You are viewing a plain text version of this content. The canonical link for it is here.
Posted to notifications@apisix.apache.org by GitBox <gi...@apache.org> on 2021/07/16 18:10:20 UTC
[GitHub] [apisix] cgodefroy92 opened a new issue #4616: Keycloak integration
cgodefroy92 opened a new issue #4616:
URL: https://github.com/apache/apisix/issues/4616
### Issue description
I am trying to use Keycloak behind an API gateway (Apache APISIX).
I use minikube to run Keycloak and my API gateway.
The gateway is working right and Keycloak too :
With Keycloak, I can use the different end-point (use the discovery end-point (http://127.0.0.1:7070/auth/realms/myrealm/.well-known/uma2-configuration), ask an access token and verify it).
With APISIX, and a simple route, I can join a backend microservice on my minikube.
(typically : http://127.0.0.1:80/greeting is served by the gateway which routes the request to the right backend microservice)
The problem occurs when I try to use the two tools together. I have used the Keycloak integration, in order to force the user to use a valid token when he is using a route served by the gateway.
In this case, when I use a valid bearer token (I get it and verify it with the end-point of keycloak), and I try to request the backend via the api gateway with the verified bearer token, I obtain systematically an "Invalid bearer token" exception.
{"error":"invalid_grant","error_description":"Invalid bearer token"}
I think the settings of the integration is well set because I am sure that te gateway call Keycloak to verify the token (when I voluntarily set a bad url to the discovery end-point in the authz-keycloak plugin, the error is clear and the gateway say that it can't join the discovery end-point).
Here are the keycloak I have used to get and verify the token :
Get token : http://127.0.0.1:7070/auth/realms/myrealm/protocol/openid-connect/token
Verify : http://127.0.0.1:7070/auth/realms/myrealm/protocol/openid-connect/token/introspect
I have seen some posts about problem when Keycloak is behind a reverse proxy, but I don't find a clear solution to my case.
Thanks for any help you can bring to me.
Regards
CG
### Environment
Request help without environment information will be ignored or closed.
* apisix version (cmd: `apisix version`): 2.7
* OS (cmd: `uname -a`): MacOs and Minikube
* apisix-dashboard version, if have: 2.7
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] tzssangglass commented on issue #4616: Keycloak integration
Posted by GitBox <gi...@apache.org>.
tzssangglass commented on issue #4616:
URL: https://github.com/apache/apisix/issues/4616#issuecomment-883444364
I think modifying apisix is useless because apisix is not responsible for generating or verifying tokens.
```
eyJhbGciOiJSUzI1NiIsInR5cCIgOiAiSldUIiwia2lkIiA6ICIzTmY5dzRyd2czYVdHcE5Lb3NSaXl6SHpSTkk0ZXdZOWRuNGlORHlHR1VzIn0.eyJleHAiOjE2MjY1Mjc2MjAsImlhdCI6MTYyNjUyNzMyMCwianRpIjoiYWU1M2RhYTAtNDNmNi00MTRkLWFjYTYtNDdhM2FhMzNkNjg5IiwiaXNzIjoiaHR0cDovLzM0Ljc5LjMyLjExOTo4MDgwL2F1dGgvcmVhbG1zL215cmVhbG0iLCJhdWQiOiJhY2NvdW50Iiwic3ViIjoiMGE0YTMxMjItNjQ5Ni00MWM2LTg0YWQtNGJmYTU1NmY4YjFmIiwidHlwIjoiQmVhcmVyIiwiYXpwIjoiYXBpc2l4Iiwic2Vzc2lvbl9zdGF0ZSI6Ijg5Y2NjMTc5LTEyMGQtNGQ1OS05Njk3LTk1OWRiYTA4NzM1ZCIsImFjciI6IjEiLCJyZWFsbV9hY2Nlc3MiOnsicm9sZXMiOlsiZGVmYXVsdC1yb2xlcy1teXJlYWxtIiwib2ZmbGluZV9hY2Nlc3MiLCJ1bWFfYXV0aG9yaXphdGlvbiJdfSwicmVzb3VyY2VfYWNjZXNzIjp7ImFjY291bnQiOnsicm9sZXMiOlsibWFuYWdlLWFjY291bnQiLCJtYW5hZ2UtYWNjb3VudC1saW5rcyIsInZpZXctcHJvZmlsZSJdfX0sInNjb3BlIjoiZW1haWwgcHJvZmlsZSIsImVtYWlsX3ZlcmlmaWVkIjpmYWxzZSwicHJlZmVycmVkX3VzZXJuYW1lIjoidXNlciJ9.NGFg-PQQY1aLf5NvOG28xOLMfD8BxInA4XUlmWXlhf4k2TmT3_aAT0OZAPhRt6hPJnxpdPLX74CKjw8hy-IaRfTuc-YEDyz6od5jYQKaPOjaQ_Xl4YZLpbLnB4jRkjH1Z7WoaAxoRoss5CCWfcBmFZ
WxkNS_MPEYDPVQEU98jD2EanKmJgoOk4n3tX-yyq6LdG2TbzshpJBXxWMHreWczxzgpPQ4NUMbfTcW1d0Wy_kXRcqEOpHtzzx7EH13_DXCWpC9pL51rA5OuFbOI3klVItmTLeJb-fTFJuAlUl3s3YkX_8L-AsvGXI6ZzUfzxPhp4XzOGS7vdGsN_TxJxUyMA
```
is a jwt, the decoded payload is
```
{
"exp": 1626527620,
"iat": 1626527320,
"jti": "ae53daa0-43f6-414d-aca6-47a3aa33d689",
"iss": "http://34.79.32.119:8080/auth/realms/myrealm",
"aud": "account",
"sub": "0a4a3122-6496-41c6-84ad-4bfa556f8b1f",
"typ": "Bearer",
"azp": "apisix",
"session_state": "89ccc179-120d-4d59-9697-959dba08735d",
"acr": "1",
"realm_access": {
"roles": [
"default-roles-myrealm",
"offline_access",
"uma_authorization"
]
},
"resource_access": {
"account": {
"roles": [
"manage-account",
"manage-account-links",
"view-profile"
]
}
},
"scope": "email profile",
"email_verified": false,
"preferred_username": "user"
}
```
obviously, `34.79.32.119` was constructed when the jwt was generated, so `34.79.32.119` should also be used as the ip when verifying. or is there any way to use `10.0.11.181` when generating jwt.
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] tzssangglass commented on issue #4616: Keycloak integration
Posted by GitBox <gi...@apache.org>.
tzssangglass commented on issue #4616:
URL: https://github.com/apache/apisix/issues/4616#issuecomment-882711876
@cgodefroy92 can you adjust the log level to debug and look at the log output here https://github.com/apache/apisix/blob/8693756470dca8228aa1a5b83ee3acc3603ed5f5/apisix/plugins/authz-keycloak.lua#L656-L669
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] cgodefroy92 edited a comment on issue #4616: Keycloak integration
Posted by GitBox <gi...@apache.org>.
cgodefroy92 edited a comment on issue #4616:
URL: https://github.com/apache/apisix/issues/4616#issuecomment-883477444
Thanks for your help. I understand that the IPs should be the same in order to make the Keycloak authentication with the jwt token works.
However I don't understand how to to do that. The only way I have found for the moment is by configuring the public IP of the Keycloak service in the APISIX route for the discovery end-point of the authz-keycloak plugin. I think it is not a good practice. I would prefer the request for the discovery plugin stay inside kubernetess.
In the other side, I don't know how to ask Keycloak a jwt token on the public ip of keycloak and force keycloak to return a jwt
payload with the internal IP of the keycloak server in the iis field value.
To fix the idea, here is my architecture :

--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] cgodefroy92 commented on issue #4616: Keycloak integration
Posted by GitBox <gi...@apache.org>.
cgodefroy92 commented on issue #4616:
URL: https://github.com/apache/apisix/issues/4616#issuecomment-882735687
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] cgodefroy92 commented on issue #4616: Keycloak integration
Posted by GitBox <gi...@apache.org>.
cgodefroy92 commented on issue #4616:
URL: https://github.com/apache/apisix/issues/4616#issuecomment-883113861
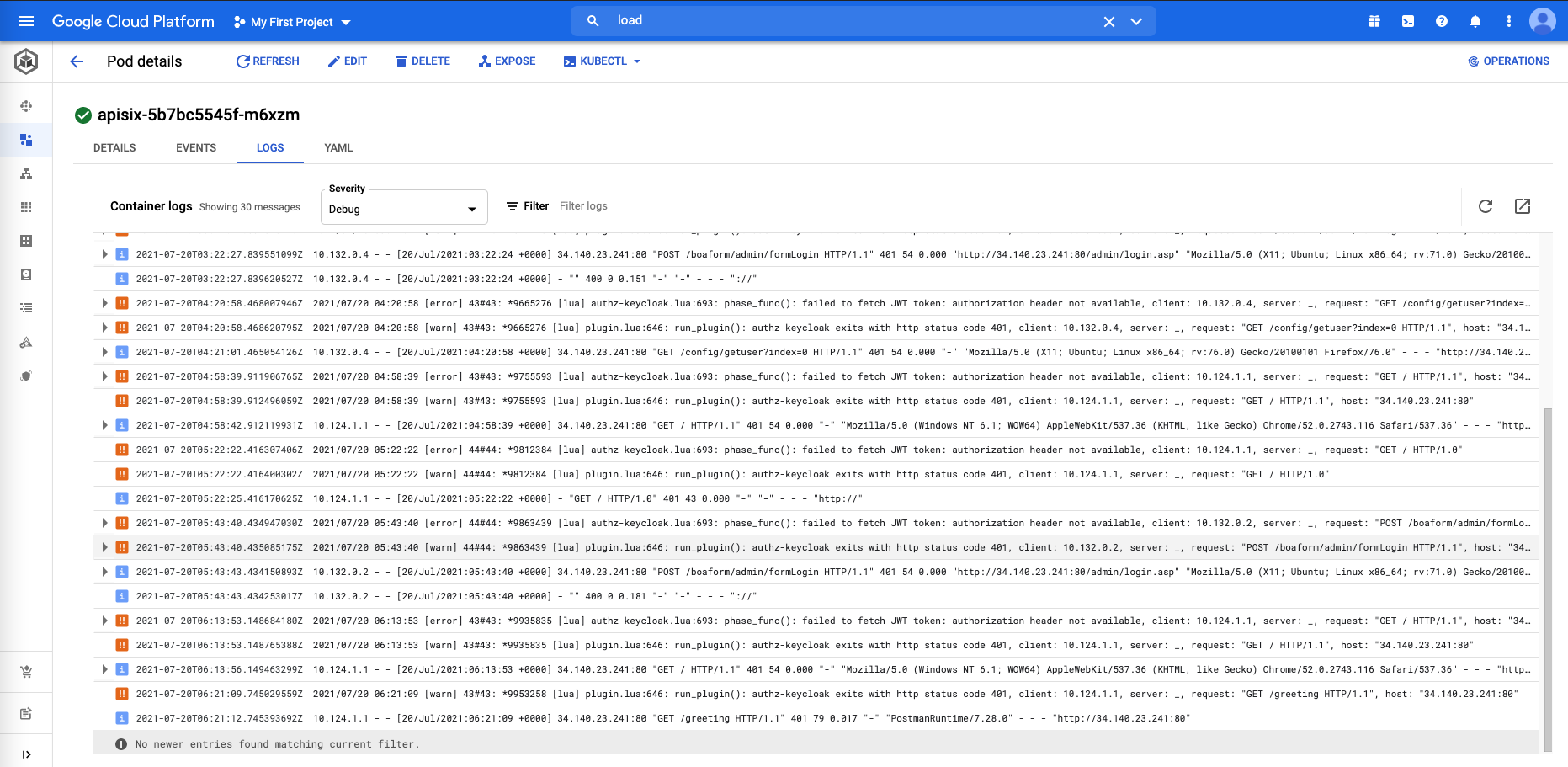
I thing that log is just a bad try I have made.
However when I send the Authorization header correctly, I get the "Invalid Bearer token" as you can see in the last two lines of the logs (see the joined screen shot).
The log is :
`plugin.lua:646: run_plugin(): authz-keycloak exits with http status code 401, client: 10.124.1.1, server: _, request: "GET /greeting HTTP/1.1", host: "34.140.23.241:80"`
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] cgodefroy92 edited a comment on issue #4616: Keycloak integration
Posted by GitBox <gi...@apache.org>.
cgodefroy92 edited a comment on issue #4616:
URL: https://github.com/apache/apisix/issues/4616#issuecomment-883477444
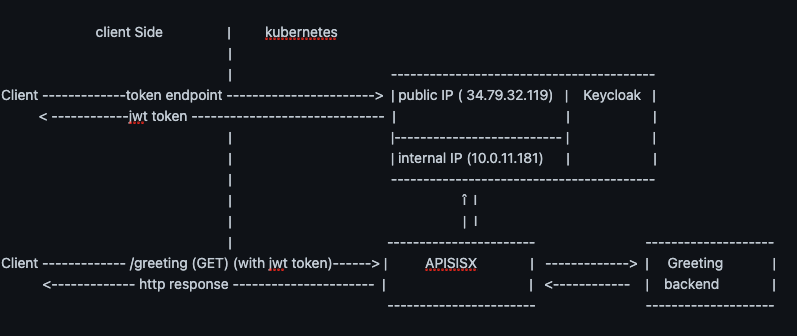
Thanks for your help. I understand that the IPs should be the same in order to make the Keycloak authentication with the jwt token works.
However I don't understand how to to do that. The only way I have found for the moment is by configuring the public IP of the Keycloak service in the APISIX route for the discovery end-point of the authz-keycloak plugin. I think it is not a good practice. I would prefer the request for the discovery plugin stay inside kubernetess.
In the other side, I don't know how to ask Keycloak a jwt token on the public ip of keycloak and force keycloak to return a jwt
payload with the internal IP of the keycloak server in the iis field value.
To fix the idea, here is my architecture :
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] cgodefroy92 commented on issue #4616: Keycloak integration
Posted by GitBox <gi...@apache.org>.
cgodefroy92 commented on issue #4616:
URL: https://github.com/apache/apisix/issues/4616#issuecomment-883529554
I have found how to force the value of the iss field in the jwt token. It is a configuration on the keycloak side : on the realm it is possible to set a "front-end" url which will be use to calculate the iss value field.
By this way, all works fine!

--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] tzssangglass commented on issue #4616: Keycloak integration
Posted by GitBox <gi...@apache.org>.
tzssangglass commented on issue #4616:
URL: https://github.com/apache/apisix/issues/4616#issuecomment-882181827
How you pass the token?
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] tokers commented on issue #4616: Keycloak integration
Posted by GitBox <gi...@apache.org>.
tokers commented on issue #4616:
URL: https://github.com/apache/apisix/issues/4616#issuecomment-882048033
@cgodefroy92 Could you show the related Route, Upstream configurations of your APISIX?
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] cgodefroy92 commented on issue #4616: Keycloak integration
Posted by GitBox <gi...@apache.org>.
cgodefroy92 commented on issue #4616:
URL: https://github.com/apache/apisix/issues/4616#issuecomment-882735687
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] cgodefroy92 commented on issue #4616: Keycloak integration
Posted by GitBox <gi...@apache.org>.
cgodefroy92 commented on issue #4616:
URL: https://github.com/apache/apisix/issues/4616#issuecomment-883477444
Thanks for your help. I understand that the IPs should be the same in order to make the Keycloak authentication with the jwt token works.
However I don't understand how to to do that. The only way I have found for the moment is by configuring the public IP of the Keycloak service in the APISIX route for the discovery end-point of the authz-keycloak plugin. I think it is not a good practice. I would prefer the request for the discovery plugin stay inside kubernetess.
In the other side, I don't know how to ask Keycloak a jwt token on the public ip of keycloak and force keycloak to return a jwt
payload with the internal IP of the keycloak server in the iis field value.
To fix the idea, here is my architecture :
client Side | kubernetes
|
| -----------------------------------------
Client -------------token endpoint -----------------------> | public IP ( 34.79.32.119) | Keycloak |
< ------------jwt token ------------------------------ | | |
| |-------------------------- | |
| | internal IP (10.0.11.181) | |
| -----------------------------------------
| î I
| | I
| ----------------------- --------------------
Client ------------- /greeting (GET) (with jwt token)------> | APISISX | -------------> | Greeting |
<------------- http response ---------------------- | | <------------ | backend |
----------------------- --------------------
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] cgodefroy92 commented on issue #4616: Keycloak integration
Posted by GitBox <gi...@apache.org>.
cgodefroy92 commented on issue #4616:
URL: https://github.com/apache/apisix/issues/4616#issuecomment-882283387
Hello,
The token is generated with this curl. command (where http://127.0.0.1:7070 is url of Keycloak):
```
curl --location --request POST 'http://127.0.0.1:7070/auth/realms/myrealm/protocol/openid-connect/token' \
--header 'Content-Type: application/x-www-form-urlencoded' \
--data-urlencode 'username=testuser' \
--data-urlencode 'password=test' \
--data-urlencode 'client_id=apisix' \
--data-urlencode 'client_secret=f7e62001-2413-4160-8cf8-fbbecb5d3567' \
--data-urlencode 'grant_type=password'
```
And then I use the token with this curl command (where http://127.0.0.1 is the url of the gateway):
```
curl --location -g --request GET 'http://127.0.0.1/greeting' \
--header 'Authorization: Bearer eyJhbGciOiJSUzI1NiIsInR5cCIgOiAiSldUIiwia2lkIiA6ICIzTmY5dzRyd2czYVdHcE5Lb3NSaXl6SHpSTkk0ZXdZOWRuNGlORHlHR1VzIn0.eyJleHAiOjE2MjY1Mjc2MjAsImlhdCI6MTYyNjUyNzMyMCwianRpIjoiYWU1M2RhYTAtNDNmNi00MTRkLWFjYTYtNDdhM2FhMzNkNjg5IiwiaXNzIjoiaHR0cDovLzM0Ljc5LjMyLjExOTo4MDgwL2F1dGgvcmVhbG1zL215cmVhbG0iLCJhdWQiOiJhY2NvdW50Iiwic3ViIjoiMGE0YTMxMjItNjQ5Ni00MWM2LTg0YWQtNGJmYTU1NmY4YjFmIiwidHlwIjoiQmVhcmVyIiwiYXpwIjoiYXBpc2l4Iiwic2Vzc2lvbl9zdGF0ZSI6Ijg5Y2NjMTc5LTEyMGQtNGQ1OS05Njk3LTk1OWRiYTA4NzM1ZCIsImFjciI6IjEiLCJyZWFsbV9hY2Nlc3MiOnsicm9sZXMiOlsiZGVmYXVsdC1yb2xlcy1teXJlYWxtIiwib2ZmbGluZV9hY2Nlc3MiLCJ1bWFfYXV0aG9yaXphdGlvbiJdfSwicmVzb3VyY2VfYWNjZXNzIjp7ImFjY291bnQiOnsicm9sZXMiOlsibWFuYWdlLWFjY291bnQiLCJtYW5hZ2UtYWNjb3VudC1saW5rcyIsInZpZXctcHJvZmlsZSJdfX0sInNjb3BlIjoiZW1haWwgcHJvZmlsZSIsImVtYWlsX3ZlcmlmaWVkIjpmYWxzZSwicHJlZmVycmVkX3VzZXJuYW1lIjoidXNlciJ9.NGFg-PQQY1aLf5NvOG28xOLMfD8BxInA4XUlmWXlhf4k2TmT3_aAT0OZAPhRt6hPJnxpdPLX74CKjw8hy-IaRfTuc-YEDyz6od5jYQKaPOjaQ_Xl4YZLpb
LnB4jRkjH1Z7WoaAxoRoss5CCWfcBmFZWxkNS_MPEYDPVQEU98jD2EanKmJgoOk4n3tX-yyq6LdG2TbzshpJBXxWMHreWczxzgpPQ4NUMbfTcW1d0Wy_kXRcqEOpHtzzx7EH13_DXCWpC9pL51rA5OuFbOI3klVItmTLeJb-fTFJuAlUl3s3YkX_8L-AsvGXI6ZzUfzxPhp4XzOGS7vdGsN_TxJxUyMA'
```
Thanks for your help.
Regards
CG
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] cgodefroy92 commented on issue #4616: Keycloak integration
Posted by GitBox <gi...@apache.org>.
cgodefroy92 commented on issue #4616:
URL: https://github.com/apache/apisix/issues/4616#issuecomment-882735687
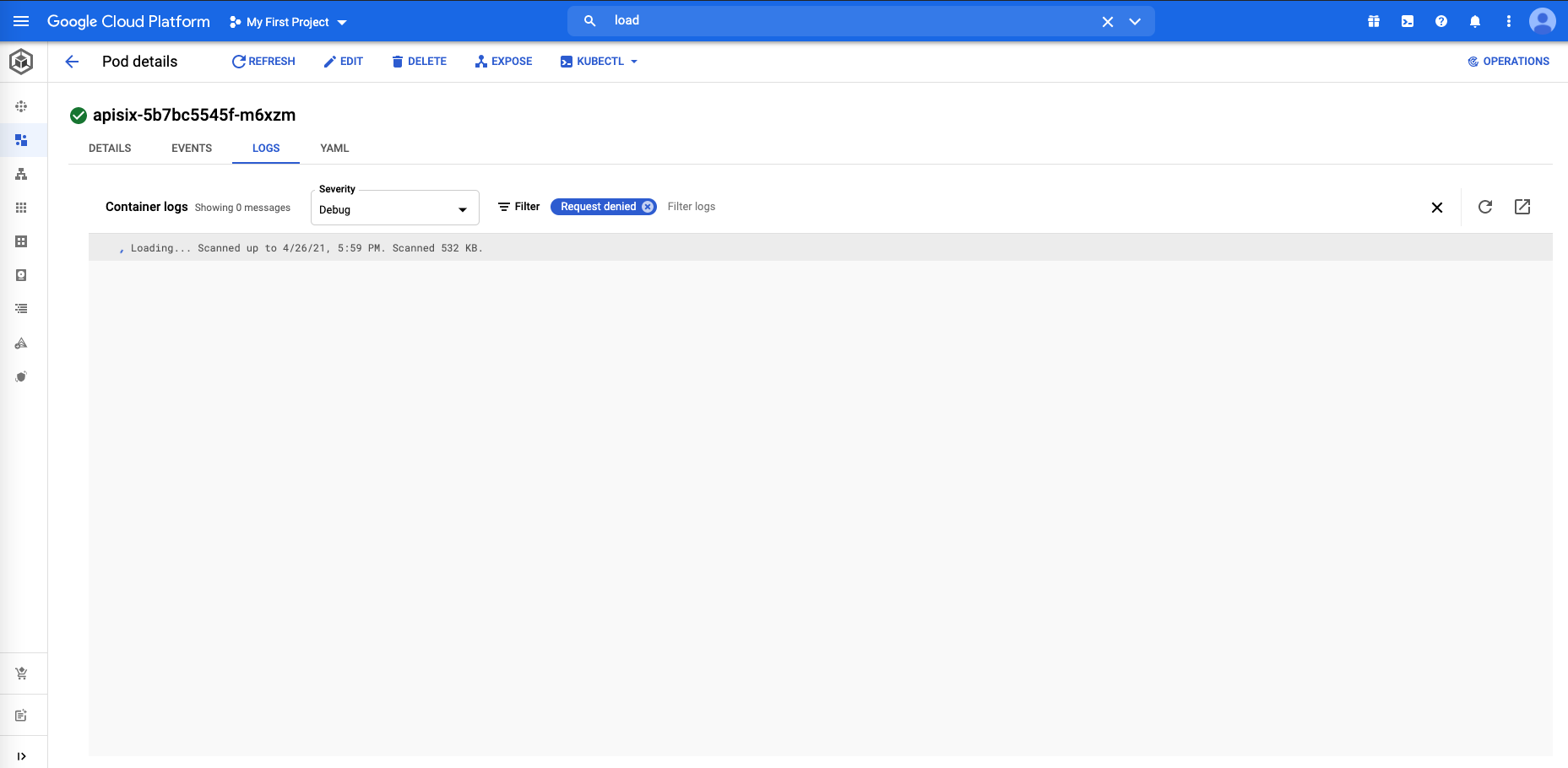
Hello,
Unfortunately, as you can see in the joined screen-shot, I don't find the logs you mentioned in your last post...
But I have joined a screen shot of the apy-gateway pod logs, and maybe you will understand what is happened.
Regards

--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] tzssangglass commented on issue #4616: Keycloak integration
Posted by GitBox <gi...@apache.org>.
tzssangglass commented on issue #4616:
URL: https://github.com/apache/apisix/issues/4616#issuecomment-882711876
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] cgodefroy92 commented on issue #4616: Keycloak integration
Posted by GitBox <gi...@apache.org>.
cgodefroy92 commented on issue #4616:
URL: https://github.com/apache/apisix/issues/4616#issuecomment-882104203
Hello and thanks for your response.
Here is the curl command I have used to create the route :
The url of the backend in the Kubernetes Cluster is : http://10.110.21.213:8181/greeting (GET method)
The url of the discovery end-point in KeyCloak in the Kubernetes Cluster is : http://10.103.25.28:7070/auth/realms/myrealm/.well-known/uma2-configuration
Regards
CG
```
curl http://127.0.0.1:9180/apisix/admin/routes -H 'X-API-KEY: edd1c9f034335f136f87ad84b625c8f1' -X POST -d '
{
"name": "greeting",
"uri": "/greeting",
"plugins": {
"authz-keycloak": {
"discovery": "http://10.103.25.28:7070/auth/realms/myrealm/.well-known/uma2-configuration",
"client_id": "apisix",
"client_secret": "**************",
"permissions": ["greeting#get"]
}
},
"upstream": {
"type": "roundrobin",
"nodes": {
"10.110.21.213:8181": 1
}
}
}'
```
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] tzssangglass commented on issue #4616: Keycloak integration
Posted by GitBox <gi...@apache.org>.
tzssangglass commented on issue #4616:
URL: https://github.com/apache/apisix/issues/4616#issuecomment-882711876
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] cgodefroy92 commented on issue #4616: Keycloak integration
Posted by GitBox <gi...@apache.org>.
cgodefroy92 commented on issue #4616:
URL: https://github.com/apache/apisix/issues/4616#issuecomment-884319201
In fact the issue was not solved because forcing the Frontend URL in Keycloak to the kubernetes internal URL is a problem when we try to code a front-end. (The front-end url of the keycloak login page became http://10.0.0.11.181:8080 which is not a public url reachable from outside the kubernetes cluster)
The only solution is to use the public IP of keycloak in the iss field of the token and find a way to change the way APISIX and Keycloak talk together, in order to Keycloak accept the token whereas APISIX call the discovery end-point with the internal IP.
I have read some posts about the usage of keycloak behind a reverse proxy and it seems that we have to pass some headers to Keycloak (X-Forwarded-For and X-Forwarded-Proto):
https://stackoverflow.com/questions/47068266/keycloak-docker-behind-loadbalancer-with-https-fails
Regards
CG
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] tzssangglass commented on issue #4616: Keycloak integration
Posted by GitBox <gi...@apache.org>.
tzssangglass commented on issue #4616:
URL: https://github.com/apache/apisix/issues/4616#issuecomment-883166849
Sorry, then this should be two questions.
step 1: adjust the log level to debug of apisix: https://github.com/apache/apisix/blob/0a583e8549a3df61ed3927207f9f7e189afea87a/docs/en/latest/FAQ.md#how-to-change-the-log-level
step 2: capture the log here: https://github.com/apache/apisix/blob/8693756470dca8228aa1a5b83ee3acc3603ed5f5/apisix/plugins/authz-keycloak.lua#L656-L669
I think the problem is that `res.status == 401`, Keycloak returned 401 after verifying the token.
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] tzssangglass commented on issue #4616: Keycloak integration
Posted by GitBox <gi...@apache.org>.
tzssangglass commented on issue #4616:
URL: https://github.com/apache/apisix/issues/4616#issuecomment-883104170
I saw the message: failed to fetch JWT token: authorization header not available. This means that the request headers do not include the `Authorization`.
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] cgodefroy92 closed issue #4616: Keycloak integration
Posted by GitBox <gi...@apache.org>.
cgodefroy92 closed issue #4616:
URL: https://github.com/apache/apisix/issues/4616
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] tzssangglass commented on issue #4616: Keycloak integration
Posted by GitBox <gi...@apache.org>.
tzssangglass commented on issue #4616:
URL: https://github.com/apache/apisix/issues/4616#issuecomment-883525124
I don't have any ideas either. What I can think of is to control the keyclock so that it doesn't check the ip.
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org