You are viewing a plain text version of this content. The canonical link for it is here.
Posted to commits@airflow.apache.org by GitBox <gi...@apache.org> on 2021/02/16 03:16:36 UTC
[GitHub] [airflow] rajeshkatkarnice opened a new issue #14253: Airflow 1.10.10 blackduck scan security risks
rajeshkatkarnice opened a new issue #14253:
URL: https://github.com/apache/airflow/issues/14253
<!--
Welcome to Apache Airflow! For a smooth issue process, try to answer the following questions.
Don't worry if they're not all applicable; just try to include what you can :-)
If you need to include code snippets or logs, please put them in fenced code
blocks. If they're super-long, please use the details tag like
<details><summary>super-long log</summary> lots of stuff </details>
Please delete these comment blocks before submitting the issue.
-->
<!--
IMPORTANT!!!
PLEASE CHECK "SIMILAR TO X EXISTING ISSUES" OPTION IF VISIBLE
NEXT TO "SUBMIT NEW ISSUE" BUTTON!!!
PLEASE CHECK IF THIS ISSUE HAS BEEN REPORTED PREVIOUSLY USING SEARCH!!!
Please complete the next sections or the issue will be closed.
These questions are the first thing we need to know to understand the context.
-->
**Apache Airflow version**: 1.10.10
**Kubernetes version (if you are using kubernetes)** (use `kubectl version`): NA
**Environment**: linux ec2
- **Cloud provider or hardware configuration**: airflow hosted on ec2
**What happened**:
<!-- (please include exact error messages if you can) -->
**What you expected to happen**:
<!-- What do you think went wrong? -->
**How to reproduce it**:
<!---
As minimally and precisely as possible. Keep in mind we do not have access to your cluster or dags.
If you are using kubernetes, please attempt to recreate the issue using minikube or kind.
## Install minikube/kind
- Minikube https://minikube.sigs.k8s.io/docs/start/
- Kind https://kind.sigs.k8s.io/docs/user/quick-start/
If this is a UI bug, please provide a screenshot of the bug or a link to a youtube video of the bug in action
You can include images using the .md style of

To record a screencast, mac users can use QuickTime and then create an unlisted youtube video with the resulting .mov file.
--->
**Anything else we need to know**:
<!--
How often does this problem occur? Once? Every time etc?
Any relevant logs to include? Put them here in side a detail tag:
<details><summary>x.log</summary> lots of stuff </details>
-->
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [airflow] potiuk edited a comment on issue #14253: Airflow 1.10.10 blackduck scan security risks
Posted by GitBox <gi...@apache.org>.
potiuk edited a comment on issue #14253:
URL: https://github.com/apache/airflow/issues/14253#issuecomment-779577586
Hello @rajeshkatkarnice. Thanks for reporting those, but this is not the way security issues should be reported, this report is not actionable.
One comment - I know BlackDuck first hand and I know that it often reports issues which are not existing. We have no BlackDuck licences so we cannot reproduce your results, so it is difficult to act on your report.
First of all, can you please re-run your checks on 1.10.14 if you want to use 1.10 line. There were many changes and updates since 1.10.10 and it is likely at least some of those problems have been fixed in subsequent versions. We are not releasing patches to earlier versions. If there are any critical security fixes we will release them in 1.10.15, 1.10.16 - there won't ever be 1.10.10.1 release for exmple. So I will kindly ask you to re-run your Black Duck scan on 1.10.14 if you want some action to be taken.
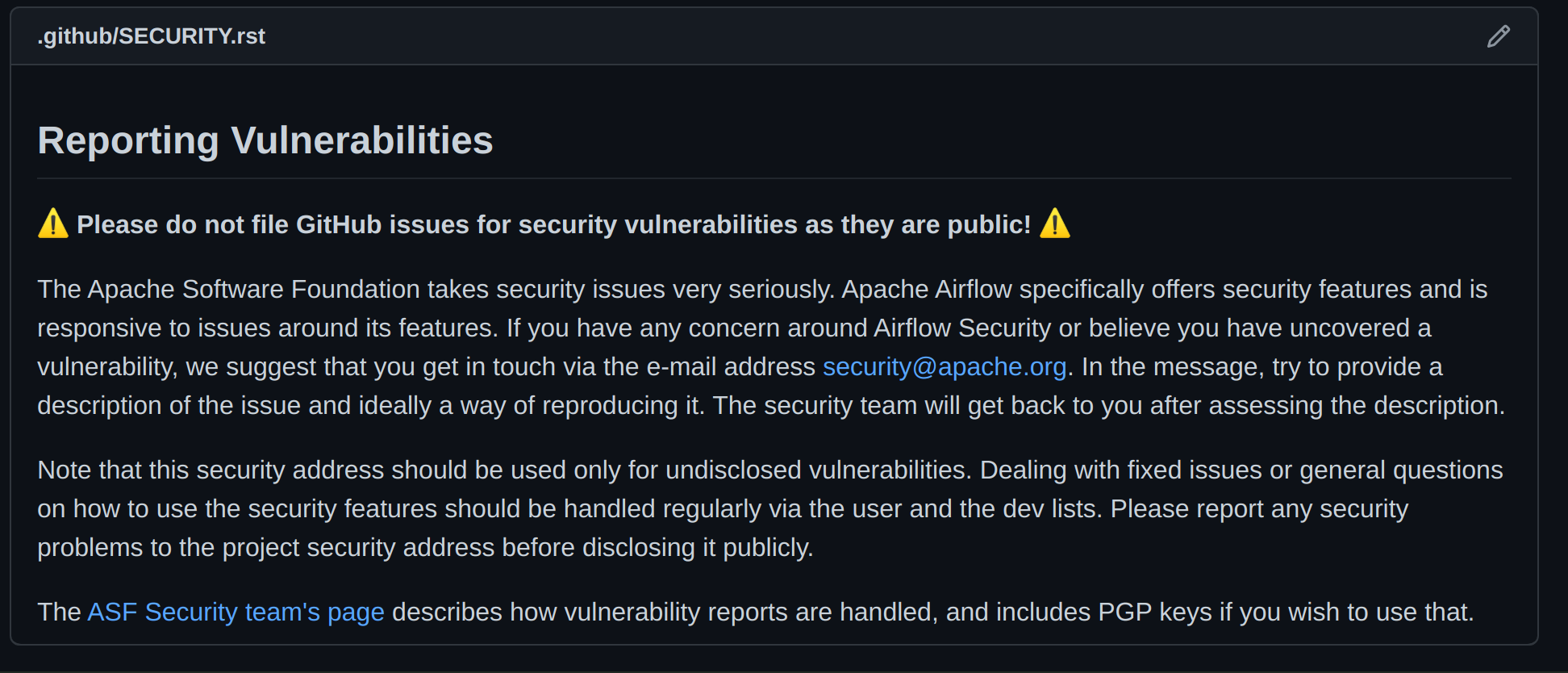
Secondly - if you do, suspect any problems with security, you report it via email to security@apache.org - not via public issue. This is detailed in https://www.apache.org/security/ and the rules there are rather clear:
```
Please send one plain-text email for each vulnerability you are reporting. We may ask you to resubmit your report if you send it as an image, movie, HTML, or PDF attachment when it could just as easily be described with plain text.
```
So you should break it down into separate issues and sent it there.
This list is private and this is the "responsible disclosure" process that you should follow. You should never discuss even suspected security issues in public issues. It also allows to properly process the issues with assigning CVEs when the issue is triaged and found a real issue.
So may I ask you - kindly - rerun your scans on latest 1.10 version (possibly also on latest 2.0 version) and follow the process of reporting the issues this way. Just for the sake of not allowing an easy discovery of potential security issue I will edit the issue now and close it.
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [airflow] potiuk commented on issue #14253: Airflow 1.10.10 blackduck scan security risks
Posted by GitBox <gi...@apache.org>.
potiuk commented on issue #14253:
URL: https://github.com/apache/airflow/issues/14253#issuecomment-779577586
Hello @rajeshkatkarnice. Thanks for reporting those, but this is not the way security issues should be reported, this report is not actionable.
One comment - I know BlackDuck first hand and I know that it often reports issues which are not existing. We have no BlackDuck licences so we cannot reproduce your results, so it is difficult to act on your report.
First of all, can you please re-run your checks on 1.10.14 if you want to use 1.10 line. There were many changes and updates since 1.10.10 and it is likely at least some of those problems have been fixed in subsequent versions. We are not releasing patches to earlier versions. If there are any critical security fixes we will release them in 1.10.15, 1.10.16 - there won't ever be 1.10.10.1 release for exmple. So I will kindly ask you to re-run your Black Duck scan on 1.10.14 if you want some action to be taken.
Secondly - if you do, suspect any problems with security, you report it via email to security@apache.org - not via public issue. This is detailed in https://www.apache.org/security/ and the rules there are rather clear:
```
Please send one plain-text email for each vulnerability you are reporting. We may ask you to resubmit your report if you send it as an image, movie, HTML, or PDF attachment when it could just as easily be described with plain text.
```
So you should break it down into separate issues and sent it there.
This list is private and this is the "responsible disclosure" process that you should follow. You should never discuss even suspected security issues in public issues. It also allows to properly process the issues with assigning CVEs when the issue is triaged and found a real issue.
So may I ask you - kindly - rerun your scans on latest 1.10 version (possibly also on latest 2.0 version) and follow the process of reporting the issues this way. Just for the sake of easy discovery I will edit the issue now and close it.
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [airflow] potiuk commented on issue #14253: Airflow 1.10.10 blackduck scan security risks
Posted by GitBox <gi...@apache.org>.
potiuk commented on issue #14253:
URL: https://github.com/apache/airflow/issues/14253#issuecomment-779714446
The answer you get is becauyse you lilely sent them the full report and it was not following this:
```
Please send one plain-text email for each vulnerability you are reporting.
```
As the message from security team says - just a report produced by any tool is out of context and it does not mean that the code is affected. Those reports are often misleading, so it would be great to make use of the report, but:
1) Rerunning it on 1.10.14 might limit the number of reported vulnerabilities
2) Submitting it in one big issue is not really helpful. If you would like to report it to us, that is great, but Ideally it should be itemised into separate issues per vulnerability and pre-screened by you. This is a community driven project, so there is no single person that can review the report and decide what to do with every single problem there - but since you have the tool and experience wiht it, you can actually help the community and pre-screen those issues. You can help by reviewing and decide yourself if this is a real issue affecting the UI or not and only report it afterwards:
* If you think it is critical security issue - report it separately (one -per item) to security@apache.org in private
* If you think it's not critical, you might check if it is already fixed in 2.0 (should be easy to check by looking at the package versions) - we are not likely to fix non-critical issues in 1.10 line.
* if you think that there is an important reasons for us to update, then please submit it is as a separate issue each (explaining why you think it is worth to fix in 1.10 line).
Generally itemizing the issues should be helpful also for you to understand if those issues are worth reporting at all.
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [airflow] potiuk commented on issue #14253: Airflow 1.10.10 blackduck scan security risks
Posted by GitBox <gi...@apache.org>.
potiuk commented on issue #14253:
URL: https://github.com/apache/airflow/issues/14253#issuecomment-779578221
Also - those rules are explained when you report issues - when you create "New Issue" there is quite clear "Report security issue" link that leads you to the ASF security paage.
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [airflow] rajeshkatkarnice commented on issue #14253: Airflow 1.10.10 blackduck scan security risks
Posted by GitBox <gi...@apache.org>.
rajeshkatkarnice commented on issue #14253:
URL: https://github.com/apache/airflow/issues/14253#issuecomment-779698441
@potiuk we already have communicated these issue over mail to Apache Security Team before raising these issues.
We got below reply from Mark(mjc@gsuite.cloud.apache.org )
//
Hi,
Outdated dependencies are not always security issues. A project would only be affected if a dependency was used in such a way that the affected underlying code is used and the vulnerabilities were exposed. We typically get reports sent to us from scanning tools that looks at dependencies out of context on how they are actually used in the projects. As such we reject these reports and suggest you either a) show how the product is affected by the dependency vulnerabilities, or b) simply mention this as a normal bug report to that project. Since dependency vulnerabilities are quite public, there is no need to use this private reporting mechanism for them.
Regards, Mark
//
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [airflow] potiuk edited a comment on issue #14253: Airflow 1.10.10 blackduck scan security risks
Posted by GitBox <gi...@apache.org>.
potiuk edited a comment on issue #14253:
URL: https://github.com/apache/airflow/issues/14253#issuecomment-779578221
Also - those rules are explained when you report issues - when you create "New Issue" there is quite clear "Report security issue" link that leads you to the ASF security page.
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [airflow] potiuk edited a comment on issue #14253: Airflow 1.10.10 blackduck scan security risks
Posted by GitBox <gi...@apache.org>.
potiuk edited a comment on issue #14253:
URL: https://github.com/apache/airflow/issues/14253#issuecomment-779578221
Also - those rules are explained when you report issues - when you create "New Issue" there is quite clear "Report security issue" link that leads you to the ASF security page.
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [airflow] potiuk edited a comment on issue #14253: Airflow 1.10.10 blackduck scan security risks
Posted by GitBox <gi...@apache.org>.
potiuk edited a comment on issue #14253:
URL: https://github.com/apache/airflow/issues/14253#issuecomment-779577586
Hello @rajeshkatkarnice. Thanks for reporting those, but this is not the way security issues should be reported, this report is not actionable and security issues should never be discussed in public issues.
One comment - I know BlackDuck first hand and I know that it often reports issues which are not existing. We have no BlackDuck licences so we cannot reproduce your results, so it is difficult to act on your report.
First of all, can you please re-run your checks on 1.10.14 if you want to use 1.10 line. There were many changes and updates since 1.10.10 and it is likely at least some of those problems have been fixed in subsequent versions. We are not releasing patches to earlier versions. If there are any critical security fixes we will release them in 1.10.15, 1.10.16 - there won't ever be 1.10.10.1 release for exmple. So I will kindly ask you to re-run your Black Duck scan on 1.10.14 if you want some action to be taken.
Secondly - if you do, suspect any problems with security, you report it via email to security@apache.org - not via public issue. This is detailed in https://www.apache.org/security/ and the rules there are rather clear:
```
Please send one plain-text email for each vulnerability you are reporting. We may ask you to resubmit your report if you send it as an image, movie, HTML, or PDF attachment when it could just as easily be described with plain text.
```
So you should break it down into separate issues and sent it there.
This list is private and this is the "responsible disclosure" process that you should follow. You should never discuss even suspected security issues in public issues. It also allows to properly process the issues with assigning CVEs when the issue is triaged and found a real issue.
So may I ask you - kindly - rerun your scans on latest 1.10 version (possibly also on latest 2.0 version) and follow the process of reporting the issues this way. Just for the sake of not allowing an easy discovery of potential security issue I will edit the issue now and close it.
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [airflow] potiuk edited a comment on issue #14253: Airflow 1.10.10 blackduck scan security risks
Posted by GitBox <gi...@apache.org>.
potiuk edited a comment on issue #14253:
URL: https://github.com/apache/airflow/issues/14253#issuecomment-779577586
Hello @rajeshkatkarnice. Thanks for reporting those, but this is not the way security issues should be reported, this report is not actionable and security issues should never be discussed in public issues.
One comment - I know BlackDuck first hand and I know that it often reports issues which are not existing. We have no BlackDuck licences so we cannot reproduce your results, so it is difficult to act on your report.
First of all, can you please re-run your checks on 1.10.14 if you want to use 1.10 line. There were many changes and updates since 1.10.10 and it is likely at least some of those problems have been fixed in subsequent versions. We are not releasing patches to earlier versions. If there are any critical security fixes we will release them in 1.10.15, 1.10.16 - there won't ever be 1.10.10.1 release for exmple. So I will kindly ask you to re-run your Black Duck scan on 1.10.14 if you want some action to be taken.
Secondly - if you do, suspect any problems with security, you report it via email to security@apache.org - not via public issue. This is detailed in https://www.apache.org/security/ and the rules there are rather clear:
```
Please send one plain-text email for each vulnerability you are reporting. We may ask you to resubmit your report if you send it as an image, movie, HTML, or PDF attachment when it could just as easily be described with plain text.
```
So you should break it down into separate issues and sent it there.
This list is private and this is the "responsible disclosure" process that you should follow. You should never discuss even suspected security issues in public issues. It also allows to properly process the issues with assigning CVEs when the issue is triaged and found to be a real issue.
So may I ask you - kindly - rerun your scans on latest 1.10 version (possibly also on latest 2.0 version) and follow the process of reporting the issues this way. Just for the sake of not allowing an easy discovery of potential security issue I will edit the issue now and close it.
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [airflow] potiuk closed issue #14253: Airflow 1.10.10 blackduck scan security risks
Posted by GitBox <gi...@apache.org>.
potiuk closed issue #14253:
URL: https://github.com/apache/airflow/issues/14253
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [airflow] potiuk edited a comment on issue #14253: Airflow 1.10.10 blackduck scan security risks
Posted by GitBox <gi...@apache.org>.
potiuk edited a comment on issue #14253:
URL: https://github.com/apache/airflow/issues/14253#issuecomment-779577586
Hello @rajeshkatkarnice. Thanks for reporting those, but this is not the way security issues should be reported, this report is not actionable and security issues should never be discussed in public issues.
One comment - I know BlackDuck first hand and I know that it often reports issues which are not existing. We have no BlackDuck licences so we cannot reproduce your results, so it is difficult to act on your report. Can you please validate the issues before reporting them individually - each issue should be checked if this is a real, or perceived issue before reporting.
First of all, can you please re-run your checks on 1.10.14 if you want to use 1.10 line. There were many changes and updates since 1.10.10 and it is likely at least some of those problems have been fixed in subsequent versions. We are not releasing patches to earlier versions. If there are any critical security fixes we will release them in 1.10.15, 1.10.16 - there won't ever be 1.10.10.1 release for exmple. So I will kindly ask you to re-run your Black Duck scan on 1.10.14 if you want some action to be taken.
Secondly - if you do, suspect any problems with security, you report it via email to security@apache.org - not via public issue. This is detailed in https://www.apache.org/security/ and the rules there are rather clear:
```
Please send one plain-text email for each vulnerability you are reporting. We may ask you to resubmit your report if you send it as an image, movie, HTML, or PDF attachment when it could just as easily be described with plain text.
```
So you should break it down into separate issues and sent it there.
This list is private and this is the "responsible disclosure" process that you should follow. You should never discuss even suspected security issues in public issues. It also allows to properly process the issues with assigning CVEs when the issue is triaged and found to be a real issue.
So may I ask you - kindly - please rerun your scans on latest 1.10 version (possibly also on latest 2.0 version) and follow the process of reporting the issues this way. Just for the sake of not allowing an easy discovery of potential security issue I will edit the issue now and close it.
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [airflow] potiuk edited a comment on issue #14253: Airflow 1.10.10 blackduck scan security risks
Posted by GitBox <gi...@apache.org>.
potiuk edited a comment on issue #14253:
URL: https://github.com/apache/airflow/issues/14253#issuecomment-779578221
Also - those rules are explained when you report issues - when you create "New Issue" there is quite clear "Policy" link that leads you to the ASF security page.

----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [airflow] potiuk edited a comment on issue #14253: Airflow 1.10.10 blackduck scan security risks
Posted by GitBox <gi...@apache.org>.
potiuk edited a comment on issue #14253:
URL: https://github.com/apache/airflow/issues/14253#issuecomment-779577586
Hello @rajeshkatkarnice. Thanks for reporting those, but this is not the way security issues should be reported, this report is not actionable and security issues should never be discussed in public issues.
One comment - I know BlackDuck first hand and I know that it often reports issues which are not existing. We have no BlackDuck licences so we cannot reproduce your results, so it is difficult to act on your report.
First of all, can you please re-run your checks on 1.10.14 if you want to use 1.10 line. There were many changes and updates since 1.10.10 and it is likely at least some of those problems have been fixed in subsequent versions. We are not releasing patches to earlier versions. If there are any critical security fixes we will release them in 1.10.15, 1.10.16 - there won't ever be 1.10.10.1 release for exmple. So I will kindly ask you to re-run your Black Duck scan on 1.10.14 if you want some action to be taken.
Secondly - if you do, suspect any problems with security, you report it via email to security@apache.org - not via public issue. This is detailed in https://www.apache.org/security/ and the rules there are rather clear:
```
Please send one plain-text email for each vulnerability you are reporting. We may ask you to resubmit your report if you send it as an image, movie, HTML, or PDF attachment when it could just as easily be described with plain text.
```
So you should break it down into separate issues and sent it there.
This list is private and this is the "responsible disclosure" process that you should follow. You should never discuss even suspected security issues in public issues. It also allows to properly process the issues with assigning CVEs when the issue is triaged and found to be a real issue.
So may I ask you - kindly - please rerun your scans on latest 1.10 version (possibly also on latest 2.0 version) and follow the process of reporting the issues this way. Just for the sake of not allowing an easy discovery of potential security issue I will edit the issue now and close it.
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org