You are viewing a plain text version of this content. The canonical link for it is here.
Posted to notifications@apisix.apache.org by GitBox <gi...@apache.org> on 2021/10/17 00:38:14 UTC
[GitHub] [apisix] haowang-pony opened a new issue #5253: request help: Apisix use as apisix ingress controller and integrate with keycloak
haowang-pony opened a new issue #5253:
URL: https://github.com/apache/apisix/issues/5253
### Issue description
Currently I want to use apisix in k8s as ingress-controller and I expose apisix gateway as Nodeport such that the service outside the kubenetes could visit the apisix.
And I also want to integrate keycloak with apisix. The keycloak was deployed in the outside the k8s. Therefore I have such architecture.
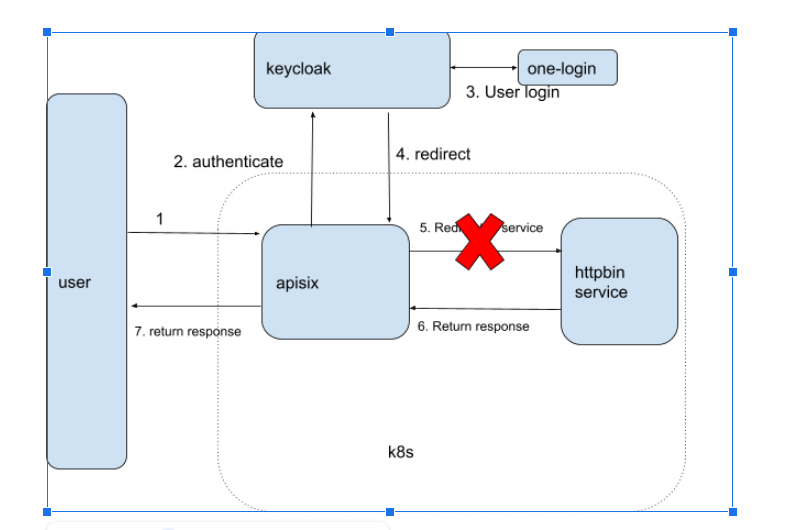
But I met a problem: after receiving redrect request from keycloak, the apisix couldn't redirect the url to service. And apisix just send the request back to keycloak and then keycloak send request back to apisix. Threfore I would have such error p`onyai.onelogin.com redirected you too many times. `
I checked the codebase and found [such comment](https://github.com/apache/apisix/blob/153e643674f13df98fb0929085ff61240aa73c66/apisix/plugins/openid-connect.lua#L294). And I checked the request to has already set access token in the cookies. I'm not sure whether I messed some configs or my usage is not allowed. If my usage is not allowed, how to use apisix as ingress-controller and integrate with keycloak outside the k8s?
Thanks in advance!
### Environment
- apisix version (cmd: `apisix version`): 1.2.0
- OS (cmd: `uname -a`):
- OpenResty / Nginx version (cmd: `nginx -V` or `openresty -V`):
- etcd version, if have (cmd: run `curl http://127.0.0.1:9090/v1/server_info` to get the info from server-info API):
- apisix-dashboard version, if have:
- the plugin runner version, if the issue is about a plugin runner (cmd: depended on the kind of runner):
- luarocks version, if the issue is about installation (cmd: `luarocks --version`):
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] haowang-pony commented on issue #5253: request help: Apisix use as apisix ingress controller and integrate with keycloak
Posted by GitBox <gi...@apache.org>.
haowang-pony commented on issue #5253:
URL: https://github.com/apache/apisix/issues/5253#issuecomment-944869303
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] haowang-pony edited a comment on issue #5253: request help: Apisix use as apisix ingress controller and integrate with keycloak
Posted by GitBox <gi...@apache.org>.
haowang-pony edited a comment on issue #5253:
URL: https://github.com/apache/apisix/issues/5253#issuecomment-945332261
> `authz-keycloak` alse connect with keycloak server, take a look at:https://github.com/apache/apisix/blob/master/docs/en/latest/plugins/authz-keycloak.md#examples
Seems we have some gap for this. Let me illustrate my questions again:
1. I never said the `auth-keycloak` couldn't connet to keycloak. My meaning is if I want to use `auth-keycloak` plugin, the request from client to apisix has to add access token in header.
I also checked [code](https://github.com/apache/apisix/blob/c46213a6e2e579f59473a0145940bbe05a0aebfb/apisix/plugins/authz-keycloak.lua#L693). T**his plugin did check the jwt token firstly. This is not what I want.**
I want to implement this architecture: The user don't need to add jwt token when talk with apisix. After receive request from user, the apisix could ask keycloak and onelogin to authenticate this request. And then froward request back to apisix. The apisix checked the jwt token already in header and redirect the request to service.
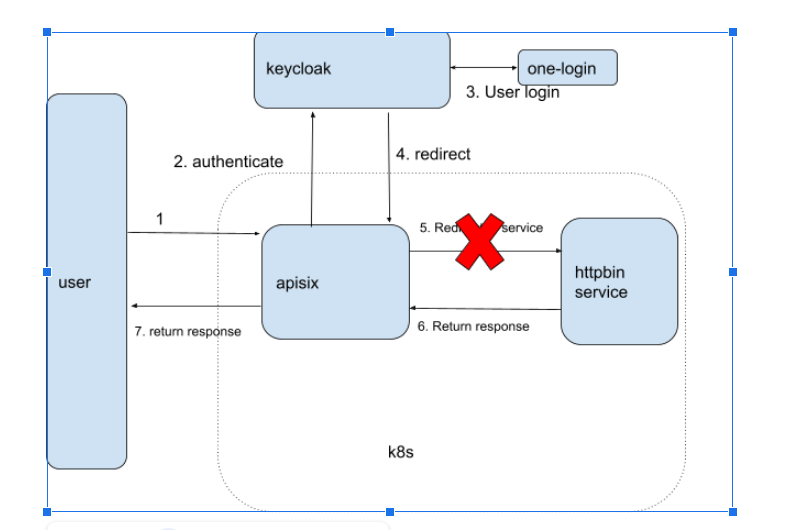
**Therefore, I think the `auth-keycloak` is not work for my case.**
2. I think the `openid-connect` is suitable plugin for my usage after reading [this article](https://apisix.apache.org/blog/2021/08/25/Using-the-Apache-APISIX-OpenID-Connect-Plugin-for-Centralized-Authentication/).
As for `openid-connect`, it doesn't require me add jwt token when user first talk to apisix.
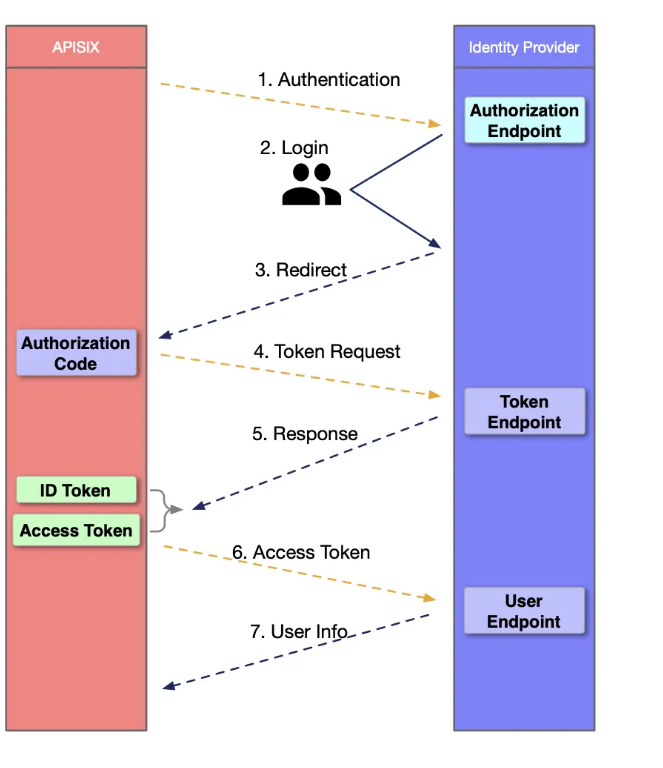
Actually I care more about the second question which is the question I want to ask in this pr. **I just want to whether openid-connect could read jwt token from cookie or not.** If not, could I come up with this feature request? For your convenience, the related code could be found at here https://github.com/apache/apisix/blob/153e643674f13df98fb0929085ff61240aa73c66/apisix/plugins/openid-connect.lua#L294.
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] haowang-pony removed a comment on issue #5253: request help: Apisix use as apisix ingress controller and integrate with keycloak
Posted by GitBox <gi...@apache.org>.
haowang-pony removed a comment on issue #5253:
URL: https://github.com/apache/apisix/issues/5253#issuecomment-944873149
I just tried the authz-keycloak, but met the same problem. the request was redirect between apisix and keycloak back and forth. And I checked request cookies already has access-token.
Here is my config
```
apiVersion: apisix.apache.org/v2beta1
kind: ApisixRoute
metadata:
name: httpbin-route
namespace: ingress-apisix
spec:
http:
- name: httpbin
match:
hosts:
- httpbin.k8s.fr.corp.pony.ai
paths:
- /*
backends:
- serviceName: httpbin
servicePort: 80
plugins:
- name: authz-keycloak
enable: true
config:
client_id: apisix
client_secret: ""
discovery: ***/.well-known/openid-configuration
policy_enforcement_mode: PERMISSIVE
```
I'm wondering the authz-keycloak and openid-connect plugin only check the access-token in header but failed to check the access token in cookie. Because if I set the access-token into request header, the workflow works very well.
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] haowang-pony edited a comment on issue #5253: request help: Apisix use as apisix ingress controller and integrate with keycloak
Posted by GitBox <gi...@apache.org>.
haowang-pony edited a comment on issue #5253:
URL: https://github.com/apache/apisix/issues/5253#issuecomment-945332261
> `authz-keycloak` alse connect with keycloak server, take a look at:https://github.com/apache/apisix/blob/master/docs/en/latest/plugins/authz-keycloak.md#examples
Seems we have some gap for this. Let me illustrate my questions again:
1. I never said the `auth-keycloak` couldn't connet to keycloak. I said the request from client to apisix need add jwt token in header. 
I also checked [code](https://github.com/apache/apisix/blob/c46213a6e2e579f59473a0145940bbe05a0aebfb/apisix/plugins/authz-keycloak.lua#L693). This plugin did check the jwt token firstly. This is not what I want.
I want to implement this architecture: The user don't need to add jwt token when talk with apisix. After receive request from user, the apisix could ask keycloak and onelogin to authenticate this request. And then froward request back to apisix. The apisix checked the jwt token already in header and redirect the request to service.

**After reading code, I think the `auth-keycloak` is not work for my case.**
2. I think the `openid-connect` is good plugin for my usage after reading [this article](https://apisix.apache.org/blog/2021/08/25/Using-the-Apache-APISIX-OpenID-Connect-Plugin-for-Centralized-Authentication/).
As for `openid-connect`, it doesn't require me add jwt token when user first talk to apisix.

Actually I care more about the second question which is the question I want to ask in this pr. **I just want to whether openid-connect could read jwt token from cookie or not.** If not, could I come up with this feature request?
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] haowang-pony edited a comment on issue #5253: request help: Apisix use as apisix ingress controller and integrate with keycloak
Posted by GitBox <gi...@apache.org>.
haowang-pony edited a comment on issue #5253:
URL: https://github.com/apache/apisix/issues/5253#issuecomment-945332261
> `authz-keycloak` alse connect with keycloak server, take a look at:https://github.com/apache/apisix/blob/master/docs/en/latest/plugins/authz-keycloak.md#examples
Seems we have some gap for this. Let me illustrate my questions again:
1. I never said the `auth-keycloak` couldn't connet to keycloak. I said the request from client to apisix need add jwt token in header. 
I also checked [code](https://github.com/apache/apisix/blob/c46213a6e2e579f59473a0145940bbe05a0aebfb/apisix/plugins/authz-keycloak.lua#L693). This plugin did check the jwt token firstly. This is not what I want.
I want to implement this architecture: The user don't need to add jwt token when talk with apisix. After receive request from user, the apisix could ask keycloak and onelogin to authenticate this request. And then froward request back to apisix. The apisix checked the jwt token already in header and redirect the request to service.

**After reading code, I think the `auth-keycloak` is not work for my case.**
2. I think the `openid-connect` is good plugin for my usage after reading [this article](https://apisix.apache.org/blog/2021/08/25/Using-the-Apache-APISIX-OpenID-Connect-Plugin-for-Centralized-Authentication/).
As for `openid-connect`, it doesn't require me add jwt token when user first talk to apisix.

Actually I care more about the second question which is the question I want to ask in this pr. **I just want to whether openid-connect could read jwt token from cookie or not.** If not, could I come up with this feature request?
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] tzssangglass commented on issue #5253: request help: Apisix use as apisix ingress controller and integrate with keycloak
Posted by GitBox <gi...@apache.org>.
tzssangglass commented on issue #5253:
URL: https://github.com/apache/apisix/issues/5253#issuecomment-944863587
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] haowang-pony edited a comment on issue #5253: request help: Apisix use as apisix ingress controller and integrate with keycloak
Posted by GitBox <gi...@apache.org>.
haowang-pony edited a comment on issue #5253:
URL: https://github.com/apache/apisix/issues/5253#issuecomment-945332261
> `authz-keycloak` alse connect with keycloak server, take a look at:https://github.com/apache/apisix/blob/master/docs/en/latest/plugins/authz-keycloak.md#examples
Seems we have some gap for this. Let me illustrate my questions again:
1. I never said the `auth-keycloak` couldn't connet to keycloak. My meaning is if I want to use `auth-keycloak` plugin, the request from client to apisix has to add access token in header.

I also checked [code](https://github.com/apache/apisix/blob/c46213a6e2e579f59473a0145940bbe05a0aebfb/apisix/plugins/authz-keycloak.lua#L693). **This plugin did check the jwt token firstly. This is not what I want.**
I want to implement this architecture: The user don't need to add jwt token when talk with apisix. After receive request from user, the apisix could ask keycloak and onelogin to authenticate this request. And then froward request back to apisix. The apisix checked the jwt token already in header and redirect the request to service.

**Therefore, I think the `auth-keycloak` is not work for my case.**
2. I think the `openid-connect` is suitable plugin for my usage after reading [this article](https://apisix.apache.org/blog/2021/08/25/Using-the-Apache-APISIX-OpenID-Connect-Plugin-for-Centralized-Authentication/).
As for `openid-connect`, it doesn't require me add jwt token when user first talk to apisix.

Actually I care more about the second question which is the question I want to ask in this pr. **I just want to whether openid-connect could read jwt token from cookie or not.** If not, could I come up with this feature request? For your convenience, the related code could be found at here https://github.com/apache/apisix/blob/153e643674f13df98fb0929085ff61240aa73c66/apisix/plugins/openid-connect.lua#L294.
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] haowang-pony edited a comment on issue #5253: request help: Apisix use as apisix ingress controller and integrate with keycloak
Posted by GitBox <gi...@apache.org>.
haowang-pony edited a comment on issue #5253:
URL: https://github.com/apache/apisix/issues/5253#issuecomment-945332261
> `authz-keycloak` alse connect with keycloak server, take a look at:https://github.com/apache/apisix/blob/master/docs/en/latest/plugins/authz-keycloak.md#examples
Seems we have some gap for this. Let me illustrate my questions again:
1. I never said the `auth-keycloak` couldn't connet to keycloak. I said the request from client to apisix need add jwt token in header. 
I also checked [code](https://github.com/apache/apisix/blob/c46213a6e2e579f59473a0145940bbe05a0aebfb/apisix/plugins/authz-keycloak.lua#L693). This plugin did check the jwt token firstly. This is not what I want.
I want to implement this architecture: The user don't need to add jwt token when talk with apisix. After receive request from user, the apisix could ask keycloak and onelogin to authenticate this request. And then froward request back to apisix. The apisix checked the jwt token already in header and redirect the request to service.

**Therefore, I think the `auth-keycloak` is not work for my case.**
2. I think the `openid-connect` is suitable plugin for my usage after reading [this article](https://apisix.apache.org/blog/2021/08/25/Using-the-Apache-APISIX-OpenID-Connect-Plugin-for-Centralized-Authentication/).
As for `openid-connect`, it doesn't require me add jwt token when user first talk to apisix.

Actually I care more about the second question which is the question I want to ask in this pr. **I just want to whether openid-connect could read jwt token from cookie or not.** If not, could I come up with this feature request?
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] haowang-pony edited a comment on issue #5253: request help: Apisix use as apisix ingress controller and integrate with keycloak
Posted by GitBox <gi...@apache.org>.
haowang-pony edited a comment on issue #5253:
URL: https://github.com/apache/apisix/issues/5253#issuecomment-945332261
> `authz-keycloak` alse connect with keycloak server, take a look at:https://github.com/apache/apisix/blob/master/docs/en/latest/plugins/authz-keycloak.md#examples
Seems we have some gap for this. Let me illustrate my questions again:
1. I never said the `auth-keycloak` couldn't connet to keycloak. I said the request from client to apisix need add jwt token in header. 
I also checked [code](https://github.com/apache/apisix/blob/c46213a6e2e579f59473a0145940bbe05a0aebfb/apisix/plugins/authz-keycloak.lua#L693). This plugin did check the jwt token firstly. This is not what I want.
I want to implement this architecture: The user don't need to add jwt token when talk with apisix. After receive request from user, the apisix could ask keycloak and onelogin to authenticate this request. And then froward request back to apisix. The apisix checked the jwt token already in header and redirect the request to service.

**Therefore, I think the `auth-keycloak` is not work for my case.**
2. I think the `openid-connect` is suitable plugin for my usage after reading [this article](https://apisix.apache.org/blog/2021/08/25/Using-the-Apache-APISIX-OpenID-Connect-Plugin-for-Centralized-Authentication/).
As for `openid-connect`, it doesn't require me add jwt token when user first talk to apisix.

Actually I care more about the second question which is the question I want to ask in this pr. **I just want to whether openid-connect could read jwt token from cookie or not.** If not, could I come up with this feature request? For your convenience, the related code could be found at here https://github.com/apache/apisix/blob/153e643674f13df98fb0929085ff61240aa73c66/apisix/plugins/openid-connect.lua#L294.
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] haowang-pony edited a comment on issue #5253: request help: Apisix use as apisix ingress controller and integrate with keycloak
Posted by GitBox <gi...@apache.org>.
haowang-pony edited a comment on issue #5253:
URL: https://github.com/apache/apisix/issues/5253#issuecomment-944876448
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] haowang-pony commented on issue #5253: request help: Apisix use as apisix ingress controller and integrate with keycloak
Posted by GitBox <gi...@apache.org>.
haowang-pony commented on issue #5253:
URL: https://github.com/apache/apisix/issues/5253#issuecomment-945332261
> `authz-keycloak` alse connect with keycloak server, take a look at:https://github.com/apache/apisix/blob/master/docs/en/latest/plugins/authz-keycloak.md#examples
Seems we have some gap for this. Let me illustrate my questions again:
1. I never said the `auth-keycloak` couldn't connet to keycloak. I said the request from client to apisix need add jwt token in header. 
I also checked [code](https://github.com/apache/apisix/blob/c46213a6e2e579f59473a0145940bbe05a0aebfb/apisix/plugins/authz-keycloak.lua#L693). This plugin did check the jwt token firstly. This is not what I want.
I want to implement this architecture: The user don't need to add jwt token when talk with apisix. After receive request from user, the apisix could ask keycloak and onelogin to authenticate this request. And then froward request back to apisix. The apisix checked the jwt token already in header and redirect the request to service.

After reading code, I think the `auth-keycloak` is not work for my case.
2. I think the `openid-connect` is good plugin for my usage after reading [this article](https://apisix.apache.org/blog/2021/08/25/Using-the-Apache-APISIX-OpenID-Connect-Plugin-for-Centralized-Authentication/).
As for `openid-connect`, it doesn't require me add jwt token when user first talk to apisix.

Actually I care more about the second question which is the question I want to ask in this pr. **I just want to whether openid-connect could read jwt token from cookie or not.** If not, could I come up with this feature request?
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] haowang-pony edited a comment on issue #5253: request help: Apisix use as apisix ingress controller and integrate with keycloak
Posted by GitBox <gi...@apache.org>.
haowang-pony edited a comment on issue #5253:
URL: https://github.com/apache/apisix/issues/5253#issuecomment-945332261
> `authz-keycloak` alse connect with keycloak server, take a look at:https://github.com/apache/apisix/blob/master/docs/en/latest/plugins/authz-keycloak.md#examples
Seems we have some gap for this. Let me illustrate my questions again:
1. I never said the `auth-keycloak` couldn't connet to keycloak. I said the request from client to apisix need add jwt token in header. 
I also checked [code](https://github.com/apache/apisix/blob/c46213a6e2e579f59473a0145940bbe05a0aebfb/apisix/plugins/authz-keycloak.lua#L693). This plugin did check the jwt token firstly. This is not what I want.
I want to implement this architecture: The user don't need to add jwt token when talk with apisix. After receive request from user, the apisix could ask keycloak and onelogin to authenticate this request. And then froward request back to apisix. The apisix checked the jwt token already in header and redirect the request to service.

**Therefore, I think the `auth-keycloak` is not work for my case.**
2. I think the `openid-connect` is good plugin for my usage after reading [this article](https://apisix.apache.org/blog/2021/08/25/Using-the-Apache-APISIX-OpenID-Connect-Plugin-for-Centralized-Authentication/).
As for `openid-connect`, it doesn't require me add jwt token when user first talk to apisix.

Actually I care more about the second question which is the question I want to ask in this pr. **I just want to whether openid-connect could read jwt token from cookie or not.** If not, could I come up with this feature request?
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [apisix] tzssangglass commented on issue #5253: request help: Apisix use as apisix ingress controller and integrate with keycloak
Posted by GitBox <gi...@apache.org>.
tzssangglass commented on issue #5253:
URL: https://github.com/apache/apisix/issues/5253#issuecomment-945731698
> just want to whether openid-connect could read jwt token from cookie or not.
yes, see:https://github.com/apache/apisix/blob/master/docs/en/latest/plugins/openid-connect.md#modes-of-operation
refer to 1:https://github.com/apache/apisix/blob/e71052783c15b4ccccedd25e78a53de5c5787370/apisix/plugins/openid-connect.lua#L189
2:https://github.com/zmartzone/lua-resty-openidc/blob/5c8cb343131f20313f134023cf344ad7fb083077/lib/resty/openidc.lua#L1544
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org