You are viewing a plain text version of this content. The canonical link for it is here.
Posted to commits@druid.apache.org by GitBox <gi...@apache.org> on 2021/01/20 13:55:44 UTC
[GitHub] [druid] trinitry opened a new issue #10783: pac4j using OAuth authentication
trinitry opened a new issue #10783:
URL: https://github.com/apache/druid/issues/10783
Dear ALL,
Enabling the pac4j module and using the following settings in runtime.properties of the router
druid.auth.authenticatorChain=["pac4j"]
druid.auth.authenticator.pac4j.type=pac4j
druid.auth.pac4j.cookiePassphrase=XXXX
druid.auth.pac4j.oidc.clientID=XXXXXX
druid.auth.pac4j.oidc.clientSecret=XXXXXXXXXXX
druid.auth.pac4j.oidc.discoveryURI=https://xxxxxx.biz/auth/realms/eu0/protocol/openid-connect/token
generated the following exception
HTTP ERROR 500 org.pac4j.core.exception.TechnicalException: java.io.IOException: Server returned HTTP response code: 405 for URL - the discoveryURI
I had test the Kafka broker, which i am trying to connect to with a short python script and i was able to get data, so credentials and URI are correct and validated.
### Affected Version
The Druid version where the problem was encountered is 0.20
### Description
I am testing locally with the start-micro-quickstart script.
the logs from the router follows:
> 2021-01-20T13:13:58,106 INFO [main] org.apache.druid.java.util.common.lifecycle.Lifecycle - Successfully started lifecycle [module]
> 2021-01-20T13:13:58,661 INFO [NodeRoleWatcher[COORDINATOR]] org.apache.druid.curator.discovery.CuratorDruidNodeDiscoveryProvider$NodeRoleWatcher - Node[http://localhost:8081] of role[coordinator] detected.
> 2021-01-20T13:13:58,778 INFO [NodeRoleWatcher[BROKER]] org.apache.druid.curator.discovery.CuratorDruidNodeDiscoveryProvider$NodeRoleWatcher - Node[http://localhost:8082] of role[broker] detected.
> 2021-01-20T13:14:06,605 WARN [qtp1398479590-80] org.eclipse.jetty.server.HttpChannel - handleException /unified-console.html java.io.IOException: Server returned HTTP response code: 405 for URL: https://xxxxxx.biz/auth/realms/eu0/protocol/openid-connect/token
> 2021-01-20T13:14:23,734 WARN [qtp1398479590-72] org.eclipse.jetty.server.HttpChannel - handleException /druid/v2/sql java.io.IOException: Server returned HTTP response code: 405 for URL: https://xxxxxx.biz/auth/realms/eu0/protocol/openid-connect/token
> 2021-01-20T13:14:23,956 WARN [qtp1398479590-73] org.eclipse.jetty.server.HttpChannel - handleException /druid/v2/sql java.io.IOException: Server returned HTTP response code: 405 for URL: https://xxxxxx.biz/auth/realms/eu0/protocol/openid-connect/token
Is this a configuration issue or OAuthentication is not supported by the pac4j module ?
Any help is more than welcome!!!!
Thank you all!
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
---------------------------------------------------------------------
To unsubscribe, e-mail: commits-unsubscribe@druid.apache.org
For additional commands, e-mail: commits-help@druid.apache.org
[GitHub] [druid] himanshug commented on issue #10783: pac4j using OAuth authentication
Posted by GitBox <gi...@apache.org>.
himanshug commented on issue #10783:
URL: https://github.com/apache/druid/issues/10783#issuecomment-764073397
For okta, discoveryURI looks something like what is described in [okta-well-known-openid-configuration](https://developer.okta.com/docs/reference/api/oidc/#well-known-openid-configuration)
what does
`curl -vv https://xxxxxx.biz/auth/realms/eu0/protocol/openid-connect/token` give you?
`HTTP 405` seems to suggest that endpoint does not support `HTTP GET`
which authentication server are you using?
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
---------------------------------------------------------------------
To unsubscribe, e-mail: commits-unsubscribe@druid.apache.org
For additional commands, e-mail: commits-help@druid.apache.org
[GitHub] [druid] trinitry commented on issue #10783: pac4j using OAuth authentication
Posted by GitBox <gi...@apache.org>.
trinitry commented on issue #10783:
URL: https://github.com/apache/druid/issues/10783#issuecomment-766946077
I am sorry if i was not clear on what i am trying to achieve,
i am trying to establish a connection
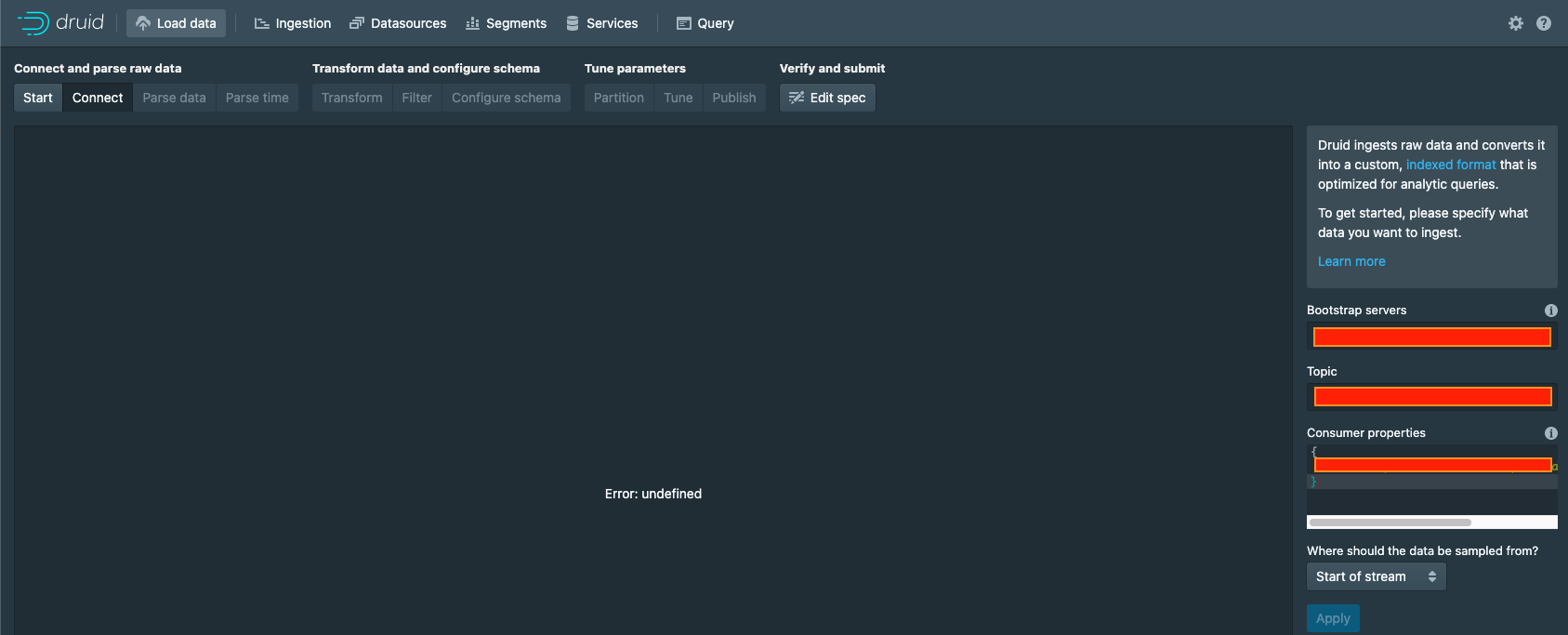
to a kafka broker using the apache kafka indexing service.
The broker i am trying to connect is been set up with OAuth.
I thought that i could use the pac4j extension to achieve the authorization with the broker-_probably not the way to do it!!_
How i could achieve the above ?
By configuring the bootstrap .servers and the topic parameter i end up with an
> Error: udefined
at the web console.
Possible due to lack of authorization.
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
---------------------------------------------------------------------
To unsubscribe, e-mail: commits-unsubscribe@druid.apache.org
For additional commands, e-mail: commits-help@druid.apache.org
[GitHub] [druid] trinitry commented on issue #10783: pac4j using OAuth authentication
Posted by GitBox <gi...@apache.org>.
trinitry commented on issue #10783:
URL: https://github.com/apache/druid/issues/10783#issuecomment-766682950
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
---------------------------------------------------------------------
To unsubscribe, e-mail: commits-unsubscribe@druid.apache.org
For additional commands, e-mail: commits-help@druid.apache.org
[GitHub] [druid] trinitry commented on issue #10783: pac4j using OAuth authentication
Posted by GitBox <gi...@apache.org>.
trinitry commented on issue #10783:
URL: https://github.com/apache/druid/issues/10783#issuecomment-767361636
Thank you for the effort,
i will look more into the kafka docs for this, i will close this issue as is not relevant to the pack4j
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
---------------------------------------------------------------------
To unsubscribe, e-mail: commits-unsubscribe@druid.apache.org
For additional commands, e-mail: commits-help@druid.apache.org
[GitHub] [druid] trinitry commented on issue #10783: pac4j using OAuth authentication
Posted by GitBox <gi...@apache.org>.
trinitry commented on issue #10783:
URL: https://github.com/apache/druid/issues/10783#issuecomment-765219676
the output from
`curl -vv https://xxxxxx.biz/auth/realms/eu0/protocol/openid-connect/token`
`> GET /auth/realms/eu0/protocol/openid-connect/token HTTP/1.1
> Host: sso.XXXX.biz
> User-Agent: curl/7.64.1
> Accept: */*
>
< HTTP/1.1 405 Method Not Allowed
< Server: nginx/1.19.5
< Date: Thu, 21 Jan 2021 12:55:13 GMT
< Content-Type: application/json
< Content-Length: 90
< Connection: keep-alive
<
* Connection #0 to host sso.XXXX.biz left intact
{"error":"RESTEASY003650: No resource method found for GET, return 405 with Allow header"}* Closing connection 0`
As i see from the above is (i believe) exactly what you suggest to be the issue!!
Then i try with a different
`druid.auth.pac4j.oidc.discoveryURI` which i also tested
`curl -vv https://sso.XXXX.biz/auth/realms/eu0/.well-known/openid-configuration`
and i got
GET /auth/realms/eu0/.well-known/openid-configuration HTTP/1.1
> Host: sso.XXXXX.biz
> User-Agent: curl/7.64.1
> Accept: */*
>
< HTTP/1.1 200 OK
< Server: nginx/1.19.5
< Date: Thu, 21 Jan 2021 12:52:48 GMT
< Content-Type: application/json
< Content-Length: 2644
< Connection: keep-alive
< Cache-Control: no-cache, must-revalidate, no-transform, no-store
<
* Connection #0 to host sso.XXXX.biz left intact
{"issuer":"https://sso .....* Closing connection 0
It seems with this discoveryURI i went a bit further... but now i get through Druid web console
> Invalid parameter: redirect_uri
For the authentication server, if i am not mistaken (as i am not the one who set the broker up but i try to connect to it), i understand that is using the
> keycloak
Thank you for your comments and support on this!!
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
---------------------------------------------------------------------
To unsubscribe, e-mail: commits-unsubscribe@druid.apache.org
For additional commands, e-mail: commits-help@druid.apache.org
[GitHub] [druid] himanshug commented on issue #10783: pac4j using OAuth authentication
Posted by GitBox <gi...@apache.org>.
himanshug commented on issue #10783:
URL: https://github.com/apache/druid/issues/10783#issuecomment-764073397
For okta, discoveryURI looks something like what is described in [okta-well-known-openid-configuration](https://developer.okta.com/docs/reference/api/oidc/#well-known-openid-configuration)
what does
`curl -vv https://xxxxxx.biz/auth/realms/eu0/protocol/openid-connect/token` give you?
`HTTP 405` seems to suggest that endpoint does not support `HTTP GET`
which authentication server are you using?
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
---------------------------------------------------------------------
To unsubscribe, e-mail: commits-unsubscribe@druid.apache.org
For additional commands, e-mail: commits-help@druid.apache.org
[GitHub] [druid] himanshug commented on issue #10783: pac4j using OAuth authentication
Posted by GitBox <gi...@apache.org>.
himanshug commented on issue #10783:
URL: https://github.com/apache/druid/issues/10783#issuecomment-766904716
Can you please describe what you are trying to achieve? pac4j extensions is only for supporting Oauth on router web console in which case you are supposed to see the auth server's login page, I couldn't understand the context around its relation to kafka indexing service usage.
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
---------------------------------------------------------------------
To unsubscribe, e-mail: commits-unsubscribe@druid.apache.org
For additional commands, e-mail: commits-help@druid.apache.org
[GitHub] [druid] trinitry closed issue #10783: pac4j using OAuth authentication
Posted by GitBox <gi...@apache.org>.
trinitry closed issue #10783:
URL: https://github.com/apache/druid/issues/10783
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
---------------------------------------------------------------------
To unsubscribe, e-mail: commits-unsubscribe@druid.apache.org
For additional commands, e-mail: commits-help@druid.apache.org
[GitHub] [druid] himanshug commented on issue #10783: pac4j using OAuth authentication
Posted by GitBox <gi...@apache.org>.
himanshug commented on issue #10783:
URL: https://github.com/apache/druid/issues/10783#issuecomment-766953421
I see, now it makes more sense.
Well, druid-pac4j extension is not for that.
I think you need to figure out what are right `consumerProperties` to set so that kafka client can authenticate with kafka broker. You would likely find more help inside kafka docs on this and/or hopefully from the people who have setup kafka broker side auth, they should be able to tell you what you need to put in client consumerProperties. hth.
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
---------------------------------------------------------------------
To unsubscribe, e-mail: commits-unsubscribe@druid.apache.org
For additional commands, e-mail: commits-help@druid.apache.org
[GitHub] [druid] himanshug commented on issue #10783: pac4j using OAuth authentication
Posted by GitBox <gi...@apache.org>.
himanshug commented on issue #10783:
URL: https://github.com/apache/druid/issues/10783#issuecomment-766904716
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
---------------------------------------------------------------------
To unsubscribe, e-mail: commits-unsubscribe@druid.apache.org
For additional commands, e-mail: commits-help@druid.apache.org
[GitHub] [druid] trinitry commented on issue #10783: pac4j using OAuth authentication
Posted by GitBox <gi...@apache.org>.
trinitry commented on issue #10783:
URL: https://github.com/apache/druid/issues/10783#issuecomment-766682950
Looking more into it and with a feedback from my colleague,
i should never end up in the web page of the auth service, i should use the
`https://sso.XXXX.biz/auth/realms/eu0/protocol/openid-connect/token`
which the
> curl -vvv
command returns the
> Connection #0 to host sso.XXXX.biz left intact
{"error":"RESTEASY003650: No resource method found for GET, return 405 with Allow header"}* Closing connection 0`
They provide me with the following steps
> The endpoint uses the typical OAuth conventions:
>
> You must make a POST
> You must use basic auth with cliend id as username and client secret as password
> Body must be x-www-form-endoded with a single param called "grant_type" with value "client_credentials"
> so, for curl becomes:
>
> curl --location --request POST 'https://sso.XXXX.biz/auth/realms/eu0/protocol/openid-connect/token' \
> --header 'Authorization: Basic Base64encoding-ID:password' \
> --header 'Content-Type: application/x-www-form-urlencoded' \
> --data-urlencode 'grant_type=client_credentials'
>
By executing the above command i got a reply with the access token.
So, could we use the pack4j extension to authorise druid and use the kafka indexing service with the aforementioned kafka broker?
----------------------------------------------------------------
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
---------------------------------------------------------------------
To unsubscribe, e-mail: commits-unsubscribe@druid.apache.org
For additional commands, e-mail: commits-help@druid.apache.org