You are viewing a plain text version of this content. The canonical link for it is here.
Posted to notifications@apisix.apache.org by ju...@apache.org on 2022/06/16 07:54:38 UTC
[apisix-website] branch master updated: docs: use CDN to load images (#1157)
This is an automated email from the ASF dual-hosted git repository.
juzhiyuan pushed a commit to branch master
in repository https://gitbox.apache.org/repos/asf/apisix-website.git
The following commit(s) were added to refs/heads/master by this push:
new 1274c1c3954 docs: use CDN to load images (#1157)
1274c1c3954 is described below
commit 1274c1c39543dcc459b442d737fd29d1e62ac7e2
Author: feihan <97...@users.noreply.github.com>
AuthorDate: Thu Jun 16 15:54:33 2022 +0800
docs: use CDN to load images (#1157)
---
.../06/14/automated-operation-base-apache-apisix.md | 16 ++++++++--------
...mse-supports-canary-release-with-apache-apisix.md | 16 ++++++++--------
.../06/14/automated-operation-base-apache-apisix.md | 20 ++++++++++----------
...mse-supports-canary-release-with-apache-apisix.md | 16 ++++++++--------
4 files changed, 34 insertions(+), 34 deletions(-)
diff --git a/website/blog/2022/06/14/automated-operation-base-apache-apisix.md b/website/blog/2022/06/14/automated-operation-base-apache-apisix.md
index 4fd50a6ed02..ebeaba0539a 100644
--- a/website/blog/2022/06/14/automated-operation-base-apache-apisix.md
+++ b/website/blog/2022/06/14/automated-operation-base-apache-apisix.md
@@ -2,7 +2,7 @@
title: "Build automated operation platform based on Apache APISIX"
authors:
- name: "Qing Chen"
- title: "Author"
+ title: "Author"
url: "https://github.com/chenqing24"
image_url: "https://avatars.githubusercontent.com/u/3502467?v=4"
- name: "Fei Han"
@@ -12,8 +12,8 @@ authors:
keywords:
- Apache APISIX
- API Gateway
-- Operation
-- Microservice
+- Operation
+- Microservice
- Lua
description: In this article, introduces how to implement an automated operation and maintenance platform based on Apache APISIX.
tags: [Technology]
@@ -35,7 +35,7 @@ During the selection of gateway, we have carried out the actual test. Compared w
The overall architecture of the automation operation and maintenance platform is as follows:
-
+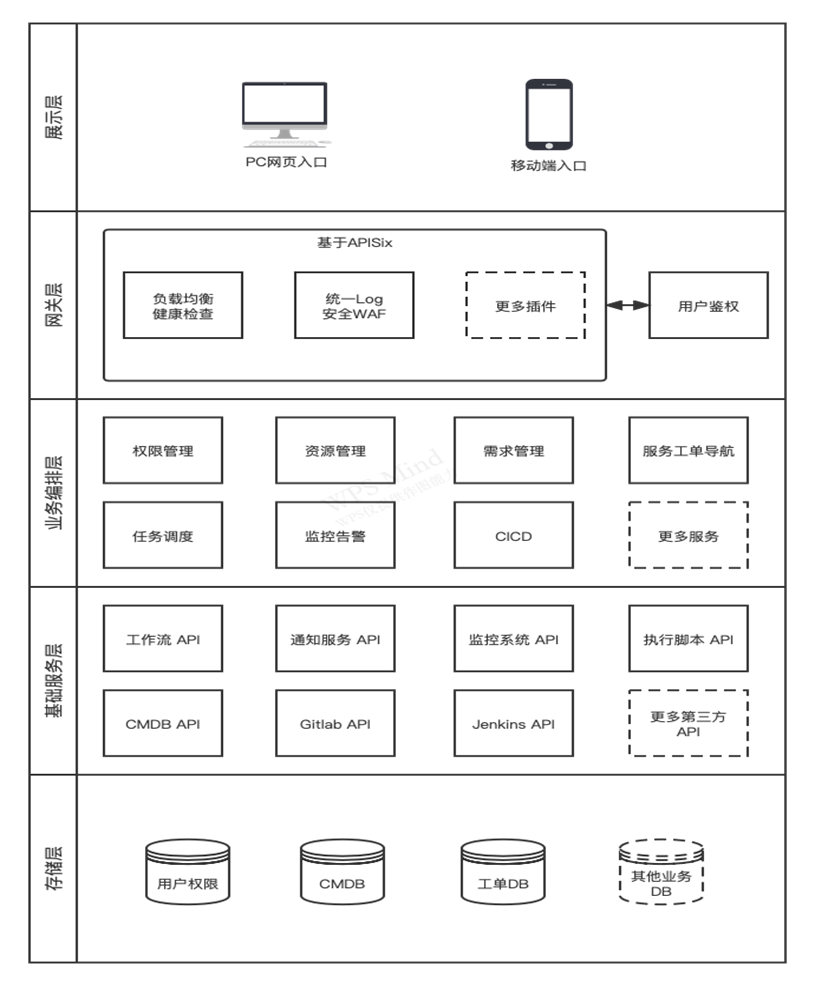
- Storage layer: the core is CMDB. Its main function is to record and manage the attributes of the organization's business and its resources, as well as the relationships between them. Not only is it responsible for querying the initial status of all business changes, but also all business resource changes should be fed back and recorded in it to realize the control of business standards and specifications. The storage layer also contains some authority management data, business work ord [...]
@@ -73,7 +73,7 @@ The overall architecture of the automation operation and maintenance platform is
For all Web frameworks, user login is a mandatory option, and I will introduce this scenario to you next.
-
+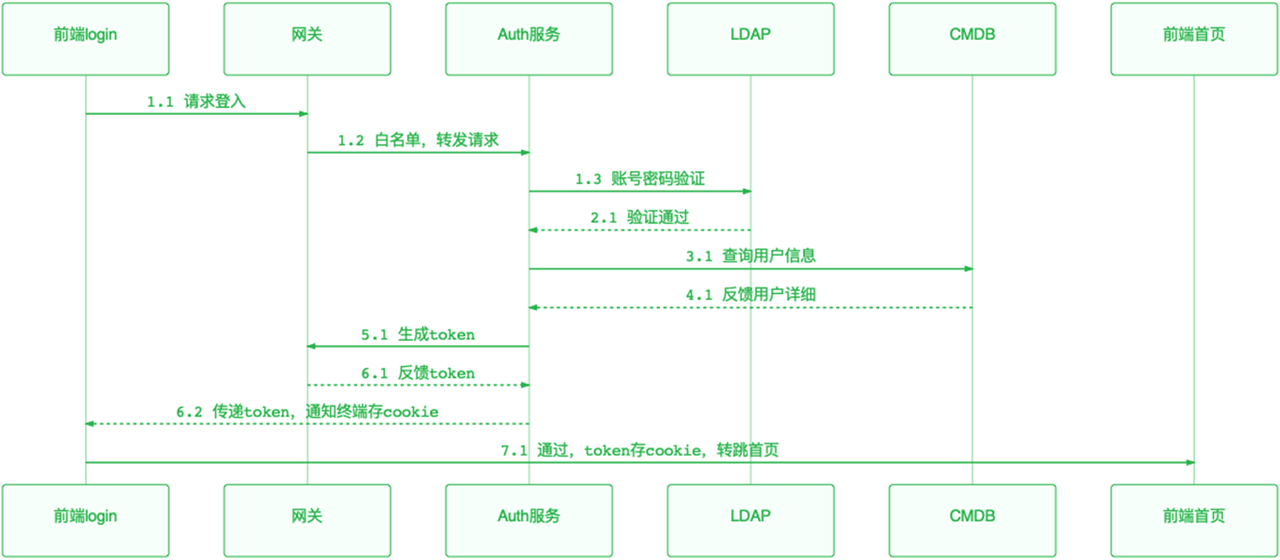
First of all, we need to understand the relevant components we use in the scenario. The first is the access front end, which is outside the gateway. Secondly, we use the APISIX cloud native API gateway as the business boundary. Then the auth service, which is a self-defined microservice, is used to verify the front-end URL request and user login request, and issue tokens to authenticated users. LDAP stores the company's internal password information. CMDB stores some business-related inf [...]
@@ -87,11 +87,11 @@ Here, we use the [`consumer restriction`](https://apisix.apache.org/zh/docs/apis
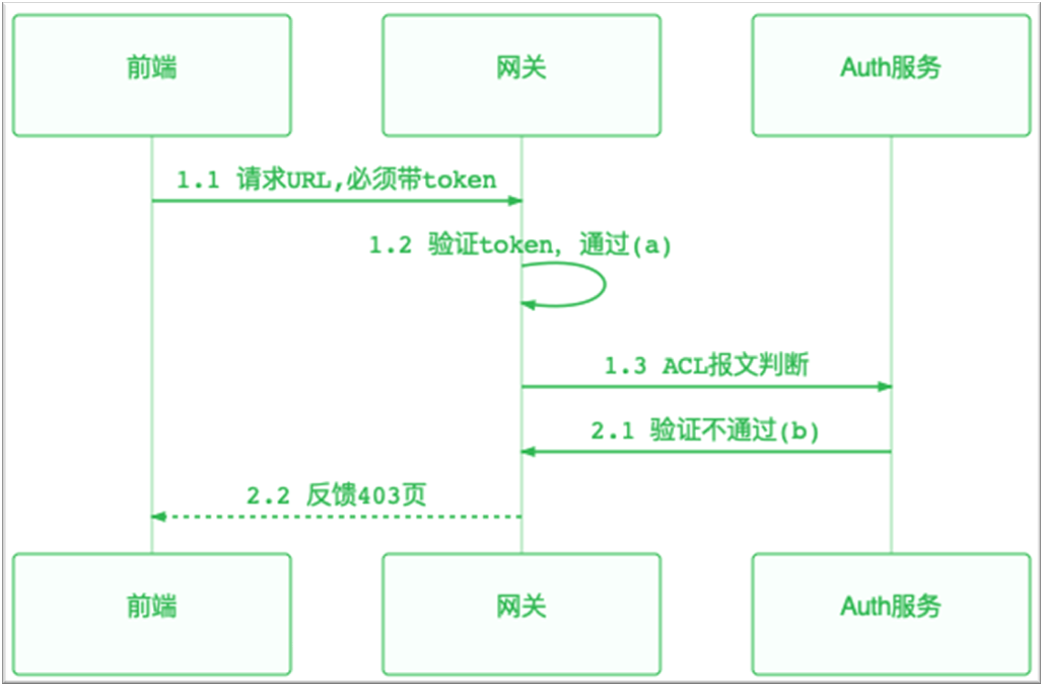
Through the above description, I believe you have a certain understanding of the normal request process. Next, I will introduce you to the scenarios of how to judge the insufficient permissions of these users. In the operation and maintenance platform, if there is an operation involving data change, a token must be carried. When the token is verified by the ACL interface that it has no access, it will directly return to a page that is forbidden to access for the front end to the process. [...]
-
+
### New service microservice access
-
+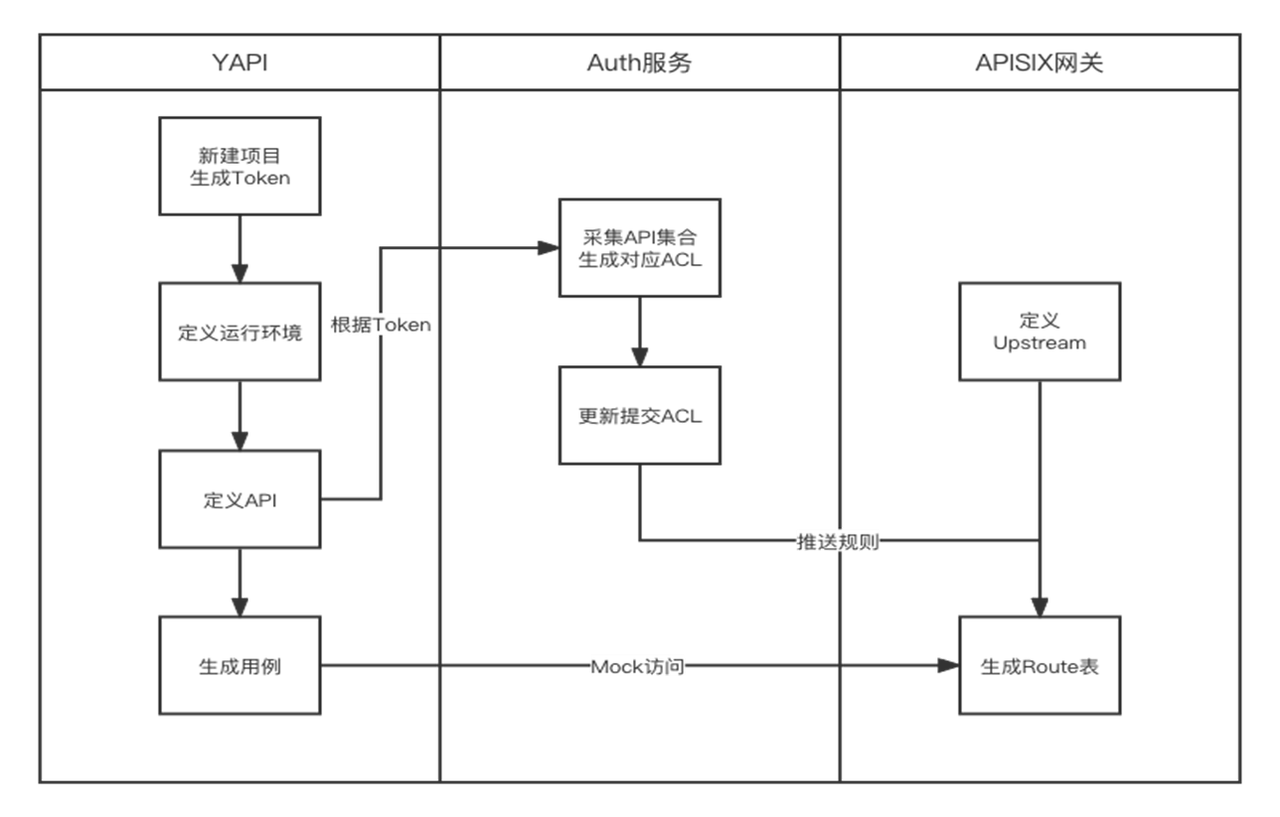
In our daily work, we often launch some microservices, so how can we connect this microservice to the automatic operation and maintenance platform?
@@ -105,7 +105,7 @@ The model is not only applicable to the automatic operation and maintenance plat
Through the above scenario description, I believe you have a general understanding of the whole system. Next, I will introduce some technical details to you.
-
+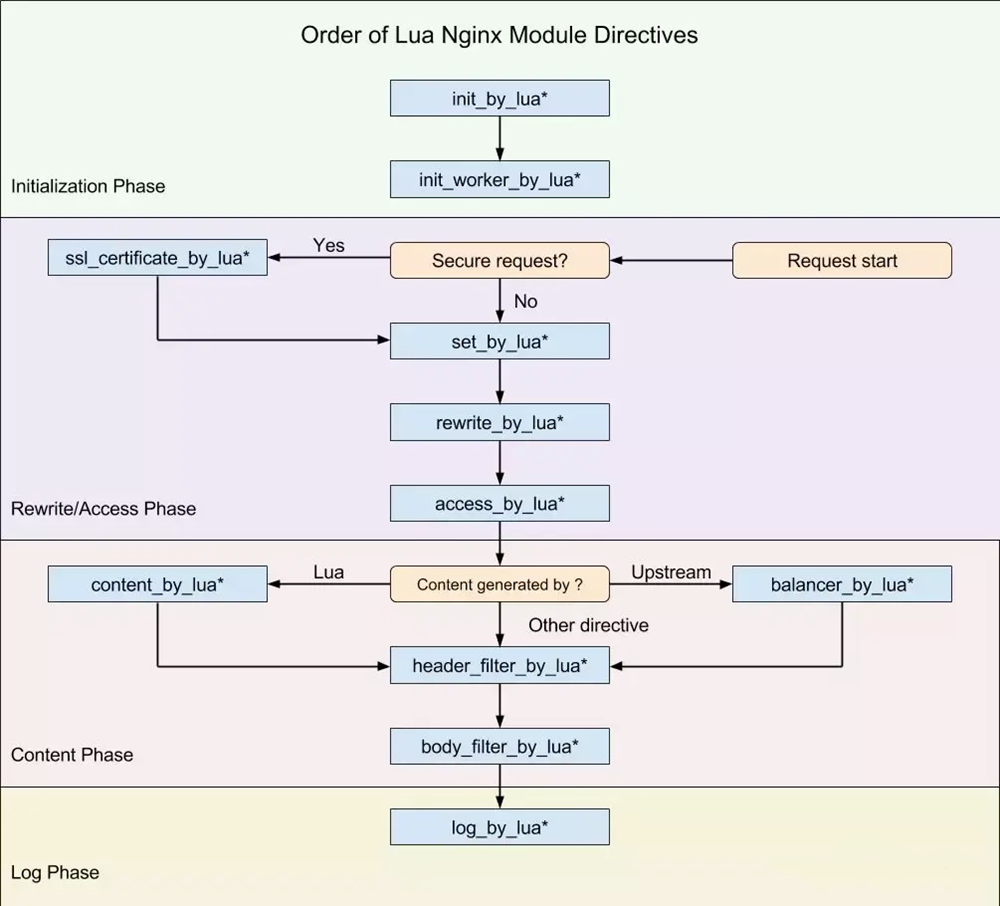
Because APISIX is implemented based on NGINX+Lua, some functions need to be implemented through NGINX libraries. From the above figure, we can see where various Lua scripts can be cut into NGINX. In this article, we mainly introduce the operations that can be performed in the rewrite/access and content phases.
diff --git a/website/blog/2022/06/14/how-mse-supports-canary-release-with-apache-apisix.md b/website/blog/2022/06/14/how-mse-supports-canary-release-with-apache-apisix.md
index fd0c9765eae..7f1d54af25e 100644
--- a/website/blog/2022/06/14/how-mse-supports-canary-release-with-apache-apisix.md
+++ b/website/blog/2022/06/14/how-mse-supports-canary-release-with-apache-apisix.md
@@ -11,8 +11,8 @@ keywords:
- Apache APISIX
- API Gateway
- Alibaba Cloud
-- Microservice
-- MSE
+- Microservice
+- MSE
- Traffic
description: This article describes how Alibaba Cloud's microservice engine MSE is based on the flexible routing capabilities of Apache APISIX, cooperates with MSE's full-link grayscale capabilities, and achieves full-link grayscale through minimal configuration and code-free intrusion.
tags: [Technology]
@@ -55,7 +55,7 @@ How to quickly implement canary release solution along the whole life cycle in t
Physical environment isolation, in fact, is to build real traffic isolation by adding machines.
-
+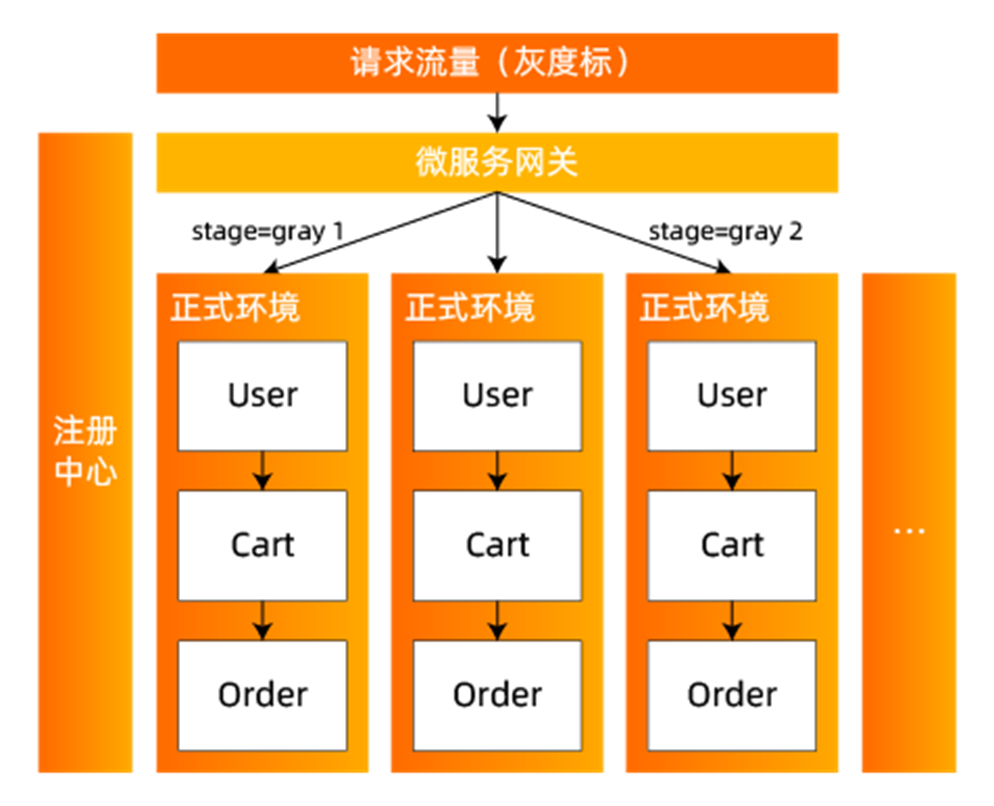
This scheme needs to build a set of network isolated and resource-independent environments for canary services, and deploy the canary version of the services in it. Because it is isolated from the formal environment, other services in the formal environment cannot access the services that need canary release. Therefore, these online services need to be deployed redundantly in the canary deployment so that the entire call link can forward traffic normally. In addition, some other dependen [...]
@@ -65,7 +65,7 @@ This scheme is generally used to build enterprise testing and pre development en
The other scheme is to build a logical environment isolation. We only need to deploy the canary version of the service. When the traffic flows on the call link, the gateway, each middleware and each micro service passing through will identify the canary traffic and dynamically forward it to the canary version of the corresponding service. As shown below:
-
+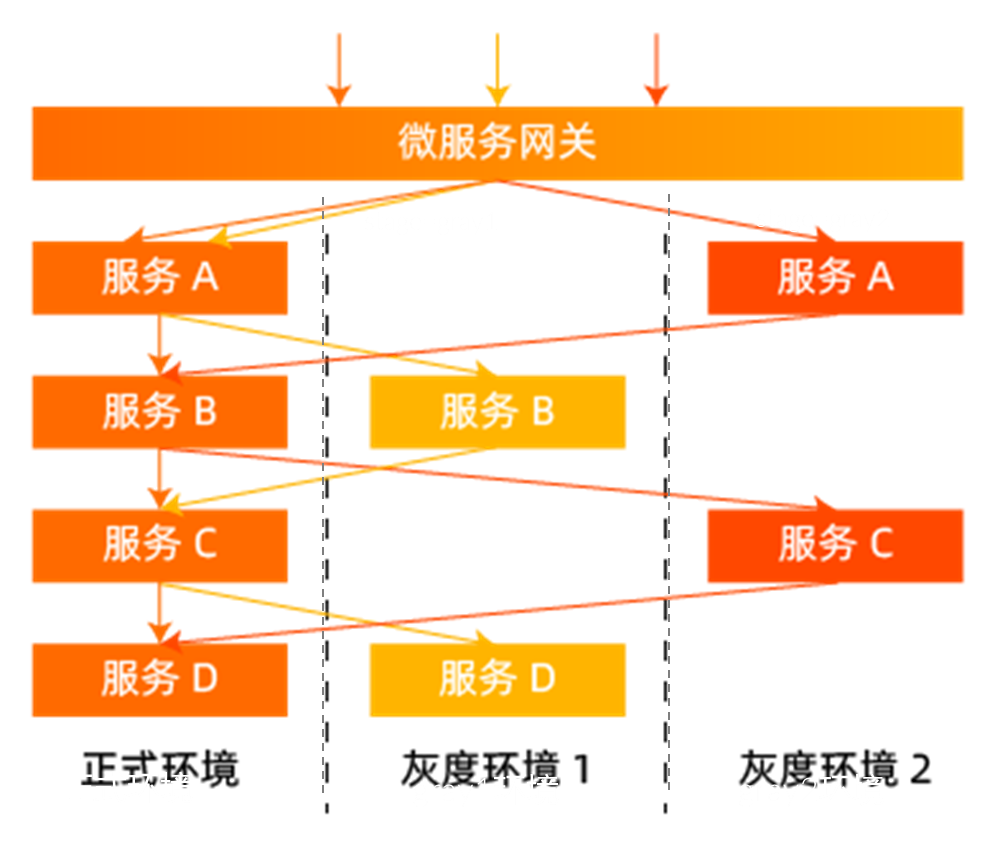
The above figure can well show the effect of this scheme. We use different colors to represent the canary traffic of different versions. It can be seen that both the microservice gateway and the microservice itself need to identify the traffic and make dynamic decisions according to the governance rules. When the service version changes, the forwarding of this call link will also change in real time. Compared with the canary deployment built by machines, this scheme can not only save a l [...]
@@ -111,7 +111,7 @@ ingress-apisix
4. Access APISIX Dashboard via `{slb-ip}:9000`.
-
+
#### Step 2: Enable microservice governance
@@ -125,7 +125,7 @@ Deploy three applications A, B, and C in Alibaba cloud container service. Each a
In some scenarios, the baseline environment and gray environment on the line can be distinguished by different domain names. Gray environment has a separate domain name that can be configured. Suppose we visit www.gray.com to request gray environment, visit www.base.com is the baseline environment.
-
+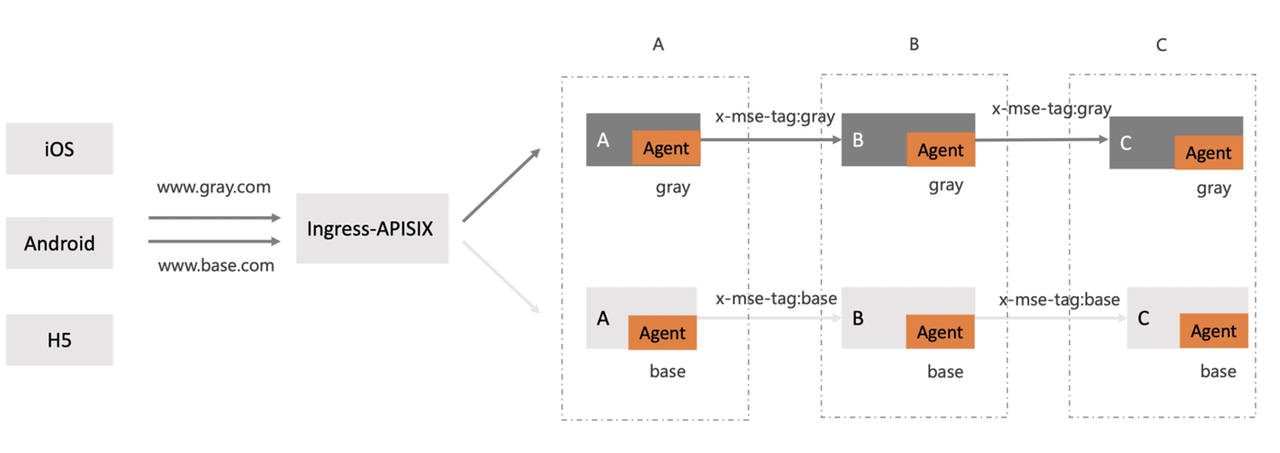
Call the link `Ingress-nginx - > A - > B - > C`, where a can be a `spring-boot` application.
@@ -214,7 +214,7 @@ Agray[172.18.144.16] -> Bgray[172.18.144.57] -> Cgray[172.18.144.157]%
Some clients can't rewrite the domain name. Users hope to visit `www.demo.com` routes to the gray environment by passing in different parameters. For example, in the following figure, the gray environment is accessed through the request parameter `env=gray`.
-
+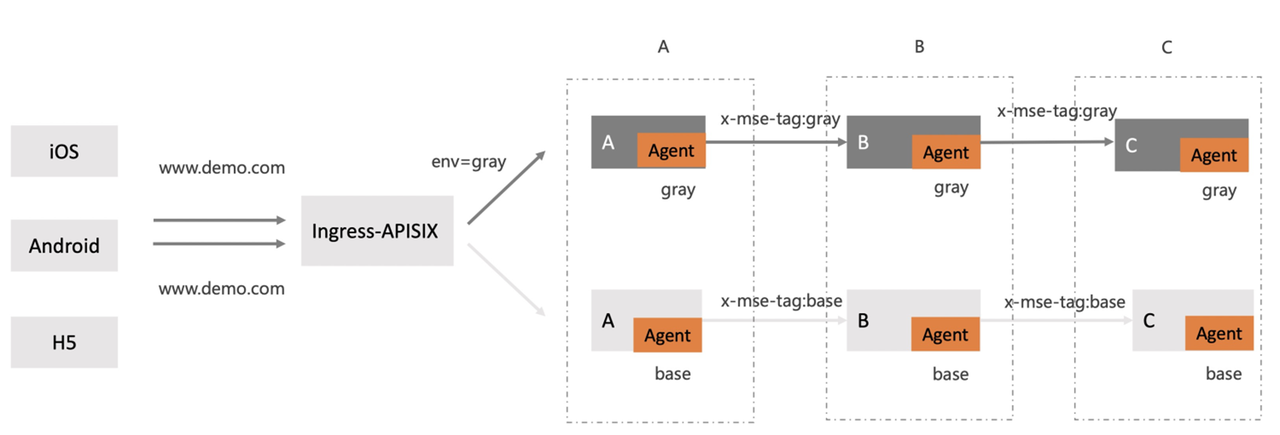
Call the link ingress apisik - > A - > b - > C, where a can be a spring boot application.
@@ -254,7 +254,7 @@ Then configure the route corresponding to the `base`:
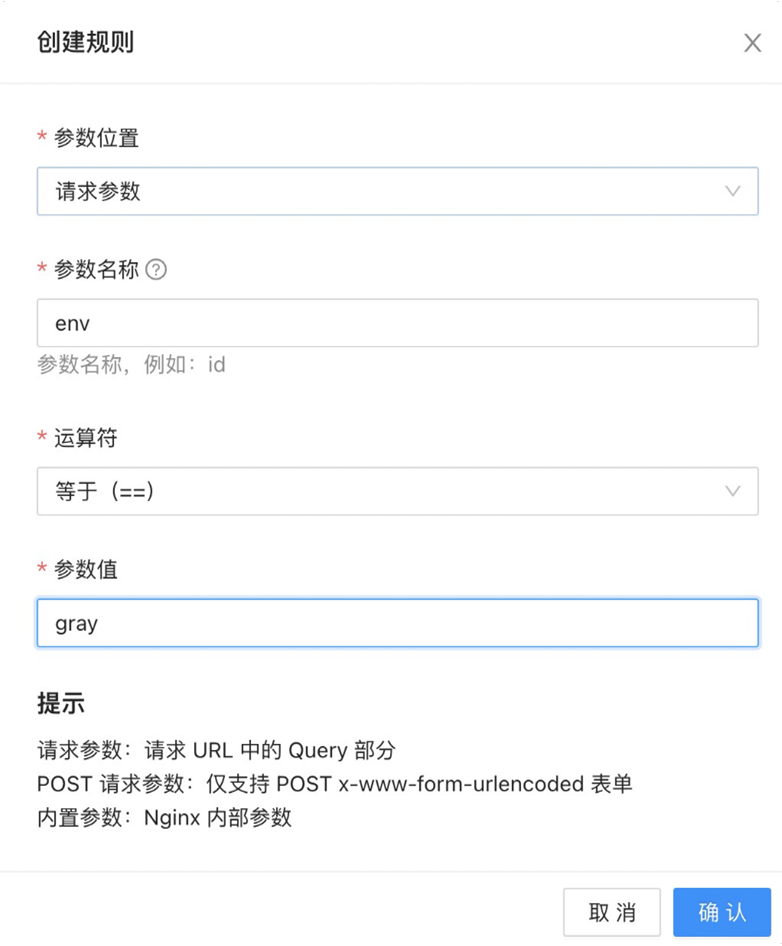
Configure the route corresponding to `gray`, as shown in the following figure:
-
+
```json
{
diff --git a/website/i18n/zh/docusaurus-plugin-content-blog/2022/06/14/automated-operation-base-apache-apisix.md b/website/i18n/zh/docusaurus-plugin-content-blog/2022/06/14/automated-operation-base-apache-apisix.md
index 119da7da80c..92593b8c135 100644
--- a/website/i18n/zh/docusaurus-plugin-content-blog/2022/06/14/automated-operation-base-apache-apisix.md
+++ b/website/i18n/zh/docusaurus-plugin-content-blog/2022/06/14/automated-operation-base-apache-apisix.md
@@ -2,7 +2,7 @@
title: "基于 Apache APISIX 的自动化运维平台"
authors:
- name: "陈庆"
- title: "Author"
+ title: "Author"
url: "https://github.com/chenqing24"
image_url: "https://avatars.githubusercontent.com/u/3502467?v=4"
- name: "韩飞"
@@ -11,10 +11,10 @@ authors:
image_url: "https://github.com/hf400159.png"
keywords:
- Apache APISIX
-- API 网关
-- 自动化
-- 运维
-- 微服务
+- API 网关
+- 自动化
+- 运维
+- 微服务
- 权限
description: 本文由前同程数科运维经理陈庆介绍了如何基于 Apache APISIX 实现自动化运维平台。
tags: [Technology]
@@ -36,7 +36,7 @@ tags: [Technology]
自动化运维平台整体架构图如下:
-
+
- 存储层:核心是 CMDB,主要功能是记录和管理组织业务和 IT 资源的属性,以及其它们之间的关系。不但负责所有业务变更的起始状态查询,而且所有的业务资源的变更都要反馈记录在其中,实现业务标准规范的管控。存储层也包含一些权限管理的数据、业务工单的流转数据以及监控告警的时序数据;
@@ -73,7 +73,7 @@ tags: [Technology]
对于所有的 Web 框架,用户登录是一个必选项,接下来我将为大家介绍此场景。
-
+
首先,我们需要了解下场景中,我们的使用的相关组件,第一个就是访问的前端,这个是在网关之外的,其次使用 APISIX 云原生 API 网关作为业务边界。再之后的 Auth 服务,它是自定义开发的微服务,作用是校验前端的 URL 请求和用户登录请求,并对通过认证的用户发放 Token。LDAP 中存放的是公司内部的密码信息。CMDB 存储的是一些业务的相关信息,包括组织结构,可以访问的权限的一些组织信息,最后是前端需要访问的页面。
@@ -87,11 +87,11 @@ tags: [Technology]
通过上述的描述,相信大家已经对正常的请求流程有了一定的理解,接下来将为大家介绍下如何判断这些用户权限不足的场景。在运维平台中,如果有涉及到数据变更的操作,必须要携带 Token,当这个 Token 被 ACL 的接口验证无权访问后,就会直接返回一个禁止访问的页面,让前端进行处理。以下是用户登录及权限验证场景的具体流程和其中更使用的相关组件。
-
+
### 新业务微服务接入
-
+
在日常工作,我们经常会上线一些微服务,那么如何让这个微服务接入自动化运维平台呢?
@@ -105,7 +105,7 @@ tags: [Technology]
通过上述的场景描述,相信大家已经对整套体系有了大概的认识,接下来为大家介绍下部分技术细节。
-
+
因为 APISIX 是基于 NGINX + Lua 实现的,所以部分功能需要通过 NGINX 的库来实现。从上图中,我们可以看到各种 Lua 脚本可以在哪些点切入到 NGINX 当中。在本文中,主要是为大家介绍 Rewrite/Access 以及 Content 阶段可以进行的操作。
diff --git a/website/i18n/zh/docusaurus-plugin-content-blog/2022/06/14/how-mse-supports-canary-release-with-apache-apisix.md b/website/i18n/zh/docusaurus-plugin-content-blog/2022/06/14/how-mse-supports-canary-release-with-apache-apisix.md
index 1ece8e1b0e2..b55b433299c 100644
--- a/website/i18n/zh/docusaurus-plugin-content-blog/2022/06/14/how-mse-supports-canary-release-with-apache-apisix.md
+++ b/website/i18n/zh/docusaurus-plugin-content-blog/2022/06/14/how-mse-supports-canary-release-with-apache-apisix.md
@@ -10,9 +10,9 @@ authors:
keywords:
- Apache APISIX
- API 网关
-- 阿里云
+- 阿里云
- 微服务
-- MSE
+- MSE
- 流量
description: 本篇文章描述了阿里云微服务引擎 MSE 如何基于 Apache APISIX 灵活的路由能力,配合 MSE 全链路灰度能力,通过极简的配置与无代码侵入的方式,来实现全链路灰度,释放基于 APISIX 的微服务架构的新价值。
tags: [User Case]
@@ -52,7 +52,7 @@ Apache APISIX 是一个开源的云原生 API 网关,作为 API 网关,它
物理环境隔离,其实就是通过增加机器的方式来搭建真正意义上的流量隔离。
-
+
该方案需要为灰度的服务搭建一套网络隔离、资源独立的环境,并在其中部署服务的灰度版本。由于与正式环境隔离,正式环境中的其他服务无法访问到需要灰度的服务,所以需要在灰度环境中冗余部署 这些线上服务,以便整个调用链路正常进行流量转发。此外,注册中心等一些其他依赖的中间件组件也需要冗余部署在灰度环境中,保证微服务之间的可见性问题,确保获取的节点 IP 地址只属于当前的网络环境。
@@ -62,7 +62,7 @@ Apache APISIX 是一个开源的云原生 API 网关,作为 API 网关,它
另一种方案是构建逻辑上的环境隔离,我们只需部署服务的灰度版本,流量在调用链路上流转时,由经过的网关、各个中间件以及各个微服务来识别灰度流量,并动态转发至对应服务的灰度版本。如下图:
-
+
上图可以很好展示这种方案的效果,我们用不同的颜色来表示不同版本的灰度流量,可以看出无论是微服务网关还是微服务本身都需要识别流量,根据治理规则做出动态决策。当服务版本发生变化时,这个调用链路的转发也会实时改变。相比于利用机器搭建的灰度环境,这种方案不仅可以节省大量的机器成 本和运维人力,而且可以帮助开发者实时快速的对线上流量进行精细化的全链路控制。
@@ -107,7 +107,7 @@ ingress-apisix
3. 安装完成后,可以绑定一个 SLB。
4. 通过 `{slb-ip}:9000` 访问 APISIX Dashboard。
-
+
#### 第二步:开启微服务治理
@@ -121,7 +121,7 @@ ingress-apisix
在部分场景下,可以通过不同的域名来区分线上基线环境和灰度环境。灰度环境有单独的域名可以配置,假设我们通过访问 [www.gray.com](http://www.gray.com/) 来请求灰度环境,访问 [www.base.com](http://www.base.com/) 走基线环境。
-
+
调用链路 `Ingress-nginx -> A -> B -> C`,其中 A 可以是一个 `spring-boot` 的应用。
@@ -209,7 +209,7 @@ Agray[172.18.144.16] -> Bgray[172.18.144.57] -> Cgray[172.18.144.157]%
有些客户端无法改写域名,希望能访问 `www.demo.com` 通过传入不同的参数来路由到灰度环境。例如下图中,通过 `env=gray` 这个请求参数,来访问灰度环境。
-
+
调用链路 `Ingress-APISIX -> A -> B -> C`,其中 A 可以是一个 `spring-boot` 的应用。
@@ -248,7 +248,7 @@ Agray[172.18.144.16] -> Bgray[172.18.144.57] -> Cgray[172.18.144.157]%
进行 `gray` 对应的路由配置,如下图所示:
-
+
```JSON
{