuritySupport$3.class
javax/activation/SecuritySupport$4.class
javax/activation/SecuritySupport$5.class
javax/activation/SecuritySupport.class
javax/activation/UnsupportedDataTypeException.class
javax/activation/URLDataSource.class
but also looking around the web i see someone comment that " You need the implementation jar file, not the API jar file. Use this." a discussion at https://stackoverflow.com/questions/58029104/cant-send-email-using-javamail-and-jdk-12
and they are suggesting to use this https://search.maven.org/artifact/com.sun.activation/javax.activation/1.2.0/jar
How can i avoid the activation for me the easiest would be to add it in the exclusion if these classes are being used somewhere before this line.
because it will be hard for me to find where these classes are being used before this point
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] francisguchie commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
francisguchie commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-827558403
eagerly waiting for the merge - @BLasan please squash
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-781376831
> > Hi - instead of excluding this from the check, you really should look to exclude the duplicate inclusion of the same dependency. It only makes sense to remove it from the check if there is no other way to avoid it - eg if two different jars, which are both required, contain the same class. But that's not the case here, so excluding one of the dependencies would be the right way forward IMHO.
>
> @BLasan and @ptuomola how can i find where this dependency is being called and how do we address removing it and yet still be able to utilize it in this class
>
> i have also noticed sometime that even the order of the dependencies in dependencies.gradle file matters alot
Yuh, if we can avoid having the `jakarta.activation/jakarta.activation-api/1.2.2` dependency from javax.mail, we'll be able to resolve this
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] francisguchie commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
francisguchie commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-775899245
@BLasan
this is what i have used ( with the actual emails of course )
**sudo nano /etc/ssmtp/ssmtp.conf**
========================================================
# root user email address
root=valiedemail@gmail.com
# The place where the mail goes. The actual machine name is required no
# MX records are consulted. Commonly mailhosts are named mail.domain.com
mailhub=smtp.gmail.com:587
AuthUser=valiedemail@gmail.com
AuthPass=itspassword
UseTLS=YES
UseSTARTTLS=YES
# Where will the mail seem to come from?
# rewriteDomain=
rewriteDomain=gmail.com
sudo nano /etc/ssmtp/revaliases
================================================================
# sSMTP aliases
#
# Format: local_account:outgoing_address:mailhub
#
# Example: root:your_login@your.domain:mailhub.your.domain[:port]
# where [:port] is an optional port number that defaults to 25.
root:valiedemail@gmail.com:smtp.gmail.com:587
I hope this helps to figure out if i have mixed up something somewhere
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on a change in pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on a change in pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#discussion_r579119188
##########
File path: fineract-provider/dependencies.gradle
##########
@@ -80,7 +80,8 @@ dependencies {
'org.webjars:webjars-locator-core',
'com.google.cloud.sql:mysql-socket-factory-connector-j-8:1.2.1',
- 'com.squareup.retrofit2:converter-gson'
+ 'com.squareup.retrofit2:converter-gson',
+ 'com.sun.activation:jakarta.activation:1.2.2'
Review comment:
Yuh. Your approach is ok @francisguchie . But instead of excluding that path, @ptuomola suggested to an exclusion for this particular dependency. I tried by adding it. But didn't work.
```
implementation ('com.sun.activation:jakarta.activation:1.2.2') {
exclude group: 'jakarta.activation', module: 'jakarta.activation-api'
exclude group: 'javax.activation', module: 'javax.activation-api'
}
```
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] francisguchie commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
francisguchie commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-810607697
@ptuomola ,
Have you had a chance to look at the changes I and @BLasan made?
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] ptuomola commented on a change in pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
ptuomola commented on a change in pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#discussion_r578933084
##########
File path: fineract-provider/src/main/java/org/apache/fineract/infrastructure/configuration/service/ExternalServicesPropertiesReadPlatformServiceImpl.java
##########
@@ -87,8 +87,6 @@ public SMTPCredentialsData extractData(final ResultSet rs) throws SQLException,
password = value;
} else if (ExternalServicesConstants.SMTP_HOST.equalsIgnoreCase(name)) {
host = value;
- } else if (ExternalServicesConstants.SMTP_PORT.equalsIgnoreCase(name)) {
- port = value;
} else if (ExternalServicesConstants.SMTP_USE_TLS.equalsIgnoreCase(name)) {
Review comment:
Hmm.. why would we not simply store the right port number in the database when using Gmail?
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] francisguchie commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
francisguchie commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-812931162
@ptuomola @xurror
Kindly have a look at this as @vorburger is asking if this is good to merge
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-781466422
> I have listed all the 31 classpath duplicates below
>
> ## javax/activation/ActivationDataFlavor.class
> javax/activation/CommandInfo$Beans$1.class
> javax/activation/CommandInfo$Beans.class
> javax/activation/CommandInfo.class
> javax/activation/CommandMap.class
> javax/activation/CommandObject.class
> javax/activation/DataContentHandler.class
> javax/activation/DataContentHandlerFactory.class
> javax/activation/DataHandler$1.class
> javax/activation/DataHandler.class
> javax/activation/DataHandlerDataSource.class
> javax/activation/DataSource.class
> javax/activation/DataSourceDataContentHandler.class
> javax/activation/FileDataSource.class
> javax/activation/FileTypeMap.class
> javax/activation/MailcapCommandMap$1.class
> javax/activation/MailcapCommandMap.class
> javax/activation/MimeType.class
> javax/activation/MimeTypeParameterList.class
> javax/activation/MimeTypeParseException.class
> javax/activation/MimetypesFileTypeMap$1.class
> javax/activation/MimetypesFileTypeMap.class
> javax/activation/ObjectDataContentHandler.class
> javax/activation/SecuritySupport$1.class
> javax/activation/SecuritySupport$2.class
> javax/activation/SecuritySupport$3.class
> javax/activation/SecuritySupport$4.class
> javax/activation/SecuritySupport$5.class
> javax/activation/SecuritySupport.class
> javax/activation/UnsupportedDataTypeException.class
> javax/activation/URLDataSource.class
>
> but also looking around the web i see someone comment that " You need the implementation jar file, not the API jar file. Use this." a discussion at https://stackoverflow.com/questions/58029104/cant-send-email-using-javamail-and-jdk-12
> and they are suggesting to use this https://search.maven.org/artifact/com.sun.activation/javax.activation/1.2.0/jar
>
> How can i avoid the activation for me the easiest would be to add it in the exclusion if these classes are being used somewhere before this line.
>
> because it will be hard for me to find where these classes are being used before this point
Yuh, that sounds good for me. If we can exclude installing javax-api or jakarta-api from javax.mail, I think we avoid having this issue. @vorburger @ptuomola Any suggestions on this?
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] francisguchie commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
francisguchie commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-826093300
@BLasan I have been waiting for a merge for this PR. I did my functional tests and the issues where solved. I have waited for your changes as requested by @ptuomola & @xurror and i followed the trail and saw the changes you made.
To me the PR is ok AFAIK
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan edited a comment on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan edited a comment on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-775372539
> @BLasan
> I do not get this part clearly
>
> **"Can you try using a gmail to send the email with port=465/587 and host=smtp.gmail.com ? Email domain used in default configurations is not a gmail"**
When you configure email sending there's a configuration for "email from". In FINERACT they use an email which is not a gmail. (Belongs to another email domain). You have already set up the smtp configurations on your machine right? Could you please try by providing hard coded values for the following configurations.
[email.setFrom()](https://github.com/apache/fineract/pull/1597/files#diff-ff180200f187360b5f3824c6656dcbb79f609f950ef0e90f25cf96df3c47ea96R81) - Replace this with a valid gmail you have (An optional one)
[email.addTo()](https://github.com/apache/fineract/blob/bb00c18f274598a02337ad901b2021041c13ccc2/fineract-provider/src/main/java/org/apache/fineract/infrastructure/core/service/GmailBackedPlatformEmailService.java#L86) - Replace email.getAddress() with the email you are going to use for the above email.setFrom() configuration
[email.setAuthenticator()](https://github.com/apache/fineract/blob/bb00c18f274598a02337ad901b2021041c13ccc2/fineract-provider/src/main/java/org/apache/fineract/infrastructure/core/service/GmailBackedPlatformEmailService.java#L65) - Replace with your gmail and the relevant password (Email you are going to use for the above two configurations)
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-827560363
Will squash the commits tonight. Thanks for the review @yemdjith @francis
On Tue, 27 Apr 2021, 17:44 Guchie, ***@***.***> wrote:
> eagerly waiting for the merge - @BLasan <https://github.com/BLasan>
> please squash
>
> —
> You are receiving this because you were mentioned.
> Reply to this email directly, view it on GitHub
> <https://github.com/apache/fineract/pull/1597#issuecomment-827558403>, or
> unsubscribe
> <https://github.com/notifications/unsubscribe-auth/AKI5NS7PP46CUKKDNDMTUODTK2TAXANCNFSM4WZ7QMLQ>
> .
>
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on a change in pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on a change in pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#discussion_r570796803
##########
File path: fineract-provider/src/main/java/org/apache/fineract/infrastructure/core/service/GmailBackedPlatformEmailService.java
##########
@@ -61,6 +64,18 @@ public void sendDefinedEmail(EmailDetail emailDetails) {
final String authuser = smtpCredentialsData.getUsername();
final String authpwd = smtpCredentialsData.getPassword();
+ LOG.info("Use name: ", smtpCredentialsData.getUsername());
+ LOG.info("Use Password: ", smtpCredentialsData.getPassword());
Review comment:
I haven't configured smtp on my pc. @francisguchie can use these logs to test the scenario in his own machine. This needs to be a draft PR. I'll change this into a draft one :)
##########
File path: fineract-provider/src/main/java/org/apache/fineract/infrastructure/core/service/GmailBackedPlatformEmailService.java
##########
@@ -61,6 +64,18 @@ public void sendDefinedEmail(EmailDetail emailDetails) {
final String authuser = smtpCredentialsData.getUsername();
final String authpwd = smtpCredentialsData.getPassword();
+ LOG.info("Use name: ", smtpCredentialsData.getUsername());
+ LOG.info("Use Password: ", smtpCredentialsData.getPassword());
Review comment:
Let me try this sir :)
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on a change in pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on a change in pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#discussion_r578928551
##########
File path: fineract-provider/dependencies.gradle
##########
@@ -80,7 +80,8 @@ dependencies {
'org.webjars:webjars-locator-core',
'com.google.cloud.sql:mysql-socket-factory-connector-j-8:1.2.1',
- 'com.squareup.retrofit2:converter-gson'
+ 'com.squareup.retrofit2:converter-gson',
+ 'com.sun.activation:jakarta.activation:1.2.2'
Review comment:
Great!! . I was in a dilemma on how that duplicate jakarta-api dependency gets installed. I'll try that. First I'll resolve this failing test cases.
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] francisguchie commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
francisguchie commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-781982315
@BLasan - I like the approach from @ptuomola as he explains. also please note that a user has the power to set the port they want here below
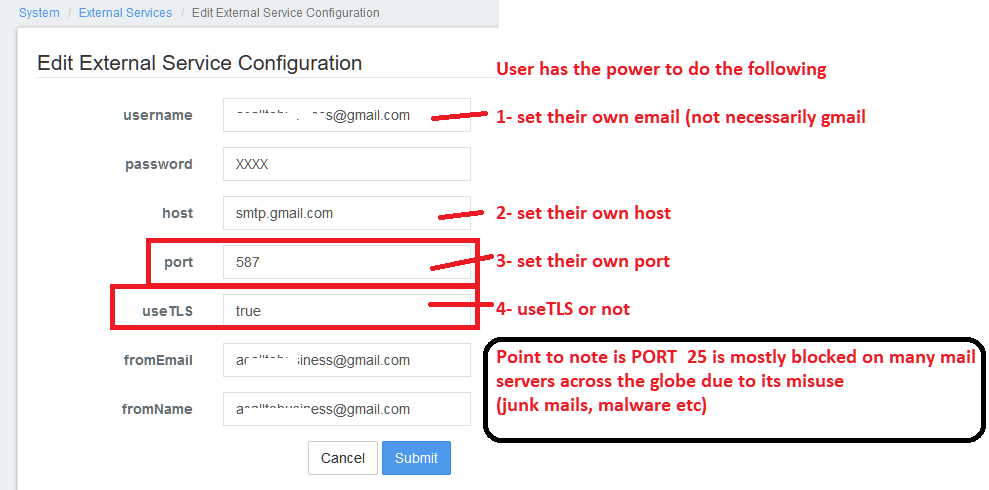
As @ptuomola says this information is saved in table c_external_service_properties as shown below
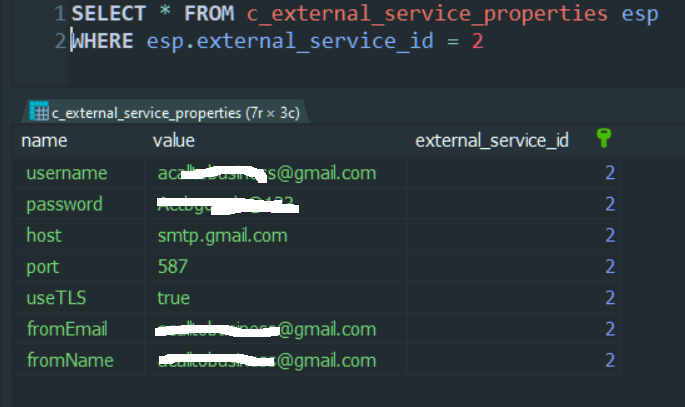
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-774149467
> > @awasum @francisguchie Default port and the host are 25 and smtp.gmail.com respectively. Is this correct? Gmail smtp server uses 587 & 465 ports to send email. Should we change these values accordingly?
>
> @BLasan
> originally, it was set as such , where fineract was ignoring the set port and i created an issue [here](https://issues.apache.org/jira/browse/FINERACT-1070)
>
> Even if use sets the following, MifosX will not send emails
> 1- Configure the server on which mifos is installed to be able to send Emails - One can do this by installing sSMTP on the server and testing email sending on the command line
>
> 2- if using a gmail address only ports 465 and 587 will work because port 25 is by default disabled on google servers This includes very many other VPS / Mail servers
>
> 3- Configure the port under the Email External Services Configuration
>
> one will still get the error below
>
> 03-Jul-2020 19:59:41.251 SEVERE [https-jsse-nio-443-exec-18]
> com.sun.jersey.spi.container.ContainerResponse.mapMappableContainerException
> The RuntimeException could not be mapped to a response, re-throwing to the HTTP container
>
> org.apache.fineract.infrastructure.core.service.PlatformEmailSendException:
> org.apache.commons.mail.EmailException:
> Sending the email to the following server failed : smtp.gmail.com:25
> at org.apache.fineract.infrastructure.core.service.GmailBackedPlatformEmailService.sendDefinedEmail(GmailBackedPlatformEmailService.java:81)
Change the default port to "465" and prevent loading from mysql. Now smtp.gmail.com will use port 465 for email sending. Can you please try again with these changes?
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] francisguchie commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
francisguchie commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-826093300
@BLasan I have been waiting for a merge for this PR. I did my functional tests and the issues where solved. I have waited for your changes as requested by @ptuomola & @xurror and i followed the trail and saw the changes you made.
To me the PR is ok AFAIK
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-775800162
> @BLasan i still get the error below -- I am thinking there is a conflict between my smtp configuration and what FINERACT is sending
>
> 2021-02-09 08:00:42.553 ERROR 16465 --- [nio-443-exec-10] serWritePlatformServiceJpaRepositoryImpl : createUser: PlatformEmailSendException
>
> org.apache.fineract.infrastructure.core.service.PlatformEmailSendException: org.apache.commons.mail.EmailException: Sending the email to the following server failed : smtp.gmail.com:587
> at org.apache.fineract.infrastructure.core.service.GmailBackedPlatformEmailService.sendDefinedEmail(GmailBackedPlatformEmailService.java:108) ~[classes/:na]
> at org.apache.fineract.infrastructure.core.service.GmailBackedPlatformEmailService.sendToUserAccount(GmailBackedPlatformEmailService.java:55) ~[classes/:na]
> at org.apache.fineract.useradministration.domain.JpaUserDomainService.create(JpaUserDomainService.java:56) ~[classes/:na]
> at org.apache.fineract.useradministration.domain.JpaUserDomainService$$FastClassBySpringCGLIB$$6e9ae4ae.invoke() ~[classes/:na]
> at org.springframework.cglib.proxy.MethodProxy.invoke(MethodProxy.java:218) ~[spring-core-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.invokeJoinpoint(CglibAopProxy.java:771) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:163) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.proceed(CglibAopProxy.java:749) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.springframework.transaction.interceptor.TransactionAspectSupport.invokeWithinTransaction(TransactionAspectSupport.java:367) ~[spring-tx-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.springframework.transaction.interceptor.TransactionInterceptor.invoke(TransactionInterceptor.java:118) ~[spring-tx-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:186) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.proceed(CglibAopProxy.java:749) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.springframework.aop.framework.CglibAopProxy$DynamicAdvisedInterceptor.intercept(CglibAopProxy.java:691) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.apache.fineract.useradministration.domain.JpaUserDomainService$$EnhancerBySpringCGLIB$$ac899949.create() ~[classes/:na]
> at org.apache.fineract.useradministration.service.AppUserWritePlatformServiceJpaRepositoryImpl.createUser(AppUserWritePlatformServiceJpaRepositoryImpl.java:153) ~[classes/:na]
> at org.apache.fineract.useradministration.service.AppUserWritePlatformServiceJpaRepositoryImpl$$FastClassBySpringCGLIB$$fc767456.invoke() ~[classes/:na]
> at org.springframework.cglib.proxy.MethodProxy.invoke(MethodProxy.java:218) ~[spring-core-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.invokeJoinpoint(CglibAopProxy.java:771) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:163) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.proceed(CglibAopProxy.java:749) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.springframework.transaction.interceptor.TransactionAspectSupport.invokeWithinTransaction(TransactionAspectSupport.java:367) ~[spring-tx-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.springframework.transaction.interceptor.TransactionInterceptor.invoke(TransactionInterceptor.java:118) ~[spring-tx-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:186) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.proceed(CglibAopProxy.java:749) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.springframework.aop.framework.CglibAopProxy$DynamicAdvisedInterceptor.intercept(CglibAopProxy.java:691) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.apache.fineract.useradministration.service.AppUserWritePlatformServiceJpaRepositoryImpl$$EnhancerBySpringCGLIB$$165f5141.createUser() ~[classes/:na]
> at org.apache.fineract.useradministration.handler.CreateUserCommandHandler.processCommand(CreateUserCommandHandler.java:45) ~[classes/:na]
> at org.apache.fineract.useradministration.handler.CreateUserCommandHandler$$FastClassBySpringCGLIB$$d7a3d31.invoke() ~[classes/:na]
> at org.springframework.cglib.proxy.MethodProxy.invoke(MethodProxy.java:218) ~[spring-core-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.invokeJoinpoint(CglibAopProxy.java:771) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:163) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.proceed(CglibAopProxy.java:749) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.springframework.transaction.interceptor.TransactionAspectSupport.invokeWithinTransaction(TransactionAspectSupport.java:367) ~[spring-tx-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.springframework.transaction.interceptor.TransactionInterceptor.invoke(TransactionInterceptor.java:118) ~[spring-tx-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:186) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.proceed(CglibAopProxy.java:749) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.springframework.aop.framework.CglibAopProxy$DynamicAdvisedInterceptor.intercept(CglibAopProxy.java:691) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.apache.fineract.useradministration.handler.CreateUserCommandHandler$$EnhancerBySpringCGLIB$$cc158cb2.processCommand() ~[classes/:na]
> at org.apache.fineract.commands.service.SynchronousCommandProcessingService.processAndLogCommand(SynchronousCommandProcessingService.java:95) ~[classes/:na]
> at org.apache.fineract.commands.service.SynchronousCommandProcessingService$$FastClassBySpringCGLIB$$ec92d53f.invoke() ~[classes/:na]
> at org.springframework.cglib.proxy.MethodProxy.invoke(MethodProxy.java:218) ~[spring-core-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.invokeJoinpoint(CglibAopProxy.java:771) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:163) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.proceed(CglibAopProxy.java:749) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.springframework.transaction.interceptor.TransactionAspectSupport.invokeWithinTransaction(TransactionAspectSupport.java:367) ~[spring-tx-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.springframework.transaction.interceptor.TransactionInterceptor.invoke(TransactionInterceptor.java:118) ~[spring-tx-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:186) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.springframework.aop.framework.CglibAopProxy$CglibMethodInvocation.proceed(CglibAopProxy.java:749) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.springframework.aop.framework.CglibAopProxy$DynamicAdvisedInterceptor.intercept(CglibAopProxy.java:691) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.apache.fineract.commands.service.SynchronousCommandProcessingService$$EnhancerBySpringCGLIB$$3ffcd9c.processAndLogCommand() ~[classes/:na]
> at org.apache.fineract.commands.service.PortfolioCommandSourceWritePlatformServiceImpl.logCommandSource(PortfolioCommandSourceWritePlatformServiceImpl.java:99) ~[classes/:na]
> at org.apache.fineract.commands.service.PortfolioCommandSourceWritePlatformServiceImpl$$FastClassBySpringCGLIB$$31c15082.invoke() ~[classes/:na]
> at org.springframework.cglib.proxy.MethodProxy.invoke(MethodProxy.java:218) ~[spring-core-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.springframework.aop.framework.CglibAopProxy$DynamicAdvisedInterceptor.intercept(CglibAopProxy.java:687) ~[spring-aop-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.apache.fineract.commands.service.PortfolioCommandSourceWritePlatformServiceImpl$$EnhancerBySpringCGLIB$$5ca4e145.logCommandSource() ~[classes/:na]
> at org.apache.fineract.useradministration.api.UsersApiResource.create(UsersApiResource.java:185) ~[classes/:na]
> at java.base/jdk.internal.reflect.NativeMethodAccessorImpl.invoke0(Native Method) ~[na:na]
> at java.base/jdk.internal.reflect.NativeMethodAccessorImpl.invoke(NativeMethodAccessorImpl.java:62) ~[na:na]
> at java.base/jdk.internal.reflect.DelegatingMethodAccessorImpl.invoke(DelegatingMethodAccessorImpl.java:43) ~[na:na]
> at java.base/java.lang.reflect.Method.invoke(Method.java:566) ~[na:na]
> at com.sun.jersey.spi.container.JavaMethodInvokerFactory$1.invoke(JavaMethodInvokerFactory.java:60) ~[jersey-server-1.19.4.jar:1.19.4]
> at com.sun.jersey.server.impl.model.method.dispatch.AbstractResourceMethodDispatchProvider$TypeOutInvoker._dispatch(AbstractResourceMethodDispatchProvider.java:185) ~[jersey-server-1.19.4.jar:1.19.4]
> at com.sun.jersey.server.impl.model.method.dispatch.ResourceJavaMethodDispatcher.dispatch(ResourceJavaMethodDispatcher.java:75) ~[jersey-server-1.19.4.jar:1.19.4]
> at com.sun.jersey.server.impl.uri.rules.HttpMethodRule.accept(HttpMethodRule.java:302) ~[jersey-server-1.19.4.jar:1.19.4]
> at com.sun.jersey.server.impl.uri.rules.ResourceClassRule.accept(ResourceClassRule.java:108) ~[jersey-server-1.19.4.jar:1.19.4]
> at com.sun.jersey.server.impl.uri.rules.RightHandPathRule.accept(RightHandPathRule.java:147) ~[jersey-server-1.19.4.jar:1.19.4]
> at com.sun.jersey.server.impl.uri.rules.RootResourceClassesRule.accept(RootResourceClassesRule.java:84) ~[jersey-server-1.19.4.jar:1.19.4]
> at com.sun.jersey.server.impl.application.WebApplicationImpl._handleRequest(WebApplicationImpl.java:1542) ~[jersey-server-1.19.4.jar:1.19.4]
> at com.sun.jersey.server.impl.application.WebApplicationImpl._handleRequest(WebApplicationImpl.java:1473) ~[jersey-server-1.19.4.jar:1.19.4]
> at com.sun.jersey.server.impl.application.WebApplicationImpl.handleRequest(WebApplicationImpl.java:1419) ~[jersey-server-1.19.4.jar:1.19.4]
> at com.sun.jersey.server.impl.application.WebApplicationImpl.handleRequest(WebApplicationImpl.java:1409) ~[jersey-server-1.19.4.jar:1.19.4]
> at com.sun.jersey.spi.container.servlet.WebComponent.service(WebComponent.java:409) ~[jersey-servlet-1.19.4.jar:1.19.4]
> at com.sun.jersey.spi.container.servlet.ServletContainer.service(ServletContainer.java:558) ~[jersey-servlet-1.19.4.jar:1.19.4]
> at com.sun.jersey.spi.container.servlet.ServletContainer.service(ServletContainer.java:733) ~[jersey-servlet-1.19.4.jar:1.19.4]
> at javax.servlet.http.HttpServlet.service(HttpServlet.java:733) ~[servlet-api.jar:4.0.FR]
> at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:231) ~[catalina.jar:9.0.37]
> at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166) ~[catalina.jar:9.0.37]
> at org.apache.tomcat.websocket.server.WsFilter.doFilter(WsFilter.java:53) ~[tomcat-websocket.jar:9.0.37]
> at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193) ~[catalina.jar:9.0.37]
> at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166) ~[catalina.jar:9.0.37]
> at org.springframework.security.web.access.intercept.FilterSecurityInterceptor.invoke(FilterSecurityInterceptor.java:115) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
> at org.springframework.security.web.access.intercept.FilterSecurityInterceptor.doFilter(FilterSecurityInterceptor.java:90) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
> at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193) ~[catalina.jar:9.0.37]
> at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166) ~[catalina.jar:9.0.37]
> at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:320) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
> at org.springframework.security.web.access.intercept.FilterSecurityInterceptor.invoke(FilterSecurityInterceptor.java:115) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
> at org.springframework.security.web.access.intercept.FilterSecurityInterceptor.doFilter(FilterSecurityInterceptor.java:90) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
> at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
> at org.springframework.security.web.access.ExceptionTranslationFilter.doFilter(ExceptionTranslationFilter.java:118) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
> at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
> at org.springframework.security.web.authentication.AnonymousAuthenticationFilter.doFilter(AnonymousAuthenticationFilter.java:111) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
> at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
> at org.springframework.security.web.servletapi.SecurityContextHolderAwareRequestFilter.doFilter(SecurityContextHolderAwareRequestFilter.java:158) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
> at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
> at org.apache.fineract.infrastructure.security.filter.InsecureTwoFactorAuthenticationFilter.doFilter(InsecureTwoFactorAuthenticationFilter.java:75) ~[classes/:na]
> at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
> at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:113) ~[spring-web-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
> at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:113) ~[spring-web-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
> at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:113) ~[spring-web-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
> at org.springframework.security.web.context.SecurityContextPersistenceFilter.doFilter(SecurityContextPersistenceFilter.java:82) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
> at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
> at org.springframework.security.web.access.channel.ChannelProcessingFilter.doFilter(ChannelProcessingFilter.java:157) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
> at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
> at org.springframework.security.web.FilterChainProxy.doFilterInternal(FilterChainProxy.java:215) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
> at org.springframework.security.web.FilterChainProxy.doFilter(FilterChainProxy.java:186) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
> at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193) ~[catalina.jar:9.0.37]
> at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166) ~[catalina.jar:9.0.37]
> at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:320) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
> at org.springframework.security.web.access.intercept.FilterSecurityInterceptor.invoke(FilterSecurityInterceptor.java:126) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
> at org.springframework.security.web.access.intercept.FilterSecurityInterceptor.doFilter(FilterSecurityInterceptor.java:90) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
> at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
> at org.springframework.security.web.access.ExceptionTranslationFilter.doFilter(ExceptionTranslationFilter.java:118) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
> at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
> at org.springframework.security.web.authentication.AnonymousAuthenticationFilter.doFilter(AnonymousAuthenticationFilter.java:111) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
> at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
> at org.springframework.security.web.servletapi.SecurityContextHolderAwareRequestFilter.doFilter(SecurityContextHolderAwareRequestFilter.java:158) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
> at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
> at org.apache.fineract.infrastructure.security.filter.InsecureTwoFactorAuthenticationFilter.doFilter(InsecureTwoFactorAuthenticationFilter.java:75) ~[classes/:na]
> at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
> at org.springframework.security.web.header.HeaderWriterFilter.doHeadersAfter(HeaderWriterFilter.java:92) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
> at org.springframework.security.web.header.HeaderWriterFilter.doFilterInternal(HeaderWriterFilter.java:77) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
> at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:119) ~[spring-web-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
> at org.springframework.security.web.context.request.async.WebAsyncManagerIntegrationFilter.doFilterInternal(WebAsyncManagerIntegrationFilter.java:56) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
> at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:119) ~[spring-web-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
> at org.springframework.security.web.authentication.www.BasicAuthenticationFilter.doFilterInternal(BasicAuthenticationFilter.java:204) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
> at org.apache.fineract.infrastructure.security.filter.TenantAwareBasicAuthenticationFilter.doFilterInternal(TenantAwareBasicAuthenticationFilter.java:144) ~[classes/:na]
> at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:119) ~[spring-web-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
> at org.springframework.security.web.context.SecurityContextPersistenceFilter.doFilter(SecurityContextPersistenceFilter.java:105) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
> at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
> at org.springframework.security.web.access.channel.ChannelProcessingFilter.doFilter(ChannelProcessingFilter.java:157) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
> at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:334) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
> at org.springframework.security.web.FilterChainProxy.doFilterInternal(FilterChainProxy.java:215) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
> at org.springframework.security.web.FilterChainProxy.doFilter(FilterChainProxy.java:178) ~[spring-security-web-5.3.5.RELEASE.jar:5.3.5.RELEASE]
> at org.springframework.web.filter.DelegatingFilterProxy.invokeDelegate(DelegatingFilterProxy.java:358) ~[spring-web-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.springframework.web.filter.DelegatingFilterProxy.doFilter(DelegatingFilterProxy.java:271) ~[spring-web-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193) ~[catalina.jar:9.0.37]
> at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166) ~[catalina.jar:9.0.37]
> at org.springframework.boot.actuate.metrics.web.servlet.WebMvcMetricsFilter.doFilterInternal(WebMvcMetricsFilter.java:93) ~[spring-boot-actuator-2.3.5.RELEASE.jar:2.3.5.RELEASE]
> at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:119) ~[spring-web-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193) ~[catalina.jar:9.0.37]
> at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166) ~[catalina.jar:9.0.37]
> at org.springframework.boot.web.servlet.support.ErrorPageFilter.doFilter(ErrorPageFilter.java:126) ~[spring-boot-2.3.5.RELEASE.jar:2.3.5.RELEASE]
> at org.springframework.boot.web.servlet.support.ErrorPageFilter.access$000(ErrorPageFilter.java:64) ~[spring-boot-2.3.5.RELEASE.jar:2.3.5.RELEASE]
> at org.springframework.boot.web.servlet.support.ErrorPageFilter$1.doFilterInternal(ErrorPageFilter.java:101) ~[spring-boot-2.3.5.RELEASE.jar:2.3.5.RELEASE]
> at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:119) ~[spring-web-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.springframework.boot.web.servlet.support.ErrorPageFilter.doFilter(ErrorPageFilter.java:119) ~[spring-boot-2.3.5.RELEASE.jar:2.3.5.RELEASE]
> at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193) ~[catalina.jar:9.0.37]
> at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166) ~[catalina.jar:9.0.37]
> at org.springframework.web.filter.CharacterEncodingFilter.doFilterInternal(CharacterEncodingFilter.java:201) ~[spring-web-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:119) ~[spring-web-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193) ~[catalina.jar:9.0.37]
> at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166) ~[catalina.jar:9.0.37]
> at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:103) ~[spring-web-5.2.10.RELEASE.jar:5.2.10.RELEASE]
> at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193) ~[catalina.jar:9.0.37]
> at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166) ~[catalina.jar:9.0.37]
> at org.apache.catalina.core.StandardWrapperValve.invoke(StandardWrapperValve.java:202) ~[catalina.jar:9.0.37]
> at org.apache.catalina.core.StandardContextValve.invoke(StandardContextValve.java:96) ~[catalina.jar:9.0.37]
> at org.apache.catalina.authenticator.AuthenticatorBase.invoke(AuthenticatorBase.java:541) ~[catalina.jar:9.0.37]
> at org.apache.catalina.core.StandardHostValve.invoke(StandardHostValve.java:139) ~[catalina.jar:9.0.37]
> at org.apache.catalina.valves.ErrorReportValve.invoke(ErrorReportValve.java:92) ~[catalina.jar:9.0.37]
> at org.apache.catalina.valves.AbstractAccessLogValve.invoke(AbstractAccessLogValve.java:690) ~[catalina.jar:9.0.37]
> at org.apache.catalina.core.StandardEngineValve.invoke(StandardEngineValve.java:74) ~[catalina.jar:9.0.37]
> at org.apache.catalina.connector.CoyoteAdapter.service(CoyoteAdapter.java:343) ~[catalina.jar:9.0.37]
> at org.apache.coyote.http11.Http11Processor.service(Http11Processor.java:373) ~[tomcat-coyote.jar:9.0.37]
> at org.apache.coyote.AbstractProcessorLight.process(AbstractProcessorLight.java:65) ~[tomcat-coyote.jar:9.0.37]
> at org.apache.coyote.AbstractProtocol$ConnectionHandler.process(AbstractProtocol.java:868) ~[tomcat-coyote.jar:9.0.37]
> at org.apache.tomcat.util.net.NioEndpoint$SocketProcessor.doRun(NioEndpoint.java:1589) ~[tomcat-coyote.jar:9.0.37]
> at org.apache.tomcat.util.net.SocketProcessorBase.run(SocketProcessorBase.java:49) ~[tomcat-coyote.jar:9.0.37]
> at java.base/java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1128) ~[na:na]
> at java.base/java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:628) ~[na:na]
> at org.apache.tomcat.util.threads.TaskThread$WrappingRunnable.run(TaskThread.java:61) ~[tomcat-util.jar:9.0.37]
> at java.base/java.lang.Thread.run(Thread.java:834) ~[na:na]
> Caused by: org.apache.commons.mail.EmailException: Sending the email to the following server failed : smtp.gmail.com:587
> at org.apache.commons.mail.Email.sendMimeMessage(Email.java:1469) ~[commons-email-1.5.jar:1.5]
> at org.apache.commons.mail.Email.send(Email.java:1496) ~[commons-email-1.5.jar:1.5]
> at org.apache.fineract.infrastructure.core.service.GmailBackedPlatformEmailService.sendDefinedEmail(GmailBackedPlatformEmailService.java:106) ~[classes/:na]
> ... 177 common frames omitted
> Caused by: java.lang.NoClassDefFoundError: com/sun/activation/registries/LogSupport
> at javax.activation.MailcapCommandMap.(MailcapCommandMap.java:149) ~[jakarta.activation-api-1.2.2.jar:1.2.2]
> at javax.activation.CommandMap.getDefaultCommandMap(CommandMap.java:55) ~[jakarta.activation-api-1.2.2.jar:1.2.2]
> at javax.activation.DataHandler.getCommandMap(DataHandler.java:137) ~[jakarta.activation-api-1.2.2.jar:1.2.2]
> at javax.activation.DataHandler.getDataContentHandler(DataHandler.java:599) ~[jakarta.activation-api-1.2.2.jar:1.2.2]
> at javax.activation.DataHandler.writeTo(DataHandler.java:299) ~[jakarta.activation-api-1.2.2.jar:1.2.2]
> at javax.mail.internet.MimeUtility.getEncoding(MimeUtility.java:340) ~[javax.mail-1.6.2.jar:1.6.2]
> at javax.mail.internet.MimeBodyPart.updateHeaders(MimeBodyPart.java:1575) ~[javax.mail-1.6.2.jar:1.6.2]
> at javax.mail.internet.MimeMessage.updateHeaders(MimeMessage.java:2271) ~[javax.mail-1.6.2.jar:1.6.2]
> at javax.mail.internet.MimeMessage.saveChanges(MimeMessage.java:2231) ~[javax.mail-1.6.2.jar:1.6.2]
> at javax.mail.Transport.send(Transport.java:123) ~[javax.mail-1.6.2.jar:1.6.2]
> at org.apache.commons.mail.Email.sendMimeMessage(Email.java:1459) ~[commons-email-1.5.jar:1.5]
> ... 179 common frames omitted
> Caused by: java.lang.ClassNotFoundException: com.sun.activation.registries.LogSupport
> at org.apache.catalina.loader.WebappClassLoaderBase.loadClass(WebappClassLoaderBase.java:1365) ~[catalina.jar:9.0.37]
> at org.apache.catalina.loader.WebappClassLoaderBase.loadClass(WebappClassLoaderBase.java:1188) ~[catalina.jar:9.0.37]
> ... 190 common frames omitted
I think we need to change the way we are sending the email. May be there's an incompatibility with the smtp server configurations you use. I'll do some more exploration on this :)
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] francisguchie commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
francisguchie commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-774112571
> @awasum @francisguchie Default port and the host are 25 and smtp.gmail.com respectively. Is this correct? Gmail smtp server uses 587 & 465 ports to send email. Should we change these values accordingly?
@BLasan
originally, it was set as such and i created an issue [here](https://issues.apache.org/jira/browse/FINERACT-1070)
**Even if use sets the following, MifosX will not send emails
1- Configure the server on which mifos is installed to be able to send Emails - One can do this by installing sSMTP on the server and testing email sending on the command line
2- if using a gmail address only ports 465 and 587 will work because port 25 is by default disabled on google servers This includes very many other VPS / Mail servers
3- Configure the port under the Email External Services Configuration
one will still get the error below
03-Jul-2020 19:59:41.251 SEVERE [https-jsse-nio-443-exec-18]
com.sun.jersey.spi.container.ContainerResponse.mapMappableContainerException
The RuntimeException could not be mapped to a response, re-throwing to the HTTP container
org.apache.fineract.infrastructure.core.service.PlatformEmailSendException:
org.apache.commons.mail.EmailException:
Sending the email to the following server failed : smtp.gmail.com:25
at org.apache.fineract.infrastructure.core.service.GmailBackedPlatformEmailService.sendDefinedEmail(GmailBackedPlatformEmailService.java:81)**
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-826273693
> @BLasan I have been waiting for a merge for this PR. I did my functional tests and the issues where solved. I have waited for your changes as requested by @ptuomola & @xurror and i followed the trail and saw the changes you made.
>
> To me the PR is ok AFAIK
Made the requested changes. @ptuomola @vorburger please take a look
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-774140979
> > @awasum @francisguchie Default port and the host are 25 and smtp.gmail.com respectively. Is this correct? Gmail smtp server uses 587 & 465 ports to send email. Should we change these values accordingly?
>
> @BLasan
> originally, it was set as such , where fineract was ignoring the set port and i created an issue [here](https://issues.apache.org/jira/browse/FINERACT-1070)
>
> Even if use sets the following, MifosX will not send emails
> 1- Configure the server on which mifos is installed to be able to send Emails - One can do this by installing sSMTP on the server and testing email sending on the command line
>
> 2- if using a gmail address only ports 465 and 587 will work because port 25 is by default disabled on google servers This includes very many other VPS / Mail servers
>
> 3- Configure the port under the Email External Services Configuration
>
> one will still get the error below
>
> 03-Jul-2020 19:59:41.251 SEVERE [https-jsse-nio-443-exec-18]
> com.sun.jersey.spi.container.ContainerResponse.mapMappableContainerException
> The RuntimeException could not be mapped to a response, re-throwing to the HTTP container
>
> org.apache.fineract.infrastructure.core.service.PlatformEmailSendException:
> org.apache.commons.mail.EmailException:
> Sending the email to the following server failed : smtp.gmail.com:25
> at org.apache.fineract.infrastructure.core.service.GmailBackedPlatformEmailService.sendDefinedEmail(GmailBackedPlatformEmailService.java:81)
Yes, those configurations are read from mysql database. You can runthe command and get the output of the configurations for smtp. Default port is 25. I think we need to change that. Or else we need to hard code the value for now. Can you try by changing the port number in the following lines?
- https://github.com/apache/fineract/pull/1597/files#diff-ff180200f187360b5f3824c6656dcbb79f609f950ef0e90f25cf96df3c47ea96R87
- https://github.com/apache/fineract/pull/1597/files#diff-ff180200f187360b5f3824c6656dcbb79f609f950ef0e90f25cf96df3c47ea96R95
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-775922740
> @BLasan this is what i have used ( with the actual emails of course )
>
> **sudo nano /etc/ssmtp/ssmtp.conf**
>
> root=[valiedemail@gmail.com](mailto:valiedemail@gmail.com)
> mailhub=smtp.gmail.com:587
> AuthUser=[valiedemail@gmail.com](mailto:valiedemail@gmail.com)
> AuthPass=itspassword
> UseTLS=YES
> UseSTARTTLS=YES
> rewriteDomain=gmail.com
>
> **sudo nano /etc/ssmtp/revaliases**
> root:[valiedemail@gmail.com](mailto:valiedemail@gmail.com):smtp.gmail.com:587
>
> I hope this helps to figure out if i have mixed up something somewhere
Thanks @francisguchie . I'll take a look and update you ASAP
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on a change in pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on a change in pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#discussion_r578925735
##########
File path: fineract-provider/src/main/java/org/apache/fineract/infrastructure/core/service/GmailBackedPlatformEmailService.java
##########
@@ -55,31 +54,42 @@ public void sendToUserAccount(String organisationName, String contactName, Strin
@Override
public void sendDefinedEmail(EmailDetail emailDetails) {
- final Email email = new SimpleEmail();
final SMTPCredentialsData smtpCredentialsData = this.externalServicesReadPlatformService.getSMTPCredentials();
final String authuser = smtpCredentialsData.getUsername();
final String authpwd = smtpCredentialsData.getPassword();
- // Very Important, Don't use email.setAuthentication()
- email.setAuthenticator(new DefaultAuthenticator(authuser, authpwd));
- email.setDebug(false); // true if you want to debug
- email.setHostName(smtpCredentialsData.getHost());
+ JavaMailSenderImpl mailSender = new JavaMailSenderImpl();
+ mailSender.setHost(smtpCredentialsData.getHost()); // smtp.gmail.com
+ mailSender.setPort(Integer.parseInt(smtpCredentialsData.getPort())); // 587
+
+ // Important: Enable less secure app access for the gmail account used in the following authentication
+
+ mailSender.setUsername(authuser); // use valid gmail address
+ mailSender.setPassword(authpwd); // use password of the above gmail account
+
+ Properties props = mailSender.getJavaMailProperties();
+ props.put("mail.transport.protocol", "smtp");
+ props.put("mail.smtp.auth", "true");
+ props.put("mail.debug", "true");
try {
if (smtpCredentialsData.isUseTLS()) {
- // FINERACT-1070: NOT email.setSSLOnConnect(true); email.setSslSmtpPort(smtpCredentialsData.getPort());
- email.setStartTLSRequired(true);
+ if (smtpCredentialsData.getPort().equals("465")) {
Review comment:
We read the port from smtpCredentials and just check the port number to make sure whether we want to enable ssl or not
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] francisguchie commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
francisguchie commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-781375409
> Hi - instead of excluding this from the check, you really should look to exclude the duplicate inclusion of the same dependency. It only makes sense to remove it from the check if there is no other way to avoid it - eg if two different jars, which are both required, contain the same class. But that's not the case here, so excluding one of the dependencies would be the right way forward IMHO.
@BLasan and @ptuomola how can i find where this dependency is being called and how do we address removing it and yet still be able to utilize it in this class
i have also noticed sometime that even the order of the dependencies in dependencies.gradle file matters alot
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] francisguchie commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
francisguchie commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-827945448
@BLasan the build failed due to some limits
Successfully built 8d6df843f0cf
Successfully tagged fineract_fineract-server:latest
ERROR: toomanyrequests: You have reached your pull rate limit. You may increase the limit by authenticating and upgrading: https://www.docker.com/increase-rate-limit
You might want to close and open the PR
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-775288693
> @BLasan
> before i even test this condition is likely to fail **String port = "465"; boolean useTLS = false;**
>
> please note that for both ports 465 and 587
> boolean useTLS = true; is required for these ports to send mail
>
> but for 587
> boolean setStartTLSRequired= true; must be added
> and for 465
> boolean setStartTLSRequired= true; should be removed
Can you try using a gmail to send the email with port=465/587 and host=smtp.gmail.com ? Email domain used in default configurations is not a gmail.
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] vorburger commented on a change in pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
vorburger commented on a change in pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#discussion_r593768189
##########
File path: fineract-provider/dependencies.gradle
##########
@@ -80,7 +80,8 @@ dependencies {
'org.webjars:webjars-locator-core',
'com.google.cloud.sql:mysql-socket-factory-connector-j-8:1.2.1',
- 'com.squareup.retrofit2:converter-gson'
+ 'com.squareup.retrofit2:converter-gson',
+ 'com.sun.activation:jakarta.activation:1.2.2'
Review comment:
@BLasan @ptuomola I've not looked closely here, but it seems to be that using `com.sun.activation:jakarta.activation:1.2.2` is confusing, because it is (probably, not verified) a very old Maven artifact which contains the exact same Java classes as the `jakarta.activation` and `javax.activation` dependencies... we should clean this up IMHO, but that could be done in a future PR.
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] francisguchie commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
francisguchie commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-793909487
@ptuomola this PR originated from my findings written in https://issues.apache.org/jira/browse/FINERACT-1070
@vorburger too after looking through my findings, he was in agreement
Somewhere along the line, we needed to get the real problem so @BLasan hard-coded the parameters and also logged some critical information for me to test on a local machine
We did some functional tests and all was well but the approach used by me even after removing the hard-codes was not of good standard if you can recall this section below
> **Yuh. Your approach is ok @francisguchie . But instead of excluding that path, @ptuomola suggested to an exclusion for this particular dependency.**
Ultimately the code was fine tuned and all was set for a merge after I did the functional test and the reviews from you and the rest about the code itself was done
Reason is because in the current build passwords cannot be sent to user via mail and more so any emails cannot be sent by FINERACT since there was an error in the code
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-782563402
@ptuomola Tried that too. But didn't work for me
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] francisguchie commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
francisguchie commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-774254305
@BLasan
before i even test this condition is likely to fail **String port = "465"; boolean useTLS = false;**
please note that for both ports 465 and 587
boolean useTLS = true; is required for these ports to send mail
but for 587
boolean setStartTLSRequired= true; must be added
and for 465
boolean setStartTLSRequired= true; should be removed
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-793329827
> Hi @vorburger - the last thing I'm aware of was the question from @BLasan on whether this PR is required - i.e. if you set the port and the server name correctly using the existing configuration parameters, will it not just work?
Didn't work for me and @francisguchie. We setup smtp configurations and tried sending emails via the terminal. It worked. But when it comes to the java code it said that cannot connect to the host `smtp.gmail.com`. I saw that someone had commented in the issue as mentioned in my previous comment. @francisguchie will give a proper clarification on this. Thanks !!
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] francisguchie commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
francisguchie commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-771555604
I hope to look into tonight @BLasan
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] BLasan commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
BLasan commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-781279319
```
ClasspathHellDuplicatesCheckRuleTest > testIfThereAreAnyDuplicatesOnTheClasspath() FAILED
org.opentest4j.AssertionFailedError: 31 Classpath duplicates detected:
javax/activation/CommandInfo$Beans$1.class
jar:file:/home/travis/.gradle/caches/modules-2/files-2.1/com.sun.activation/jakarta.activation/1.2.2/74548703f9851017ce2f556066659438019e7eb5/jakarta.activation-1.2.2.jar!/javax/activation/CommandInfo$Beans$1.class
jar:file:/home/travis/.gradle/caches/modules-2/files-2.1/jakarta.activation/jakarta.activation-api/1.2.2/99f53adba383cb1bf7c3862844488574b559621f/jakarta.activation-api-1.2.2.jar!/javax/activation/CommandInfo$Beans$1.class
javax/activation/DataContentHandlerFactory.class
jar:file:/home/travis/.gradle/caches/modules-2/files-2.1/com.sun.activation/jakarta.activation/1.2.2/74548703f9851017ce2f556066659438019e7eb5/jakarta.activation-1.2.2.jar!/javax/activation/DataContentHandlerFactory.class
jar:file:/home/travis/.gradle/caches/modules-2/files-2.1/jakarta.activation/jakarta.activation-api/1.2.2/99f53adba383cb1bf7c3862844488574b559621f/jakarta.activation-api-1.2.2.jar!/javax/activation/DataContentHandlerFactory.class
```
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] francisguchie commented on pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
francisguchie commented on pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#issuecomment-781990357
> > @BLasan we need to add an exclusion in here ClasspathHellDuplicatesChecker.java
>
> Can you add the change?
@BLasan
https://github.com/apache/fineract/pull/1627/commits/cff63783cd77beb92cb92e5449ad77002e4ac6ad
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [fineract] francisguchie commented on a change in pull request #1597: Add condition to start TLS (FINERACT-1070)
Posted by GitBox <gi...@apache.org>.
francisguchie commented on a change in pull request #1597:
URL: https://github.com/apache/fineract/pull/1597#discussion_r579081286
##########
File path: fineract-provider/src/main/java/org/apache/fineract/infrastructure/core/service/GmailBackedPlatformEmailService.java
##########
@@ -55,31 +54,42 @@ public void sendToUserAccount(String organisationName, String contactName, Strin
@Override
public void sendDefinedEmail(EmailDetail emailDetails) {
- final Email email = new SimpleEmail();
final SMTPCredentialsData smtpCredentialsData = this.externalServicesReadPlatformService.getSMTPCredentials();
final String authuser = smtpCredentialsData.getUsername();
final String authpwd = smtpCredentialsData.getPassword();
- // Very Important, Don't use email.setAuthentication()
- email.setAuthenticator(new DefaultAuthenticator(authuser, authpwd));
- email.setDebug(false); // true if you want to debug
- email.setHostName(smtpCredentialsData.getHost());
+ JavaMailSenderImpl mailSender = new JavaMailSenderImpl();
+ mailSender.setHost(smtpCredentialsData.getHost()); // smtp.gmail.com
+ mailSender.setPort(Integer.parseInt(smtpCredentialsData.getPort())); // 587
+
+ // Important: Enable less secure app access for the gmail account used in the following authentication
+
+ mailSender.setUsername(authuser); // use valid gmail address
+ mailSender.setPassword(authpwd); // use password of the above gmail account
+
+ Properties props = mailSender.getJavaMailProperties();
+ props.put("mail.transport.protocol", "smtp");
+ props.put("mail.smtp.auth", "true");
+ props.put("mail.debug", "true");
try {
if (smtpCredentialsData.isUseTLS()) {
- // FINERACT-1070: NOT email.setSSLOnConnect(true); email.setSslSmtpPort(smtpCredentialsData.getPort());
- email.setStartTLSRequired(true);
+ if (smtpCredentialsData.getPort().equals("465")) {
Review comment:
> Hmmm... We should not rely on a port number to decide whether to enable SSL. We should simply have a config parameter to turn it on or off. People can choose to run their mail servers on whatever port they feel like...
@ptuomola please note that
**useTLS = YES** is a condition that must be set for port 587 and 465 to successfully send mail (as i test it on linux 16 and 18) if one installs ssmpt server
**UseSTARTTLS=YES** if enabled with port 465 in use - mails will not go yet it is a must for port 587 for mails to go successfully
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org