You are viewing a plain text version of this content. The canonical link for it is here.
Posted to commits@airflow.apache.org by GitBox <gi...@apache.org> on 2022/03/15 17:38:03 UTC
[GitHub] [airflow] potiuk opened a new pull request #22292: Fail with error when extending image with pip run as root
potiuk opened a new pull request #22292:
URL: https://github.com/apache/airflow/pull/22292
The production docker image installs airflow with --user
flag for `airflow` user and all subsequent image extension
should be done using `airflow` user. It is very easy however,
to run `pip` as root user when you switched temporarily to the
root user for `apt` installation.
This PR makes the accidental `root` user run `pip` fail with
error and redirection to the documentation where it is explained
to the users that they should use `airflow` user for `pip` with
examples.
Fixes: #22250
<!--
Thank you for contributing! Please make sure that your code changes
are covered with tests. And in case of new features or big changes
remember to adjust the documentation.
Feel free to ping committers for the review!
In case of existing issue, reference it using one of the following:
closes: #ISSUE
related: #ISSUE
How to write a good git commit message:
http://chris.beams.io/posts/git-commit/
-->
---
**^ Add meaningful description above**
Read the **[Pull Request Guidelines](https://github.com/apache/airflow/blob/main/CONTRIBUTING.rst#pull-request-guidelines)** for more information.
In case of fundamental code change, Airflow Improvement Proposal ([AIP](https://cwiki.apache.org/confluence/display/AIRFLOW/Airflow+Improvements+Proposals)) is needed.
In case of a new dependency, check compliance with the [ASF 3rd Party License Policy](https://www.apache.org/legal/resolved.html#category-x).
In case of backwards incompatible changes please leave a note in [UPDATING.md](https://github.com/apache/airflow/blob/main/UPDATING.md).
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: commits-unsubscribe@airflow.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [airflow] github-actions[bot] commented on pull request #22292: Fail with error when extending image with pip run as root
Posted by GitBox <gi...@apache.org>.
github-actions[bot] commented on pull request #22292:
URL: https://github.com/apache/airflow/pull/22292#issuecomment-1068273443
The PR most likely needs to run full matrix of tests because it modifies parts of the core of Airflow. However, committers might decide to merge it quickly and take the risk. If they don't merge it quickly - please rebase it to the latest main at your convenience, or amend the last commit of the PR, and push it with --force-with-lease.
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: commits-unsubscribe@airflow.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [airflow] potiuk commented on pull request #22292: Fail with error when extending image with pip run as root
Posted by GitBox <gi...@apache.org>.
potiuk commented on pull request #22292:
URL: https://github.com/apache/airflow/pull/22292#issuecomment-1068278745
> This makes me think maybe pip should gain a flag that disables root invocation altogether, e.g. `pip --no-root` would refuse to do anything instead of warn if the uid is 0.
Yeah. Why not. As long as we can control it somehow. I do think rather than "policing" (and producing the warning) giving control to the users who are using `pip` as part of the pipeline is much better idea (but - as discussed for a long time, those power users of `pip` who have their own users should be able to control it.
The funny thing in this case that users are so used to the `root` warning that it did absolutely nothing to prevent the user to make the mistake. The user saw the "do not use pip as root` as warning but happily ignored it, and it require a slack conversation and close looking at the Dockerfile of the user to help him.
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: commits-unsubscribe@airflow.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [airflow] potiuk commented on pull request #22292: Fail with error when extending image with pip run as root
Posted by GitBox <gi...@apache.org>.
potiuk commented on pull request #22292:
URL: https://github.com/apache/airflow/pull/22292#issuecomment-1068265381
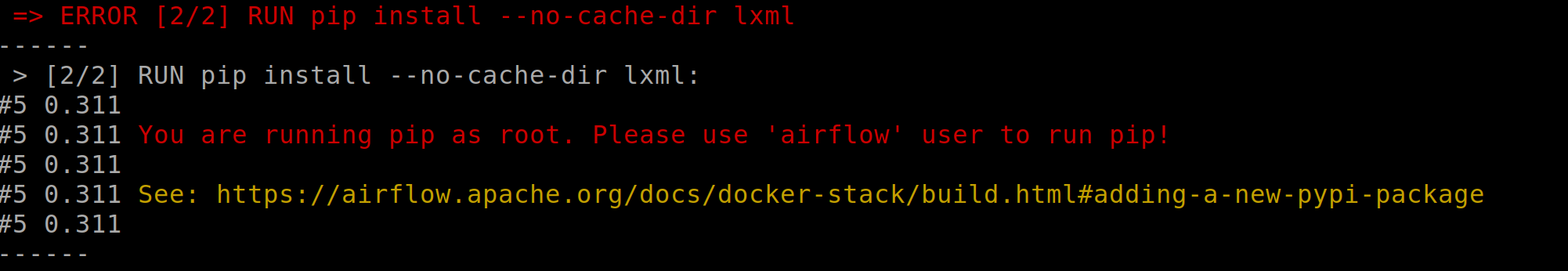
When you try to extend the image with `pip` as `root` user, you will get this now:
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: commits-unsubscribe@airflow.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [airflow] potiuk edited a comment on pull request #22292: Fail with error when extending image with pip run as root
Posted by GitBox <gi...@apache.org>.
potiuk edited a comment on pull request #22292:
URL: https://github.com/apache/airflow/pull/22292#issuecomment-1068278745
> This makes me think maybe pip should gain a flag that disables root invocation altogether, e.g. `pip --no-root` would refuse to do anything instead of warn if the uid is 0.
Yeah. Why not. As long as we can control it somehow. I do think rather than "policing" (and producing the warning) giving control to the users who are using `pip` as part of the pipeline is much better idea (but - as discussed for a long time, those power users of `pip` who have their own users should be able to control it).
The funny thing in this case that users are so used to the `root` warning that it did absolutely nothing to prevent the user to make the mistake. The user saw the "do not use pip as root` as warning but happily ignored it, and it require a slack conversation and close looking at the Dockerfile of the user to help him.
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: commits-unsubscribe@airflow.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [airflow] potiuk edited a comment on pull request #22292: Fail with error when extending image with pip run as root
Posted by GitBox <gi...@apache.org>.
potiuk edited a comment on pull request #22292:
URL: https://github.com/apache/airflow/pull/22292#issuecomment-1068278745
> This makes me think maybe pip should gain a flag that disables root invocation altogether, e.g. `pip --no-root` would refuse to do anything instead of warn if the uid is 0.
Yeah. Why not. As long as we can control it somehow. I do think rather than "policing" (and producing the warning) giving control to the users who are using `pip` as part of the pipeline is much better idea (but - as discussed for a long time, those power users of `pip` who have their own users should be able to control it).
The funny thing in this case that users are so used to the `root` warning that it did absolutely nothing to prevent the user to make the mistake. The user saw the "do not use pip as root` as warning but happily ignored it, and it required a slack conversation and close looking at the Dockerfile of the user to help him.
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: commits-unsubscribe@airflow.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [airflow] potiuk edited a comment on pull request #22292: Fail with error when extending image with pip run as root
Posted by GitBox <gi...@apache.org>.
potiuk edited a comment on pull request #22292:
URL: https://github.com/apache/airflow/pull/22292#issuecomment-1068278745
> This makes me think maybe pip should gain a flag that disables root invocation altogether, e.g. `pip --no-root` would refuse to do anything instead of warn if the uid is 0.
Yeah. Why not. As long as we can control it somehow. I do think rather than "policing" (and producing the warning) giving control to the users who are using `pip` as part of the pipeline is much better idea (but - as discussed for a long time, those power users of `pip` who have their own users should be able to control it).
The funny thing in this case that users are so used to the `root` warnings that it did absolutely nothing to prevent the user to make the mistake. The user saw the "do not use pip as root` as warning but happily ignored it, and it required a slack conversation and close looking at the Dockerfile of the user to help him.
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: commits-unsubscribe@airflow.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [airflow] potiuk merged pull request #22292: Fail with error when extending image with pip run as root
Posted by GitBox <gi...@apache.org>.
potiuk merged pull request #22292:
URL: https://github.com/apache/airflow/pull/22292
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: commits-unsubscribe@airflow.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org