You are viewing a plain text version of this content. The canonical link for it is here.
Posted to notifications@apisix.apache.org by GitBox <gi...@apache.org> on 2021/11/30 10:29:13 UTC
[GitHub] [apisix] deepzz0 opened a new issue #5650: request help: etcd tls connect handshake failed
deepzz0 opened a new issue #5650:
URL: https://github.com/apache/apisix/issues/5650
### Issue description
```
2021/11/30 10:19:20 [warn] 45#45: *75201 [lua] v3.lua:631: request_chunk(): https://172.19.125.95:2379: handshake failed. Retrying, context: ngx.timer
2021/11/30 10:19:20 [error] 48#48: *75191 SSL_do_handshake() failed (SSL: error:14094412:SSL routines:ssl3_read_bytes:sslv3 alert bad certificate:SSL alert number 42), context: ngx.timer
```
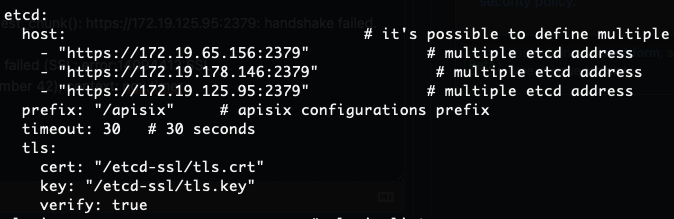
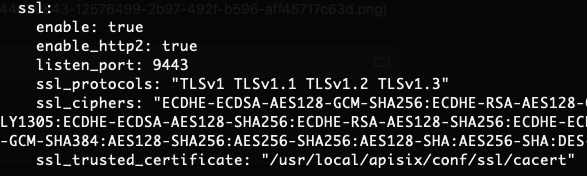
Above is my configuration, I can confirm that the certificate is ok. I saw the previous issue said openResty does not support mTLS?
### Environment
- apisix version (cmd: `apisix version`): 2.10.0
- OS (cmd: `uname -a`):
- OpenResty / Nginx version (cmd: `nginx -V` or `openresty -V`):
- etcd version, if have (cmd: run `curl http://127.0.0.1:9090/v1/server_info` to get the info from server-info API):
- apisix-dashboard version, if have:
- the plugin runner version, if the issue is about a plugin runner (cmd: depended on the kind of runner):
- luarocks version, if the issue is about installation (cmd: `luarocks --version`):
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] deepzz0 commented on issue #5650: request help: etcd tls connect handshake failed
Posted by GitBox <gi...@apache.org>.
deepzz0 commented on issue #5650:
URL: https://github.com/apache/apisix/issues/5650#issuecomment-985227784
@shuaijinchao @tokers @tzssangglass My certificate is in compliance, the X509 SAN has the relevant IP
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] shuaijinchao commented on issue #5650: request help: etcd tls connect handshake failed
Posted by GitBox <gi...@apache.org>.
shuaijinchao commented on issue #5650:
URL: https://github.com/apache/apisix/issues/5650#issuecomment-982541116
Is the ca certificate configured? refer to: https://github.com/apache/apisix/blob/master/t/cli/test_etcd_mtls.sh
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] shuaijinchao commented on issue #5650: request help: etcd tls connect handshake failed
Posted by GitBox <gi...@apache.org>.
shuaijinchao commented on issue #5650:
URL: https://github.com/apache/apisix/issues/5650#issuecomment-982574246
refer to: https://github.com/apache/apisix/issues/5155
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] deepzz0 commented on issue #5650: request help: etcd tls connect handshake failed
Posted by GitBox <gi...@apache.org>.
deepzz0 commented on issue #5650:
URL: https://github.com/apache/apisix/issues/5650#issuecomment-987496965
@tokers It means I didn't provide the client certificate, when i use `-cert` and `-key` in openssl, it's ok.
`Certificate host Mismatch` is an error reported by the client when trying to verify the server certificate. I will do more verification in my spare time to confirm the problem.
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] tzssangglass commented on issue #5650: request help: etcd tls connect handshake failed
Posted by GitBox <gi...@apache.org>.
tzssangglass commented on issue #5650:
URL: https://github.com/apache/apisix/issues/5650#issuecomment-983222695
e.g.: https://github.com/apache/apisix/blob/b4921c3a1919a7722b54393ed7c7e81825ca9d2c/t/cli/test_etcd_mtls.sh#L164-L172
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] deepzz0 commented on issue #5650: request help: etcd tls connect handshake failed
Posted by GitBox <gi...@apache.org>.
deepzz0 commented on issue #5650:
URL: https://github.com/apache/apisix/issues/5650#issuecomment-982541062
Upgrading to Apisix version 2.11.0 has been resolved, but but a new error appeared:
```
11/30 11:16:28 [warn] 49#49: *22332 [lua] v3.lua:151: _request_uri(): https://172.19.65.156:2379: certificate host mismatch. Retrying, context: ngx.timer
2021/11/30 11:16:28 [warn] 49#49: *22332 [lua] v3.lua:151: _request_uri(): https://172.19.65.156:2379: certificate host mismatch. Retrying, context: ngx.timer
2021/11/30 11:16:28 [warn] 49#49: *22332 [lua] health_check.lua:90: report_failure(): update endpoint: https://172.19.65.156:2379 to unhealthy, context: ngx.timer
```
My config:
```
etcd:
host: # it's possible to define multiple etcd hosts addresses of the same etcd cluster.
- "https://172.19.65.156:2379" # multiple etcd address
- "https://172.19.178.146:2379" # multiple etcd address
- "https://172.19.125.95:2379" # multiple etcd address
prefix: "/apisix" # apisix configurations prefix
timeout: 30 # 30 seconds
tls:
cert: "/etcd-ssl/tls.crt"
key: "/etcd-ssl/tls.key"
verify: true
```
my etcd cert:
```
09v3 extensions:
X509v3 Key Usage: critical
Digital Signature, Key Encipherment
X509v3 Extended Key Usage:
TLS Web Server Authentication, TLS Web Client Authentication
X509v3 Basic Constraints: critical
CA:FALSE
X509v3 Subject Key Identifier:
94:03:8D:57:B1:80:16:B1:24:F1:FB:54:84:48:D9:85:3D:50:A5:1A
X509v3 Authority Key Identifier:
keyid:D8:91:86:C9:95:9D:40:22:31:17:18:30:8C:0E:90:2A:AD:07:84:31
X509v3 Subject Alternative Name:
IP Address:172.19.65.156, IP Address:172.19.125.95, IP Address:172.19.178.146, IP Address:127.0.0.1
```
what's wrong?
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] hctech edited a comment on issue #5650: request help: etcd tls connect handshake failed
Posted by GitBox <gi...@apache.org>.
hctech edited a comment on issue #5650:
URL: https://github.com/apache/apisix/issues/5650#issuecomment-1079672618
1. use api7/apisix-base:1.19.9.1.4 as base image to build,api7/apisix-base:1.19.9.1.4 image use `RESTY_OPENSSL_VERSION="1.1.1g"`;
2. set etcd tls verify: false;
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] tokers commented on issue #5650: request help: etcd tls connect handshake failed
Posted by GitBox <gi...@apache.org>.
tokers commented on issue #5650:
URL: https://github.com/apache/apisix/issues/5650#issuecomment-986172595
I forget the details about lua-resty-http, I'm not sure whether it will set the SNI if the node is pure IP.
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] deepzz0 commented on issue #5650: request help: etcd tls connect handshake failed
Posted by GitBox <gi...@apache.org>.
deepzz0 commented on issue #5650:
URL: https://github.com/apache/apisix/issues/5650#issuecomment-986382468
> If so, the TLS handshaking should succeed, @deepzz0 Could you try to capture some TLS handshaking packages?
Now config:

Log:
```
2021/12/06 02:24:14 [warn] 49#49: *14344 [lua] v3.lua:647: request_chunk(): https://192.168.252.154:2379: certificate host mismatch. Retrying, context: ngx.timer
2021/12/06 02:24:14 [warn] 49#49: *14357 [lua] v3.lua:647: request_chunk(): https://192.168.252.154:2379: certificate host mismatch. Retrying, context: ngx.timer
2021/12/06 02:24:14 [warn] 49#49: *14319 [lua] health_check.lua:90: report_failure(): update endpoint: https://192.168.252.154:2379 to unhealthy, context: ngx.timer
2021/12/06 02:24:14 [warn] 49#49: *14319 [lua] v3.lua:647: request_chunk(): https://192.168.252.154:2379: certificate host mismatch. Retrying, context: ngx.timer
2021/12/06 02:24:14 [warn] 49#49: *14319 [lua] v3.lua:647: request_chunk(): has no healthy etcd endpoint available. Retrying, context: ngx.timer
2021/12/06 02:24:14 [error] 49#49: *14319 [lua] config_etcd.lua:563: no healthy etcd endpoint available, next retry after 64s, context: ngx.timer
2021/12/06 02:24:14 [warn] 49#49: *14344 [lua] v3.lua:647: request_chunk(): https://192.168.252.154:2379: certificate host mismatch. Retrying, context: ngx.timer
```
OpenSSL Hanshak:
```
[root@k8s-master0 ~]# openssl s_client -host 192.168.252.154 -port 2379 -verify_ip 192.168.252.154 -CAfile /etc/kubernetes/ssl/ca.pem
CONNECTED(00000003)
depth=1 C = CN, ST = HangZhou, L = XS, O = k8s, OU = System, CN = kubernetes
verify return:1
depth=0 C = CN, ST = HangZhou, L = XS, O = k8s, OU = System, CN = etcd
verify return:1
140718298392464:error:14094412:SSL routines:ssl3_read_bytes:sslv3 alert bad certificate:s3_pkt.c:1493:SSL alert number 42
140718298392464:error:140790E5:SSL routines:ssl23_write:ssl handshake failure:s23_lib.c:177:
---
Certificate chain
0 s:/C=CN/ST=HangZhou/L=XS/O=k8s/OU=System/CN=etcd
i:/C=CN/ST=HangZhou/L=XS/O=k8s/OU=System/CN=kubernetes
---
Server certificate
-----BEGIN CERTIFICATE-----
MIID8DCCAtigAwIBAgIUBABLfsUNcRp+7uMwZCAArGw8aBowDQYJKoZIhvcNAQEL
BQAwYTELMAkGA1UEBhMCQ04xETAPBgNVBAgTCEhhbmdaaG91MQswCQYDVQQHEwJY
UzEMMAoGA1UEChMDazhzMQ8wDQYDVQQLEwZTeXN0ZW0xEzARBgNVBAMTCmt1YmVy
bmV0ZXMwIBcNMjEwNDI3MDMxODAwWhgPMjA3MTA0MTUwMzE4MDBaMFsxCzAJBgNV
BAYTAkNOMREwDwYDVQQIEwhIYW5nWmhvdTELMAkGA1UEBxMCWFMxDDAKBgNVBAoT
A2s4czEPMA0GA1UECxMGU3lzdGVtMQ0wCwYDVQQDEwRldGNkMIIBIjANBgkqhkiG
9w0BAQEFAAOCAQ8AMIIBCgKCAQEA0e5PUK0J7PNnvreEbg5ui9H1H+7NoJWAtSK8
wVp/+ESDoERur+VVA+6zRDtPuF4q/dEIYIsu2lvrDD7ROt8zXCixyPmHsr0ez9O+
AZ4iVJX47Y9USohQOWmuxaH1KuaNB5xKTt3ORHf2LTY+X8FTYaxziBMvGhhRi6VS
KzcPFM8g4ABosFXptGhAhQSSl2IXYaBe6IdVHiD26KEYZBI/wr5i+ZSI3I9fQSIm
Oa5pO/GjhwgKG3YYNoYPvEV0+DnZWqqt7bx9xyO+aAneEmMHYFZEgyJ7X+KFSTK5
ypAznfFkqyuHr3M4xLmixsy5WVYfAhJm/8JyeVzYG41A5r8puwIDAQABo4GjMIGg
MA4GA1UdDwEB/wQEAwIFoDAdBgNVHSUEFjAUBggrBgEFBQcDAQYIKwYBBQUHAwIw
DAYDVR0TAQH/BAIwADAdBgNVHQ4EFgQUv3bFYCUZyKwPkTK8fSws/qzcKtswHwYD
VR0jBBgwFoAUu27ktPy6PVEypELIfgjAmEabUvYwIQYDVR0RBBowGIcEwKj8mocE
wKj8q4cEwKj8vYcEfwAAATANBgkqhkiG9w0BAQsFAAOCAQEAMHv4GGyULdF7bs91
9kejDSFjI0a0od4Tk99UXAeovCVQq5yG5B/y00dbn+PKwpofRu+2UAhwnHpCVAWS
zFplf8Wjma2NJ0+C8HiZCGm2qBJBZr5ZTTzP395XhA8iPur6oVdTu9YG4ucRvtHx
zfK6q6VGF9MXSpC0DdYrKtFOxCI3NrC6VUYxsBPdpA2oJdL8bjdLNz5onjobzPum
FblN7O3O8NBaFK03WzS0iko4taKewnAs+L3nYWPb/Xwl55BAqXNevaA1V427s3G0
AFqMCPo+BFl2i3B1YKSEsKUTovuHrqpS8QmTXHiWzV3lPCoEyHW/yuLbJ3m91d5a
GQQWCA==
-----END CERTIFICATE-----
subject=/C=CN/ST=HangZhou/L=XS/O=k8s/OU=System/CN=etcd
issuer=/C=CN/ST=HangZhou/L=XS/O=k8s/OU=System/CN=kubernetes
---
Acceptable client certificate CA names
/C=CN/ST=HangZhou/L=XS/O=k8s/OU=System/CN=kubernetes
Client Certificate Types: RSA sign, ECDSA sign
Requested Signature Algorithms: RSA+SHA256:ECDSA+SHA256:RSA+SHA384:ECDSA+SHA384:RSA+SHA512:ECDSA+SHA512:RSA+SHA1:ECDSA+SHA1
Shared Requested Signature Algorithms: RSA+SHA256:ECDSA+SHA256:RSA+SHA384:ECDSA+SHA384:RSA+SHA512:ECDSA+SHA512:RSA+SHA1:ECDSA+SHA1
Peer signing digest: SHA512
Server Temp Key: ECDH, P-256, 256 bits
---
SSL handshake has read 1572 bytes and written 138 bytes
---
New, TLSv1/SSLv3, Cipher is ECDHE-RSA-AES256-GCM-SHA384
Server public key is 2048 bit
Secure Renegotiation IS supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
SSL-Session:
Protocol : TLSv1.2
Cipher : ECDHE-RSA-AES256-GCM-SHA384
Session-ID:
Session-ID-ctx:
Master-Key: A3D512591F3CFFD01CA7DB451232941064E25C70A6191A54DBB4BD3D5AFE5B0E6E8E74747D4F665694FBECB39484A2B2
Key-Arg : None
Krb5 Principal: None
PSK identity: None
PSK identity hint: None
Start Time: 1638757343
Timeout : 300 (sec)
Verify return code: 0 (ok)
---
```
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] tokers commented on issue #5650: request help: etcd tls connect handshake failed
Posted by GitBox <gi...@apache.org>.
tokers commented on issue #5650:
URL: https://github.com/apache/apisix/issues/5650#issuecomment-987486570
> > Is this a self-signed certificate or signed by a private CA? Have you configured the `ssl_trusted_certificate` option?
>
> Yes, it's self-signed. You can see the configuration above, `ssl_trusted_certificate` has been set.
>
> If `verify` is set to true, an error "Certificate host Mismatch.",But I have no problem passing OpenSSL authentication
Your OpenSSL authentication also reports a bad certificate alert:
> verify return:1
140718298392464:error:14094412:SSL routines:ssl3_read_bytes:sslv3 alert bad certificate:s3_pkt.c:1493:SSL alert number 42
140718298392464:error:140790E5:SSL routines:ssl23_write:ssl handshake failure:s23_lib.c:177:
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] tzssangglass commented on issue #5650: request help: etcd tls connect handshake failed
Posted by GitBox <gi...@apache.org>.
tzssangglass commented on issue #5650:
URL: https://github.com/apache/apisix/issues/5650#issuecomment-985273079
> @shuaijinchao @tokers @tzssangglass My certificate is in compliance, the X509 SAN has the relevant IP
so?
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] tokers removed a comment on issue #5650: request help: etcd tls connect handshake failed
Posted by GitBox <gi...@apache.org>.
tokers removed a comment on issue #5650:
URL: https://github.com/apache/apisix/issues/5650#issuecomment-986172345
@deepzz0 Please read our replies carefully.
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] tokers commented on issue #5650: request help: etcd tls connect handshake failed
Posted by GitBox <gi...@apache.org>.
tokers commented on issue #5650:
URL: https://github.com/apache/apisix/issues/5650#issuecomment-983196264
@deepzz0 Configure the SNI setting in etcd section.
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] tokers commented on issue #5650: request help: etcd tls connect handshake failed
Posted by GitBox <gi...@apache.org>.
tokers commented on issue #5650:
URL: https://github.com/apache/apisix/issues/5650#issuecomment-986172654
@deepzz0 Could you try to preserve only one node in the etcd host and set the SNI to its IP address and check out the result?
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] tokers commented on issue #5650: request help: etcd tls connect handshake failed
Posted by GitBox <gi...@apache.org>.
tokers commented on issue #5650:
URL: https://github.com/apache/apisix/issues/5650#issuecomment-986343505
If so, the TLS handshaking should succeed, @deepzz0 Could you try to capture some TLS handshaking packages?
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] tokers commented on issue #5650: request help: etcd tls connect handshake failed
Posted by GitBox <gi...@apache.org>.
tokers commented on issue #5650:
URL: https://github.com/apache/apisix/issues/5650#issuecomment-986172345
@deepzz0 Please read our replies carefully.
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] tzssangglass commented on issue #5650: request help: etcd tls connect handshake failed
Posted by GitBox <gi...@apache.org>.
tzssangglass commented on issue #5650:
URL: https://github.com/apache/apisix/issues/5650#issuecomment-986230349
see more: https://github.com/apache/apisix/issues/5155#issuecomment-929948164
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] tzssangglass commented on issue #5650: request help: etcd tls connect handshake failed
Posted by GitBox <gi...@apache.org>.
tzssangglass commented on issue #5650:
URL: https://github.com/apache/apisix/issues/5650#issuecomment-986752194
you can specify the SNI for etcd, as mentioned above.
see more: https://github.com/apache/apisix/issues/5155#issuecomment-929948164
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] tzssangglass commented on issue #5650: request help: etcd tls connect handshake failed
Posted by GitBox <gi...@apache.org>.
tzssangglass commented on issue #5650:
URL: https://github.com/apache/apisix/issues/5650#issuecomment-986175190
> 我忘记了关于lua-resty-http的细节,我不确定如果节点是纯IP的它是否会设置SNI。
see: https://github.com/api7/lua-resty-etcd/pull/146#discussion_r724843510
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] hctech commented on issue #5650: request help: etcd tls connect handshake failed
Posted by GitBox <gi...@apache.org>.
hctech commented on issue #5650:
URL: https://github.com/apache/apisix/issues/5650#issuecomment-1079672618
use api7/apisix-base:1.19.9.1.4 as base image to build, set etcd tls verify: false
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] tokers commented on issue #5650: request help: etcd tls connect handshake failed
Posted by GitBox <gi...@apache.org>.
tokers commented on issue #5650:
URL: https://github.com/apache/apisix/issues/5650#issuecomment-1080073556
> @tokers It means I didn't provide the client certificate, when i use `-cert` and `-key` in openssl, it's ok. `Certificate host Mismatch` is an error reported by the client when trying to verify the server certificate. I will do more verification in my spare time to confirm the problem.
Just like @hctech , If your ETCD certificate was signed by private CA, you can either:
1. disable ETCD TLS Verify option in APISIX config.yaml, or
2. add the ETCD CA certificate to the CA bundle and specified it in `ssl_trusted_certificate` option.
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] deepzz0 commented on issue #5650: request help: etcd tls connect handshake failed
Posted by GitBox <gi...@apache.org>.
deepzz0 commented on issue #5650:
URL: https://github.com/apache/apisix/issues/5650#issuecomment-986700762
> Is this a self-signed certificate or signed by a private CA? Have you configured the `ssl_trusted_certificate` option?
Yes, it's self-signed. You can see the configuration above, `ssl_trusted_certificate` has been set.
If `verify` is set to true, an error "Certificate host Mismatch.",But I have no problem passing OpenSSL authentication
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] tokers commented on issue #5650: request help: etcd tls connect handshake failed
Posted by GitBox <gi...@apache.org>.
tokers commented on issue #5650:
URL: https://github.com/apache/apisix/issues/5650#issuecomment-986595093
Is this a self-signed certificate or signed by a private CA? Have you configured the `ssl_trusted_certificate` option?
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] deepzz0 commented on issue #5650: request help: etcd tls connect handshake failed
Posted by GitBox <gi...@apache.org>.
deepzz0 commented on issue #5650:
URL: https://github.com/apache/apisix/issues/5650#issuecomment-982544938
> Is the ca certificate configured? refer to: https://github.com/apache/apisix/blob/master/t/cli/test_etcd_mtls.sh
The first problem is solved, but a new error appeared: certificate host mismatch.
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] deepzz0 edited a comment on issue #5650: request help: etcd tls connect handshake failed
Posted by GitBox <gi...@apache.org>.
deepzz0 edited a comment on issue #5650:
URL: https://github.com/apache/apisix/issues/5650#issuecomment-982541062
Upgrading to Apisix version 2.11.0 has been resolved, but but a new error appeared:
```
11/30 11:16:28 [warn] 49#49: *22332 [lua] v3.lua:151: _request_uri(): https://172.19.65.156:2379: certificate host mismatch. Retrying, context: ngx.timer
2021/11/30 11:16:28 [warn] 49#49: *22332 [lua] v3.lua:151: _request_uri(): https://172.19.65.156:2379: certificate host mismatch. Retrying, context: ngx.timer
2021/11/30 11:16:28 [warn] 49#49: *22332 [lua] health_check.lua:90: report_failure(): update endpoint: https://172.19.65.156:2379 to unhealthy, context: ngx.timer
```
My config:
```
etcd:
host: # it's possible to define multiple etcd hosts addresses of the same etcd cluster.
- "https://172.19.65.126:2379" # multiple etcd address
- "https://172.19.178.136:2379" # multiple etcd address
- "https://172.19.125.105:2379" # multiple etcd address
prefix: "/apisix" # apisix configurations prefix
timeout: 30 # 30 seconds
tls:
cert: "/etcd-ssl/tls.crt"
key: "/etcd-ssl/tls.key"
verify: true
```
my etcd cert:
```
09v3 extensions:
X509v3 Key Usage: critical
Digital Signature, Key Encipherment
X509v3 Extended Key Usage:
TLS Web Server Authentication, TLS Web Client Authentication
X509v3 Basic Constraints: critical
CA:FALSE
X509v3 Subject Key Identifier:
94:03:8D:57:B1:80:16:B1:24:F1:FB:54:84:48:D9:85:3D:50:A5:1A
X509v3 Authority Key Identifier:
keyid:D8:91:86:C9:95:9D:40:22:31:17:18:30:8C:0E:90:2A:AD:07:84:31
X509v3 Subject Alternative Name:
IP Address:172.19.65.126, IP Address:172.19.178.136, IP Address:172.19.125.105, IP Address:127.0.0.1
```
what's wrong?
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] tzssangglass commented on issue #5650: request help: etcd tls connect handshake failed
Posted by GitBox <gi...@apache.org>.
tzssangglass commented on issue #5650:
URL: https://github.com/apache/apisix/issues/5650#issuecomment-1079717776
> 1. use api7/apisix-base:1.19.9.1.4 as base image to build,api7/apisix-base:1.19.9.1.4 image use `RESTY_OPENSSL_VERSION="1.1.1g"`;
> 2. set etcd tls verify: false;
If there is a similar problem, please give a detailed reproduction use case so that I can reproduce it.
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org