You are viewing a plain text version of this content. The canonical link for it is here.
Posted to commits@airflow.apache.org by GitBox <gi...@apache.org> on 2021/04/01 22:50:57 UTC
[GitHub] [airflow] wolfier commented on issue #15136: curl REST authentication fails if variable value hidden from the UI
wolfier commented on issue #15136:
URL: https://github.com/apache/airflow/issues/15136#issuecomment-812218246
Based on #8421, the render template view is not be capable of hiding sensitive information.
Quoting @kaxil,
> Yes the Rendered UI Field currently exposes everything. We should have a way of hiding this.
I was unable to replicate what you had by following your instructions. The hidden sensitive value when the name of the Variable contains special keywords still renders as its original value.
I think you may have saved the Airflow Variable while the value was shown as the replaced value in the Airflow Variables view thereby saving the the actual value as "********". That was the only way I am able to replicate what you had.
1. Create Airflow Variable in UI, my_value_secret.
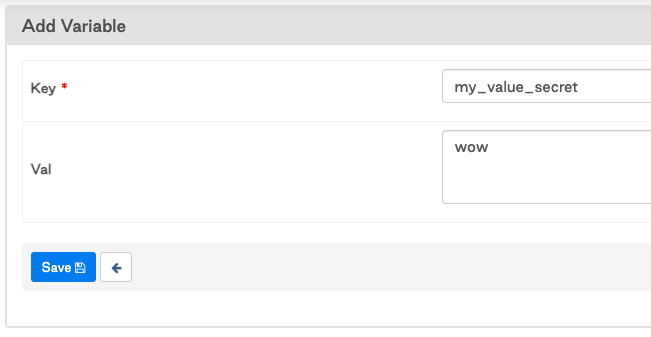
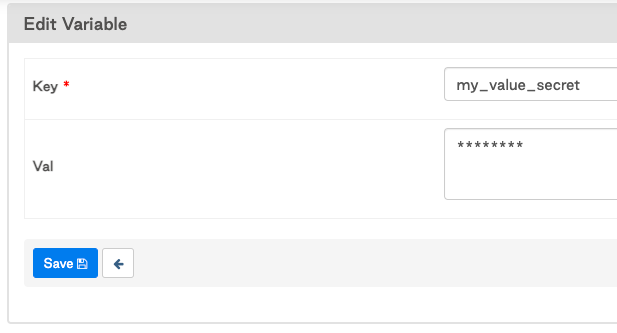
2. Save my_value_secret with no changes made.
3. Create Airflow Variable in UI, my_value
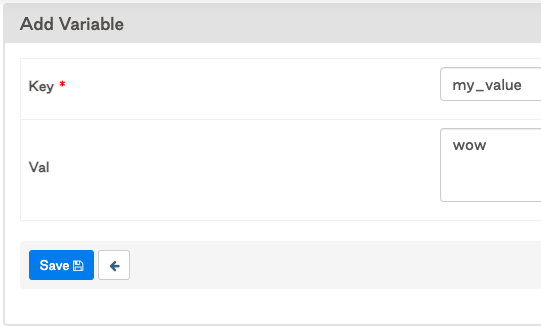
4. my_value_secret Variable is rendered as "********" while my_value Variable is rendered as "wow"
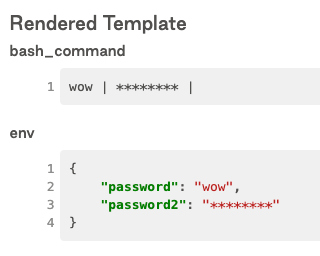
```python
from airflow.models import DAG
from datetime import datetime
from airflow.models import Variable
from airflow.operators.bash import BashOperator
dag = DAG(
dag_id="trigger_dag",
start_date=datetime(2021, 3, 10),
catchup=False,
schedule_interval='@once',
)
with dag:
put_task = BashOperator(
task_id='put_task',
bash_command=
'{{ var.value.my_value }} | '
'{{ var.value.my_value_secret }} | '
,
env={
'password': Variable.get(f"my_value"),
'password2': Variable.get(f"my_value_secret"),
}
)
```
Can you verify that your scenario is reproducible on your end? Also if you are able to reproduce the issue, can you print out the secret value in a PythonOperator to see its true value?
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
For queries about this service, please contact Infrastructure at:
users@infra.apache.org