You are viewing a plain text version of this content. The canonical link for it is here.
Posted to dev@kafka.apache.org by GitBox <gi...@apache.org> on 2021/12/14 16:32:42 UTC
[GitHub] [kafka-site] scott-confluent opened a new pull request #388: adding new CVEs to list
scott-confluent opened a new pull request #388:
URL: https://github.com/apache/kafka-site/pull/388
Per https://docs.google.com/document/d/1zar4nlhIQnDB7qm9i4RqFUFXM5pWP7_a0WERcLlR0Wo/edit#heading=h.jp7xjzp1clqe
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: dev-unsubscribe@kafka.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [kafka-site] scott-confluent commented on pull request #388: adding new CVEs to list
Posted by GitBox <gi...@apache.org>.
scott-confluent commented on pull request #388:
URL: https://github.com/apache/kafka-site/pull/388#issuecomment-994151250
@junrao @rhauch Does adding it here make sense?
<img width="1019" alt="Screen Shot 2021-12-14 at 6 59 27 PM" src="https://user-images.githubusercontent.com/66280178/146098304-984b64f1-4a58-4e53-b69a-4fb0d1fa1197.png">
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: dev-unsubscribe@kafka.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [kafka-site] rhauch edited a comment on pull request #388: adding new CVEs to list
Posted by GitBox <gi...@apache.org>.
rhauch edited a comment on pull request #388:
URL: https://github.com/apache/kafka-site/pull/388#issuecomment-994134387
As background for Connect:
* Connect runtime puts all JARs from each connector plugin on a separate classloader, and the Connect runtime nor other connector plugins have access to a plugin's JARs. This is why a connector plugin that includes a Log4J 2.x JAR
* Most connector implementations simply use the logging provided by the Connect runtime, which is Log4J 1.x regardless of the JARs included by connector plugins.
* However, if a connector plugins does include the Log4J 2.x JAR files, those JAR files will only be used if the connector implementation explicitly uses those APIs. There isn't a need to do this, but connectors are custom code and can do quite a bit.
We might consider adding something like this under the `CVE-2021-44228` section, which I hope conveys the limited scope of the risk:
> The Connect runtime of Apache Kafka allows users to install third party connector plugins. These connector plugins will use Connect runtime's Log4J 1.x by default, even when Log4J 1.x or 2.x JARs are inadvertently shipped with the connector plugin. Check with the vendor of any connector plugin that includes a Log4J 2.x JAR file.
Basically, AK is not responsible for third party connectors that users add to their Connect installations. But users should consult with the vendor of those third party connectors.
As for `CVE-2021-4104`, I think the existing wording applies to Connect just as well as every other part of AK, so IMO no changes are necessary to that section specifically for Connect.
Feel free to wordsmith as needed.
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: dev-unsubscribe@kafka.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [kafka-site] junrao commented on a change in pull request #388: adding new CVEs to list
Posted by GitBox <gi...@apache.org>.
junrao commented on a change in pull request #388:
URL: https://github.com/apache/kafka-site/pull/388#discussion_r768953613
##########
File path: cve-list.html
##########
@@ -9,6 +9,63 @@ <h1>Apache Kafka Security Vulnerabilities</h1>
This page lists all security vulnerabilities fixed in released versions of Apache Kafka.
+<h2><a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-44228">CVE-2021-44228</a>
+ Flaw in Apache Log4j logging library in versions from 2.0.0 and before 2.15.0</h2>
+
+ <p>Some components in Apache Kafka use <code>Log4j-v1.2.17</code> there is no dependence on <code>Log4j v2.*</code></p>
+
+ <p><a href="https://logging.apache.org/log4j/2.x/manual/lookups.html">Lookups feature</a> was introduced in Log4j v2.x in order to allow specifying Log4j configuration parameters in arbitrary locations (even outside of the configuration files). Log4j v1.x does not offer the same functionality and thus is not vulnerable to <a href="https://access.redhat.com/security/cve/cve-2021-44228">CVE-2021-44228</a>.</p>
+ <p>Users should NOT be impacted by this vulnerability</p>
+
+ <table class="data-table">
+ <tbody>
+ <tr>
+ <td>Versions affected</td>
+ <td>NA</td>
+ </tr>
+ <tr>
+ <td>Fixed versions</td>
+ <td>NA</td>
+ </tr>
+ <tr>
+ <td>Impact</td>
+ <td>NA</td>
+ </tr>
+ <tr>
+ <td>Issue announced</td>
+ <td>09 Dec 2021</td>
+ </tr>
+ </tbody>
+ </table>
+
+<h2><a href="https://access.redhat.com/security/cve/CVE-2021-4104">CVE-2021-4104</a>
+ Flaw in Apache Log4j logging library in versions 1.x</h2>
+
+ <p>Some components in Apache Kafka use <code>Log4j-v1.2.17</code></p>
Review comment:
How about the following?
"The following components in Apache Kafka use Log4j-v1.2.17: broker, controller, zookeeper, connect, mirrormaker and tools. Clients may also be configured to use Log4j-v1.2.17."
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: dev-unsubscribe@kafka.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [kafka-site] junrao commented on pull request #388: adding new CVEs to list
Posted by GitBox <gi...@apache.org>.
junrao commented on pull request #388:
URL: https://github.com/apache/kafka-site/pull/388#issuecomment-994141826
Thanks, @rhauch. The simpler version is probably enough. @scott-confluent : Could you add that?
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: dev-unsubscribe@kafka.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [kafka-site] junrao commented on a change in pull request #388: adding new CVEs to list
Posted by GitBox <gi...@apache.org>.
junrao commented on a change in pull request #388:
URL: https://github.com/apache/kafka-site/pull/388#discussion_r768987825
##########
File path: cve-list.html
##########
@@ -9,6 +9,63 @@ <h1>Apache Kafka Security Vulnerabilities</h1>
This page lists all security vulnerabilities fixed in released versions of Apache Kafka.
+<h2><a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-44228">CVE-2021-44228</a>
+ Flaw in Apache Log4j logging library in versions from 2.0.0 and before 2.15.0</h2>
+
+ <p>Some components in Apache Kafka use <code>Log4j-v1.2.17</code> there is no dependence on <code>Log4j v2.*</code></p>
+
+ <p><a href="https://logging.apache.org/log4j/2.x/manual/lookups.html">Lookups feature</a> was introduced in Log4j v2.x in order to allow specifying Log4j configuration parameters in arbitrary locations (even outside of the configuration files). Log4j v1.x does not offer the same functionality and thus is not vulnerable to <a href="https://access.redhat.com/security/cve/cve-2021-44228">CVE-2021-44228</a>.</p>
+ <p>Users should NOT be impacted by this vulnerability</p>
+
+ <table class="data-table">
+ <tbody>
+ <tr>
+ <td>Versions affected</td>
+ <td>NA</td>
+ </tr>
+ <tr>
+ <td>Fixed versions</td>
+ <td>NA</td>
+ </tr>
+ <tr>
+ <td>Impact</td>
+ <td>NA</td>
+ </tr>
+ <tr>
+ <td>Issue announced</td>
+ <td>09 Dec 2021</td>
+ </tr>
+ </tbody>
+ </table>
+
+<h2><a href="https://access.redhat.com/security/cve/CVE-2021-4104">CVE-2021-4104</a>
+ Flaw in Apache Log4j logging library in versions 1.x</h2>
+
+ <p>Some components in Apache Kafka use <code>Log4j-v1.2.17</code></p>
Review comment:
A minor change. "Client applications may also be configured to use Log4j-v1.x."
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: dev-unsubscribe@kafka.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [kafka-site] junrao merged pull request #388: adding new CVEs to list
Posted by GitBox <gi...@apache.org>.
junrao merged pull request #388:
URL: https://github.com/apache/kafka-site/pull/388
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: dev-unsubscribe@kafka.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [kafka-site] scott-confluent edited a comment on pull request #388: adding new CVEs to list
Posted by GitBox <gi...@apache.org>.
scott-confluent edited a comment on pull request #388:
URL: https://github.com/apache/kafka-site/pull/388#issuecomment-993980560
@junrao I have pushed all updates from the doc as well as your comments here
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: dev-unsubscribe@kafka.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [kafka-site] scott-confluent removed a comment on pull request #388: adding new CVEs to list
Posted by GitBox <gi...@apache.org>.
scott-confluent removed a comment on pull request #388:
URL: https://github.com/apache/kafka-site/pull/388#issuecomment-994121512
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: dev-unsubscribe@kafka.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [kafka-site] junrao commented on pull request #388: adding new CVEs to list
Posted by GitBox <gi...@apache.org>.
junrao commented on pull request #388:
URL: https://github.com/apache/kafka-site/pull/388#issuecomment-994163284
@scott-confluent : Thanks for the updated PR. LGTM
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: dev-unsubscribe@kafka.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [kafka-site] scott-confluent commented on a change in pull request #388: adding new CVEs to list
Posted by GitBox <gi...@apache.org>.
scott-confluent commented on a change in pull request #388:
URL: https://github.com/apache/kafka-site/pull/388#discussion_r768941484
##########
File path: cve-list.html
##########
@@ -9,6 +9,63 @@ <h1>Apache Kafka Security Vulnerabilities</h1>
This page lists all security vulnerabilities fixed in released versions of Apache Kafka.
+<h2><a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-44228">CVE-2021-44228</a>
+ Flaw in Apache Log4j logging library in versions from 2.0.0 and before 2.15.0</h2>
+
+ <p>Some components in Apache Kafka use <code>Log4j-v1.2.17</code> there is no dependence on <code>Log4j v2.*</code></p>
+
+ <p><a href="https://logging.apache.org/log4j/2.x/manual/lookups.html">Lookups feature</a> was introduced in Log4j v2.x in order to allow specifying Log4j configuration parameters in arbitrary locations (even outside of the configuration files). Log4j v1.x does not offer the same functionality and thus is not vulnerable to <a href="https://access.redhat.com/security/cve/cve-2021-44228">CVE-2021-44228</a>.</p>
+ <p>Users should NOT be impacted by this vulnerability</p>
+
+ <table class="data-table">
+ <tbody>
+ <tr>
+ <td>Versions affected</td>
+ <td>NA</td>
+ </tr>
+ <tr>
+ <td>Fixed versions</td>
+ <td>NA</td>
+ </tr>
+ <tr>
+ <td>Impact</td>
+ <td>NA</td>
+ </tr>
+ <tr>
+ <td>Issue announced</td>
+ <td>09 Dec 2021</td>
+ </tr>
+ </tbody>
+ </table>
+
+<h2><a href="https://access.redhat.com/security/cve/CVE-2021-4104">CVE-2021-4104</a>
+ Flaw in Apache Log4j logging library in versions 1.x</h2>
+
+ <p>Some components in Apache Kafka use <code>Log4j-v1.2.17</code></p>
Review comment:
How does something like this sound?
"Some components, including but not limited to: broker, controller, zookeeper, connect, mirrormaker, tools, and clients configured with log4j, use `Log4j-v1.2.17`"
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: dev-unsubscribe@kafka.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [kafka-site] scott-confluent commented on pull request #388: adding new CVEs to list
Posted by GitBox <gi...@apache.org>.
scott-confluent commented on pull request #388:
URL: https://github.com/apache/kafka-site/pull/388#issuecomment-993980560
@junrao I have pushed all updates from the doc as well as your comments here
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: dev-unsubscribe@kafka.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [kafka-site] scott-confluent commented on a change in pull request #388: adding new CVEs to list
Posted by GitBox <gi...@apache.org>.
scott-confluent commented on a change in pull request #388:
URL: https://github.com/apache/kafka-site/pull/388#discussion_r769105156
##########
File path: cve-list.html
##########
@@ -9,6 +9,70 @@ <h1>Apache Kafka Security Vulnerabilities</h1>
This page lists all security vulnerabilities fixed in released versions of Apache Kafka.
+<h2><a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-44228">CVE-2021-44228</a>
+ Flaw in Apache Log4j logging library in versions from 2.0.0 and before 2.15.0</h2>
+
+ <p>Some components in Apache Kafka use <code>Log4j-v1.2.17</code> there is no dependence on <code>Log4j v2.*</code></p>
+
+ <p><a href="https://logging.apache.org/log4j/2.x/manual/lookups.html">Lookups feature</a> was introduced in Log4j v2.x in order to allow specifying Log4j configuration parameters in arbitrary locations (even outside of the configuration files). Log4j v1.x does not offer the same functionality and thus is not vulnerable to <a href="https://access.redhat.com/security/cve/cve-2021-44228">CVE-2021-44228</a>.</p>
+ <p>Users should NOT be impacted by this vulnerability</p>
+
+ <table class="data-table">
+ <tbody>
+ <tr>
+ <td>Versions affected</td>
+ <td>org.apache.logging.log4j:log4j-core >=2.0-beta9 and < 2.15.0</td>
+ </tr>
+ <tr>
+ <td>Fixed versions</td>
+ <td>NA</td>
+ </tr>
+ <tr>
+ <td>Impact</td>
+ <td>NA</td>
+ </tr>
+ <tr>
+ <td>Issue announced</td>
+ <td>09 Dec 2021</td>
+ </tr>
+ </tbody>
+ </table>
+
+<h2><a href="https://access.redhat.com/security/cve/CVE-2021-4104">CVE-2021-4104</a>
+ Flaw in Apache Log4j logging library in versions 1.x</h2>
+
+ <p>The following components in Apache Kafka use <code>Log4j-v1.2.17</code>: broker, controller, zookeeper, connect, mirrormaker and tools. Clients may also be configured to use <code>Log4j-v1.2.17</code>.</p>
Review comment:
Updated. Thanks for clarifying
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: dev-unsubscribe@kafka.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [kafka-site] scott-confluent removed a comment on pull request #388: adding new CVEs to list
Posted by GitBox <gi...@apache.org>.
scott-confluent removed a comment on pull request #388:
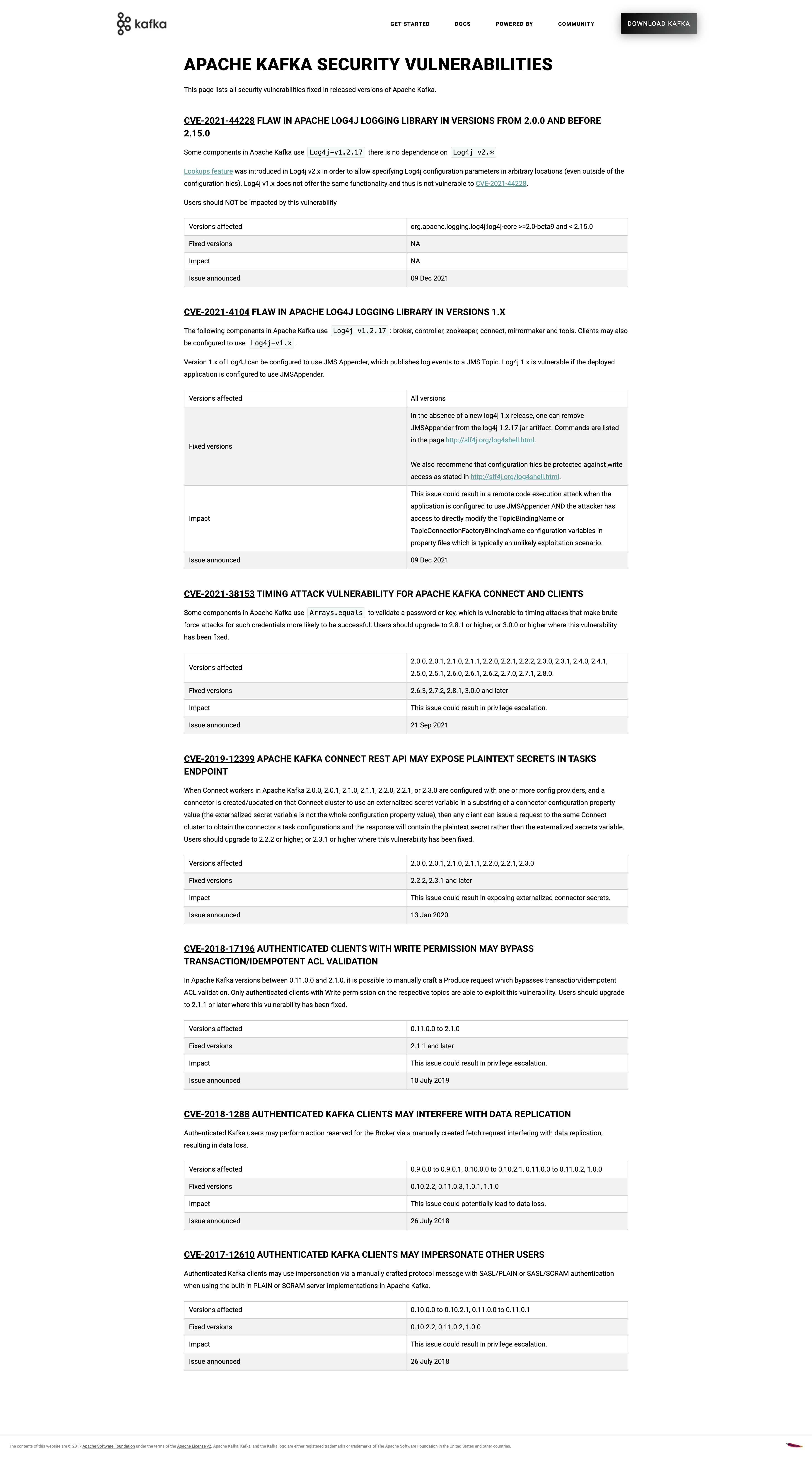
URL: https://github.com/apache/kafka-site/pull/388#issuecomment-993854475
We can't get a preview up, but here's the full page screenshot from my local:

--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: dev-unsubscribe@kafka.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [kafka-site] scott-confluent commented on pull request #388: adding new CVEs to list
Posted by GitBox <gi...@apache.org>.
scott-confluent commented on pull request #388:
URL: https://github.com/apache/kafka-site/pull/388#issuecomment-993960076
> Do we want to add a disclaimer that users need to check their connectors to see if it uses log4j2?
>
> Though the core library does not use this dependency, it is possible external connectors that use it could introduce vulnerabilities if they depend on the affected log4j2 version
@junrao what do you think?
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: dev-unsubscribe@kafka.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [kafka-site] scott-confluent commented on a change in pull request #388: adding new CVEs to list
Posted by GitBox <gi...@apache.org>.
scott-confluent commented on a change in pull request #388:
URL: https://github.com/apache/kafka-site/pull/388#discussion_r769068111
##########
File path: cve-list.html
##########
@@ -9,6 +9,63 @@ <h1>Apache Kafka Security Vulnerabilities</h1>
This page lists all security vulnerabilities fixed in released versions of Apache Kafka.
+<h2><a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-44228">CVE-2021-44228</a>
+ Flaw in Apache Log4j logging library in versions from 2.0.0 and before 2.15.0</h2>
+
+ <p>Some components in Apache Kafka use <code>Log4j-v1.2.17</code> there is no dependence on <code>Log4j v2.*</code></p>
+
+ <p><a href="https://logging.apache.org/log4j/2.x/manual/lookups.html">Lookups feature</a> was introduced in Log4j v2.x in order to allow specifying Log4j configuration parameters in arbitrary locations (even outside of the configuration files). Log4j v1.x does not offer the same functionality and thus is not vulnerable to <a href="https://access.redhat.com/security/cve/cve-2021-44228">CVE-2021-44228</a>.</p>
+ <p>Users should NOT be impacted by this vulnerability</p>
+
+ <table class="data-table">
+ <tbody>
+ <tr>
+ <td>Versions affected</td>
+ <td>NA</td>
+ </tr>
+ <tr>
+ <td>Fixed versions</td>
+ <td>NA</td>
+ </tr>
+ <tr>
+ <td>Impact</td>
+ <td>NA</td>
+ </tr>
+ <tr>
+ <td>Issue announced</td>
+ <td>09 Dec 2021</td>
+ </tr>
+ </tbody>
+ </table>
+
+<h2><a href="https://access.redhat.com/security/cve/CVE-2021-4104">CVE-2021-4104</a>
+ Flaw in Apache Log4j logging library in versions 1.x</h2>
+
+ <p>Some components in Apache Kafka use <code>Log4j-v1.2.17</code></p>
Review comment:
Is this to update the last sentence of the first paragraph?
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: dev-unsubscribe@kafka.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [kafka-site] junrao commented on a change in pull request #388: adding new CVEs to list
Posted by GitBox <gi...@apache.org>.
junrao commented on a change in pull request #388:
URL: https://github.com/apache/kafka-site/pull/388#discussion_r769082582
##########
File path: cve-list.html
##########
@@ -9,6 +9,70 @@ <h1>Apache Kafka Security Vulnerabilities</h1>
This page lists all security vulnerabilities fixed in released versions of Apache Kafka.
+<h2><a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-44228">CVE-2021-44228</a>
+ Flaw in Apache Log4j logging library in versions from 2.0.0 and before 2.15.0</h2>
+
+ <p>Some components in Apache Kafka use <code>Log4j-v1.2.17</code> there is no dependence on <code>Log4j v2.*</code></p>
+
+ <p><a href="https://logging.apache.org/log4j/2.x/manual/lookups.html">Lookups feature</a> was introduced in Log4j v2.x in order to allow specifying Log4j configuration parameters in arbitrary locations (even outside of the configuration files). Log4j v1.x does not offer the same functionality and thus is not vulnerable to <a href="https://access.redhat.com/security/cve/cve-2021-44228">CVE-2021-44228</a>.</p>
+ <p>Users should NOT be impacted by this vulnerability</p>
+
+ <table class="data-table">
+ <tbody>
+ <tr>
+ <td>Versions affected</td>
+ <td>org.apache.logging.log4j:log4j-core >=2.0-beta9 and < 2.15.0</td>
+ </tr>
+ <tr>
+ <td>Fixed versions</td>
+ <td>NA</td>
+ </tr>
+ <tr>
+ <td>Impact</td>
+ <td>NA</td>
+ </tr>
+ <tr>
+ <td>Issue announced</td>
+ <td>09 Dec 2021</td>
+ </tr>
+ </tbody>
+ </table>
+
+<h2><a href="https://access.redhat.com/security/cve/CVE-2021-4104">CVE-2021-4104</a>
+ Flaw in Apache Log4j logging library in versions 1.x</h2>
+
+ <p>The following components in Apache Kafka use <code>Log4j-v1.2.17</code>: broker, controller, zookeeper, connect, mirrormaker and tools. Clients may also be configured to use <code>Log4j-v1.2.17</code>.</p>
Review comment:
Clients may also be configured to use <code>Log4j-v1.2.17 => Clients may also be configured to use <code>Log4j-v1.x
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: dev-unsubscribe@kafka.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [kafka-site] scott-confluent commented on a change in pull request #388: adding new CVEs to list
Posted by GitBox <gi...@apache.org>.
scott-confluent commented on a change in pull request #388:
URL: https://github.com/apache/kafka-site/pull/388#discussion_r768958081
##########
File path: cve-list.html
##########
@@ -9,6 +9,63 @@ <h1>Apache Kafka Security Vulnerabilities</h1>
This page lists all security vulnerabilities fixed in released versions of Apache Kafka.
+<h2><a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-44228">CVE-2021-44228</a>
+ Flaw in Apache Log4j logging library in versions from 2.0.0 and before 2.15.0</h2>
+
+ <p>Some components in Apache Kafka use <code>Log4j-v1.2.17</code> there is no dependence on <code>Log4j v2.*</code></p>
+
+ <p><a href="https://logging.apache.org/log4j/2.x/manual/lookups.html">Lookups feature</a> was introduced in Log4j v2.x in order to allow specifying Log4j configuration parameters in arbitrary locations (even outside of the configuration files). Log4j v1.x does not offer the same functionality and thus is not vulnerable to <a href="https://access.redhat.com/security/cve/cve-2021-44228">CVE-2021-44228</a>.</p>
+ <p>Users should NOT be impacted by this vulnerability</p>
+
+ <table class="data-table">
+ <tbody>
+ <tr>
+ <td>Versions affected</td>
+ <td>NA</td>
+ </tr>
+ <tr>
+ <td>Fixed versions</td>
+ <td>NA</td>
+ </tr>
+ <tr>
+ <td>Impact</td>
+ <td>NA</td>
+ </tr>
+ <tr>
+ <td>Issue announced</td>
+ <td>09 Dec 2021</td>
+ </tr>
+ </tbody>
+ </table>
+
+<h2><a href="https://access.redhat.com/security/cve/CVE-2021-4104">CVE-2021-4104</a>
+ Flaw in Apache Log4j logging library in versions 1.x</h2>
+
+ <p>Some components in Apache Kafka use <code>Log4j-v1.2.17</code></p>
Review comment:
Here it is with both updates:
<img width="1024" alt="Screen Shot 2021-12-14 at 1 57 20 PM" src="https://user-images.githubusercontent.com/66280178/146062124-bc90d370-91ed-40e7-a0c6-771c0bf9d856.png">
##########
File path: cve-list.html
##########
@@ -9,6 +9,63 @@ <h1>Apache Kafka Security Vulnerabilities</h1>
This page lists all security vulnerabilities fixed in released versions of Apache Kafka.
+<h2><a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-44228">CVE-2021-44228</a>
+ Flaw in Apache Log4j logging library in versions from 2.0.0 and before 2.15.0</h2>
+
+ <p>Some components in Apache Kafka use <code>Log4j-v1.2.17</code> there is no dependence on <code>Log4j v2.*</code></p>
+
+ <p><a href="https://logging.apache.org/log4j/2.x/manual/lookups.html">Lookups feature</a> was introduced in Log4j v2.x in order to allow specifying Log4j configuration parameters in arbitrary locations (even outside of the configuration files). Log4j v1.x does not offer the same functionality and thus is not vulnerable to <a href="https://access.redhat.com/security/cve/cve-2021-44228">CVE-2021-44228</a>.</p>
+ <p>Users should NOT be impacted by this vulnerability</p>
+
+ <table class="data-table">
+ <tbody>
+ <tr>
+ <td>Versions affected</td>
+ <td>NA</td>
+ </tr>
+ <tr>
+ <td>Fixed versions</td>
+ <td>NA</td>
+ </tr>
+ <tr>
+ <td>Impact</td>
+ <td>NA</td>
+ </tr>
+ <tr>
+ <td>Issue announced</td>
+ <td>09 Dec 2021</td>
+ </tr>
+ </tbody>
+ </table>
+
+<h2><a href="https://access.redhat.com/security/cve/CVE-2021-4104">CVE-2021-4104</a>
+ Flaw in Apache Log4j logging library in versions 1.x</h2>
+
+ <p>Some components in Apache Kafka use <code>Log4j-v1.2.17</code></p>
+
+ <p>Version 1.x of Log4J can be configured to use JMS Appender, which publishes log events to a JMS Topic. Log4j 1.x is vulnerable if the deployed application is configured to use JMSAppender.</p>
+
+ <table class="data-table">
+ <tbody>
+ <tr>
+ <td>Versions affected</td>
+ <td>All versions</td>
+ </tr>
+ <tr>
+ <td>Fixed versions</td>
+ <td>NA</td>
Review comment:
Here it is with both updates:
<img width="1024" alt="Screen Shot 2021-12-14 at 1 57 20 PM" src="https://user-images.githubusercontent.com/66280178/146062124-bc90d370-91ed-40e7-a0c6-771c0bf9d856.png">
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: dev-unsubscribe@kafka.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [kafka-site] junrao commented on pull request #388: adding new CVEs to list
Posted by GitBox <gi...@apache.org>.
junrao commented on pull request #388:
URL: https://github.com/apache/kafka-site/pull/388#issuecomment-993922371
@ijuma : Does the content look good to you? Thanks.
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: dev-unsubscribe@kafka.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [kafka-site] scott-confluent commented on pull request #388: adding new CVEs to list
Posted by GitBox <gi...@apache.org>.
scott-confluent commented on pull request #388:
URL: https://github.com/apache/kafka-site/pull/388#issuecomment-994121512

--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: dev-unsubscribe@kafka.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [kafka-site] junrao commented on a change in pull request #388: adding new CVEs to list
Posted by GitBox <gi...@apache.org>.
junrao commented on a change in pull request #388:
URL: https://github.com/apache/kafka-site/pull/388#discussion_r768947897
##########
File path: cve-list.html
##########
@@ -9,6 +9,63 @@ <h1>Apache Kafka Security Vulnerabilities</h1>
This page lists all security vulnerabilities fixed in released versions of Apache Kafka.
+<h2><a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-44228">CVE-2021-44228</a>
+ Flaw in Apache Log4j logging library in versions from 2.0.0 and before 2.15.0</h2>
+
+ <p>Some components in Apache Kafka use <code>Log4j-v1.2.17</code> there is no dependence on <code>Log4j v2.*</code></p>
+
+ <p><a href="https://logging.apache.org/log4j/2.x/manual/lookups.html">Lookups feature</a> was introduced in Log4j v2.x in order to allow specifying Log4j configuration parameters in arbitrary locations (even outside of the configuration files). Log4j v1.x does not offer the same functionality and thus is not vulnerable to <a href="https://access.redhat.com/security/cve/cve-2021-44228">CVE-2021-44228</a>.</p>
+ <p>Users should NOT be impacted by this vulnerability</p>
+
+ <table class="data-table">
+ <tbody>
+ <tr>
+ <td>Versions affected</td>
+ <td>NA</td>
+ </tr>
+ <tr>
+ <td>Fixed versions</td>
+ <td>NA</td>
+ </tr>
+ <tr>
+ <td>Impact</td>
+ <td>NA</td>
+ </tr>
+ <tr>
+ <td>Issue announced</td>
+ <td>09 Dec 2021</td>
+ </tr>
+ </tbody>
+ </table>
+
+<h2><a href="https://access.redhat.com/security/cve/CVE-2021-4104">CVE-2021-4104</a>
+ Flaw in Apache Log4j logging library in versions 1.x</h2>
+
+ <p>Some components in Apache Kafka use <code>Log4j-v1.2.17</code></p>
+
+ <p>Version 1.x of Log4J can be configured to use JMS Appender, which publishes log events to a JMS Topic. Log4j 1.x is vulnerable if the deployed application is configured to use JMSAppender.</p>
+
+ <table class="data-table">
+ <tbody>
+ <tr>
+ <td>Versions affected</td>
+ <td>All versions</td>
+ </tr>
+ <tr>
+ <td>Fixed versions</td>
+ <td>NA</td>
Review comment:
Since we don't have a fix yet, perhaps we could add the following.
In the absence of a new log4j 1.x release, one can remove JMSAppender
from the *log4j-1.2.17.jar* artifact. Commands are listed in the
page <http://slf4j.org/log4shell.html>.
We also recommend that configuration files be protected against write access as stated in <http://slf4j.org/log4shell.html>.
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: dev-unsubscribe@kafka.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [kafka-site] rhauch commented on pull request #388: adding new CVEs to list
Posted by GitBox <gi...@apache.org>.
rhauch commented on pull request #388:
URL: https://github.com/apache/kafka-site/pull/388#issuecomment-994134387
As background for Connect:
* Connect runtime puts all JARs from each connector plugin on a separate classloader, and the Connect runtime nor other connector plugins have access to a plugin's JARs. This is why a connector plugin that includes a Log4J 2.x JAR
* Most connector implementations simply use the logging provided by the Connect runtime, which is Log4J 1.x regardless of the JARs included by connector plugins.
* However, if a connector plugins does include the Log4J 2.x JAR files, those JAR files will only be used if the connector implementation explicitly uses those APIs. There isn't a need to do this, but connectors are custom code and can do quite a bit.
We might consider adding something like this, which I hope conveys the limited scope of the risk:
> The Connect runtime of Apache Kafka allows users to install third party connector plugins. These connector plugins will use Connect runtime's Log4J 1.x by default, even when Log4J 1.x or 2.x JARs are inadvertently shipped with the connector plugin. Check with the vendor of any connector plugin that includes a Log4J 2.x JAR file.
Basically, AK is not responsible for third party connectors that users add to their Connect installations. But users should consult with the vendor of those third party connectors.
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: dev-unsubscribe@kafka.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [kafka-site] scott-confluent commented on pull request #388: adding new CVEs to list
Posted by GitBox <gi...@apache.org>.
scott-confluent commented on pull request #388:
URL: https://github.com/apache/kafka-site/pull/388#issuecomment-993854475
We can't get a preview up, but here's the full page screenshot from my local:

--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: dev-unsubscribe@kafka.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [kafka-site] rhauch commented on pull request #388: adding new CVEs to list
Posted by GitBox <gi...@apache.org>.
rhauch commented on pull request #388:
URL: https://github.com/apache/kafka-site/pull/388#issuecomment-994136975
Or, if we want something even simpler, maybe we could just add a sentence to the `CVE-2021-44228` section that says:
> Check with the vendor of any connector plugin that includes a Log4J 2.x JAR file.
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: dev-unsubscribe@kafka.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [kafka-site] scott-confluent edited a comment on pull request #388: adding new CVEs to list
Posted by GitBox <gi...@apache.org>.
scott-confluent edited a comment on pull request #388:
URL: https://github.com/apache/kafka-site/pull/388#issuecomment-993980560
@junrao I have pushed all updates from the doc as well as your comments here

--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: dev-unsubscribe@kafka.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [kafka-site] scott-confluent commented on pull request #388: adding new CVEs to list
Posted by GitBox <gi...@apache.org>.
scott-confluent commented on pull request #388:
URL: https://github.com/apache/kafka-site/pull/388#issuecomment-994133552

--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: dev-unsubscribe@kafka.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [kafka-site] junrao commented on pull request #388: adding new CVEs to list
Posted by GitBox <gi...@apache.org>.
junrao commented on pull request #388:
URL: https://github.com/apache/kafka-site/pull/388#issuecomment-993920823
@scott-confluent : Have you pushed the new changes?
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: dev-unsubscribe@kafka.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [kafka-site] junrao commented on a change in pull request #388: adding new CVEs to list
Posted by GitBox <gi...@apache.org>.
junrao commented on a change in pull request #388:
URL: https://github.com/apache/kafka-site/pull/388#discussion_r768937548
##########
File path: cve-list.html
##########
@@ -9,6 +9,63 @@ <h1>Apache Kafka Security Vulnerabilities</h1>
This page lists all security vulnerabilities fixed in released versions of Apache Kafka.
+<h2><a href="https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-44228">CVE-2021-44228</a>
+ Flaw in Apache Log4j logging library in versions from 2.0.0 and before 2.15.0</h2>
+
+ <p>Some components in Apache Kafka use <code>Log4j-v1.2.17</code> there is no dependence on <code>Log4j v2.*</code></p>
+
+ <p><a href="https://logging.apache.org/log4j/2.x/manual/lookups.html">Lookups feature</a> was introduced in Log4j v2.x in order to allow specifying Log4j configuration parameters in arbitrary locations (even outside of the configuration files). Log4j v1.x does not offer the same functionality and thus is not vulnerable to <a href="https://access.redhat.com/security/cve/cve-2021-44228">CVE-2021-44228</a>.</p>
+ <p>Users should NOT be impacted by this vulnerability</p>
+
+ <table class="data-table">
+ <tbody>
+ <tr>
+ <td>Versions affected</td>
+ <td>NA</td>
+ </tr>
+ <tr>
+ <td>Fixed versions</td>
+ <td>NA</td>
+ </tr>
+ <tr>
+ <td>Impact</td>
+ <td>NA</td>
+ </tr>
+ <tr>
+ <td>Issue announced</td>
+ <td>09 Dec 2021</td>
+ </tr>
+ </tbody>
+ </table>
+
+<h2><a href="https://access.redhat.com/security/cve/CVE-2021-4104">CVE-2021-4104</a>
+ Flaw in Apache Log4j logging library in versions 1.x</h2>
+
+ <p>Some components in Apache Kafka use <code>Log4j-v1.2.17</code></p>
Review comment:
Could we spell out all components? I think the components include the following.
broker
controller
zookeeper
connect
mirrormaker
tools
clients configured with log4j
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: dev-unsubscribe@kafka.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [kafka-site] izzyacademy commented on pull request #388: adding new CVEs to list
Posted by GitBox <gi...@apache.org>.
izzyacademy commented on pull request #388:
URL: https://github.com/apache/kafka-site/pull/388#issuecomment-993942492
Do we want to add a disclaimer that users need to check their connectors to see if it uses log4j2?
Though the core library does not use this dependency, it is possible external connectors that use it could introduce vulnerabilities if they depend on the affected log4j2 version
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: dev-unsubscribe@kafka.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [kafka-site] scott-confluent edited a comment on pull request #388: adding new CVEs to list
Posted by GitBox <gi...@apache.org>.
scott-confluent edited a comment on pull request #388:
URL: https://github.com/apache/kafka-site/pull/388#issuecomment-993980560
@junrao I have pushed all updates from the doc as well as your comments here:

--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: dev-unsubscribe@kafka.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [kafka-site] scott-confluent removed a comment on pull request #388: adding new CVEs to list
Posted by GitBox <gi...@apache.org>.
scott-confluent removed a comment on pull request #388:
URL: https://github.com/apache/kafka-site/pull/388#issuecomment-993980560
@junrao I have pushed all updates from the doc as well as your comments here:

--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: dev-unsubscribe@kafka.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [kafka-site] rhauch edited a comment on pull request #388: adding new CVEs to list
Posted by GitBox <gi...@apache.org>.
rhauch edited a comment on pull request #388:
URL: https://github.com/apache/kafka-site/pull/388#issuecomment-994134387
As background for Connect:
* Connect runtime puts all JARs from each connector plugin on a separate classloader, and the Connect runtime nor other connector plugins have access to a plugin's JARs. This is why a connector plugin that includes a Log4J 2.x JAR
* Most connector implementations simply use the logging provided by the Connect runtime, which is Log4J 1.x regardless of the JARs included by connector plugins.
* However, if a connector plugins does include the Log4J 2.x JAR files, those JAR files will only be used if the connector implementation explicitly uses those APIs. There isn't a need to do this, but connectors are custom code and can do quite a bit.
We might consider adding something like this under the CVE-2021-44228 section, which I hope conveys the limited scope of the risk:
> The Connect runtime of Apache Kafka allows users to install third party connector plugins. These connector plugins will use Connect runtime's Log4J 1.x by default, even when Log4J 1.x or 2.x JARs are inadvertently shipped with the connector plugin. Check with the vendor of any connector plugin that includes a Log4J 2.x JAR file.
Basically, AK is not responsible for third party connectors that users add to their Connect installations. But users should consult with the vendor of those third party connectors.
As for CVE-2021-4104, I think the existing wording applies to Connect just as well as every other part of AK, so IMO no changes are necessary to that section specifically for Connect.
Feel free to wordsmith as needed.
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: dev-unsubscribe@kafka.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org