You are viewing a plain text version of this content. The canonical link for it is here.
Posted to commits@airflow.apache.org by GitBox <gi...@apache.org> on 2021/04/01 13:04:42 UTC
[GitHub] [airflow] saveriogzz opened a new issue #15136: curl REST authentication fails if variable value hidden from the UI
saveriogzz opened a new issue #15136:
URL: https://github.com/apache/airflow/issues/15136
<!--
Welcome to Apache Airflow! For a smooth issue process, try to answer the following questions.
Don't worry if they're not all applicable; just try to include what you can :-)
If you need to include code snippets or logs, please put them in fenced code
blocks. If they're super-long, please use the details tag like
<details><summary>super-long log</summary> lots of stuff </details>
Please delete these comment blocks before submitting the issue.
-->
<!--
IMPORTANT!!!
PLEASE CHECK "SIMILAR TO X EXISTING ISSUES" OPTION IF VISIBLE
NEXT TO "SUBMIT NEW ISSUE" BUTTON!!!
PLEASE CHECK IF THIS ISSUE HAS BEEN REPORTED PREVIOUSLY USING SEARCH!!!
Please complete the next sections or the issue will be closed.
These questions are the first thing we need to know to understand the context.
-->
**Apache Airflow version**: 2.0.1 - release:2.0.1+beb8af5ac6c438c29e2c186145115fb1334a3735
**Environment**:
- **OS** (e.g. from /etc/os-release): Ubuntu 20.04.2 LTS
**What happened**:
After I have hidden some sensitive variable values from the UI by writing 'secret' into their names, the task supposed to run using this variable value fails for an authentication issue.
The task is a **BashOperator** with which I am doing **curl PUT** requests.
More in details, the bash operator is the following:
```python
put_task = BashOperator(
task_id='put_task',
bash_command=rest_operations.templated_put,
env={
'basepath': basepath,
'filename': filename,
'checksum': "{{ ti.xcom_pull(task_ids='create_metadata', key='checksum') }}",
'user': user,
'password': Variable.get(f"{user}_apikey_secret")
}
)
```
where the templated bash command is:
```bash
curl --header "Content-Type: application/json" --request PUT --data-binary @$basepath/$filename https://cloudnet.fmi.fi/upload/data/$checksum --user $user:$password
```
and the variable is correctly rendered as secret:
```json
{
"basepath": "/path/to/my/binary/data",
"checksum": "mychecksum",
"filename": "myfile",
"password": "********",
"user": "myUser"
}
```
<!-- (please include exact error messages if you can) -->
I get this *Authorization required* message.
```
[2021-04-01 08:51:17,677] {bash.py:158} INFO - Running command: curl --header "Content-Type: application/json" --request PUT --data-binary @$basepath/$filename https://cloudnet.fmi.fi/upload/data/$checksum --user $user:$password
[2021-04-01 08:51:17,849] {bash.py:169} INFO - Output:
[2021-04-01 08:51:18,069] {bash.py:173} INFO - % Total % Received % Xferd Average Speed Time Time Time Current
[2021-04-01 08:51:18,072] {bash.py:173} INFO - Dload Upload Total Spent Left Speed
[2021-04-01 08:51:18,190] {bash.py:173} INFO -
0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0
0 1367k 100 22 0 0 154 0 --:--:-- --:--:-- --:--:-- 154
[2021-04-01 08:51:18,196] {bash.py:173} INFO - Authorization required
```
However, If I remove 'secret' from the variable name, then its value is shown in clear, but everything works as expected.
**What you expected to happen**: I would expect the bash command to be working also with the hidden variable value.
<!-- What do you think went wrong? -->
**How to reproduce it**:
<!---
As minimally and precisely as possible. Keep in mind we do not have access to your cluster or dags.
If you are using kubernetes, please attempt to recreate the issue using minikube or kind.
## Install minikube/kind
- Minikube https://minikube.sigs.k8s.io/docs/start/
- Kind https://kind.sigs.k8s.io/docs/user/quick-start/
If this is a UI bug, please provide a screenshot of the bug or a link to a youtube video of the bug in action
You can include images using the .md style of

To record a screencast, mac users can use QuickTime and then create an unlisted youtube video with the resulting .mov file.
--->
**Anything else we need to know**:
<!--
How often does this problem occur? Once? Every time etc?
Any relevant logs to include? Put them here in side a detail tag:
<details><summary>x.log</summary> lots of stuff </details>
-->
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [airflow] saveriogzz closed issue #15136: curl REST authentication fails if variable value hidden from the UI
Posted by GitBox <gi...@apache.org>.
saveriogzz closed issue #15136:
URL: https://github.com/apache/airflow/issues/15136
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [airflow] saveriogzz commented on issue #15136: curl REST authentication fails if variable value hidden from the UI
Posted by GitBox <gi...@apache.org>.
saveriogzz commented on issue #15136:
URL: https://github.com/apache/airflow/issues/15136#issuecomment-812445161
Hey @wolfier thanks for your help!
You are iright indeed, the password was not "correctly rendered as secret" but simply saved as the actual value "********" after an edit..
I will close this and follow #8421
Thanks a lot again!! ❤️
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [airflow] saveriogzz edited a comment on issue #15136: curl REST authentication fails if variable value hidden from the UI
Posted by GitBox <gi...@apache.org>.
saveriogzz edited a comment on issue #15136:
URL: https://github.com/apache/airflow/issues/15136#issuecomment-812445161
Hey @wolfier thanks for your help!
You are right indeed, the password was not "correctly rendered as secret" but simply saved as the actual value "********" after an edit..
I will close this and follow #8421
Thanks a lot again!! ❤️
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [airflow] boring-cyborg[bot] commented on issue #15136: curl REST authentication fails if variable value hidden from the UI
Posted by GitBox <gi...@apache.org>.
boring-cyborg[bot] commented on issue #15136:
URL: https://github.com/apache/airflow/issues/15136#issuecomment-811893241
Thanks for opening your first issue here! Be sure to follow the issue template!
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [airflow] wolfier commented on issue #15136: curl REST authentication fails if variable value hidden from the UI
Posted by GitBox <gi...@apache.org>.
wolfier commented on issue #15136:
URL: https://github.com/apache/airflow/issues/15136#issuecomment-812218246
Based on #8421, the render template view is not be capable of hiding sensitive information.
Quoting @kaxil,
> Yes the Rendered UI Field currently exposes everything. We should have a way of hiding this.
I was unable to replicate what you had by following your instructions. The hidden sensitive value when the name of the Variable contains special keywords still renders as its original value.
I think you may have saved the Airflow Variable while the value was shown as the replaced value in the Airflow Variables view thereby saving the the actual value as "********". That was the only way I am able to replicate what you had.
1. Create Airflow Variable in UI, my_value_secret.
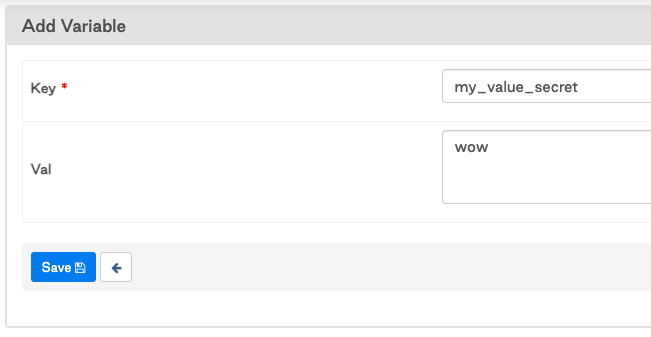
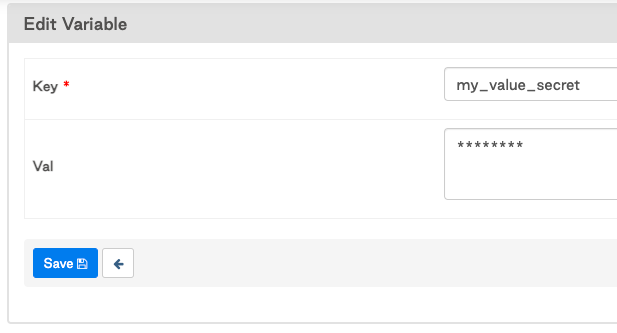
2. Save my_value_secret with no changes made.
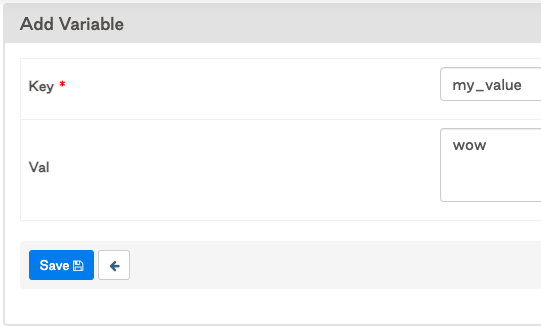
3. Create Airflow Variable in UI, my_value
4. my_value_secret Variable is rendered as "********" while my_value Variable is rendered as "wow"
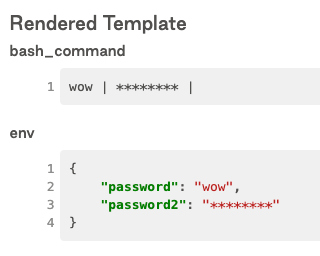
```python
from airflow.models import DAG
from datetime import datetime
from airflow.models import Variable
from airflow.operators.bash import BashOperator
dag = DAG(
dag_id="trigger_dag",
start_date=datetime(2021, 3, 10),
catchup=False,
schedule_interval='@once',
)
with dag:
put_task = BashOperator(
task_id='put_task',
bash_command=
'{{ var.value.my_value }} | '
'{{ var.value.my_value_secret }} | '
,
env={
'password': Variable.get(f"my_value"),
'password2': Variable.get(f"my_value_secret"),
}
)
```
Can you verify that your scenario is reproducible on your end? Also if you are able to reproduce the issue, can you print out the secret value in a PythonOperator to see its true value?
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org