You are viewing a plain text version of this content. The canonical link for it is here.
Posted to commits@pulsar.apache.org by GitBox <gi...@apache.org> on 2022/03/11 08:02:11 UTC
[GitHub] [pulsar] momo-jun opened a new pull request #14659: [Doc] add doc for Oauth2 authentication support in node.js client and update doc for custom AuthN/AuthZ
momo-jun opened a new pull request #14659:
URL: https://github.com/apache/pulsar/pull/14659
### Modifications
1. To align with the latest release of node.js client 1.6.2 and fix #14143, add doc for Oauth2 authentication support in node.js client.
2. To align with #14044 for 2.11, update doc for extended AuthN/AuthZ by replacing outdated info and code samples with github URLs, adding more auth providers with links to examples.
The preview looks good.

### Documentation
- [ ] `doc`
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: commits-unsubscribe@pulsar.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [pulsar] Anonymitaet merged pull request #14659: [Doc] [Do-not-merge] add doc for Oauth2 authentication support in node.js client and update doc for custom AuthN/AuthZ
Posted by GitBox <gi...@apache.org>.
Anonymitaet merged pull request #14659:
URL: https://github.com/apache/pulsar/pull/14659
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: commits-unsubscribe@pulsar.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [pulsar] Anonymitaet merged pull request #14659: [Doc] [Do-not-merge] add doc for Oauth2 authentication support in node.js client and update doc for custom AuthN/AuthZ
Posted by GitBox <gi...@apache.org>.
Anonymitaet merged pull request #14659:
URL: https://github.com/apache/pulsar/pull/14659
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: commits-unsubscribe@pulsar.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [pulsar] github-actions[bot] commented on pull request #14659: [Doc] add doc for Oauth2 authentication support in node.js client and update doc for custom AuthN/AuthZ
Posted by GitBox <gi...@apache.org>.
github-actions[bot] commented on pull request #14659:
URL: https://github.com/apache/pulsar/pull/14659#issuecomment-1064868247
@momo-jun:Thanks for your contribution. For this PR, do we need to update docs?
(The [PR template contains info about doc](https://github.com/apache/pulsar/blob/master/.github/PULL_REQUEST_TEMPLATE.md#documentation), which helps others know more about the changes. Can you provide doc-related info in this and future PR descriptions? Thanks)
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: commits-unsubscribe@pulsar.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [pulsar] momo-jun commented on pull request #14659: [Doc] [Do-not-merge] add doc for Oauth2 authentication support in node.js client and update doc for custom AuthN/AuthZ
Posted by GitBox <gi...@apache.org>.
momo-jun commented on pull request #14659:
URL: https://github.com/apache/pulsar/pull/14659#issuecomment-1070130806
Thanks @Anonymitaet and @tuteng for your comments. I've fixed them. PTAL.
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: commits-unsubscribe@pulsar.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [pulsar] github-actions[bot] commented on pull request #14659: [Doc] add doc for Oauth2 authentication support in node.js client and update doc for custom AuthN/AuthZ
Posted by GitBox <gi...@apache.org>.
github-actions[bot] commented on pull request #14659:
URL: https://github.com/apache/pulsar/pull/14659#issuecomment-1064873171
@momo-jun:Thanks for providing doc info!
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: commits-unsubscribe@pulsar.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [pulsar] momo-jun commented on pull request #14659: [Doc] add doc for Oauth2 authentication support in node.js client and update doc for custom AuthN/AuthZ
Posted by GitBox <gi...@apache.org>.
momo-jun commented on pull request #14659:
URL: https://github.com/apache/pulsar/pull/14659#issuecomment-1064986891
Hi @tuteng @Anonymitaet can you please review this doc PR? Thank you.
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: commits-unsubscribe@pulsar.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org
[GitHub] [pulsar] Anonymitaet commented on a change in pull request #14659: [Doc] add doc for Oauth2 authentication support in node.js client and update doc for custom AuthN/AuthZ
Posted by GitBox <gi...@apache.org>.
Anonymitaet commented on a change in pull request #14659:
URL: https://github.com/apache/pulsar/pull/14659#discussion_r825648899
##########
File path: site2/docs/security-extending.md
##########
@@ -23,173 +23,54 @@ PulsarClient client = PulsarClient.builder()
.build();
```
-You can use 2 interfaces to implement on the client side:
- * `Authentication` -> http://pulsar.apache.org/api/client/org/apache/pulsar/client/api/Authentication.html
- * `AuthenticationDataProvider` -> http://pulsar.apache.org/api/client/org/apache/pulsar/client/api/AuthenticationDataProvider.html
-
-
-This in turn needs to provide the client credentials in the form of `org.apache.pulsar.client.api.AuthenticationDataProvider`. This leaves the chance to return different kinds of authentication token for different types of connection or by passing a certificate chain to use for TLS.
+You can implement 2 interfaces on the client side:
+ * [`Authentication`](http://pulsar.apache.org/api/client/org/apache/pulsar/client/api/Authentication.html)
+ * [`AuthenticationDataProvider`](http://pulsar.apache.org/api/client/org/apache/pulsar/client/api/AuthenticationDataProvider.html)
+This in turn requires you to provide the client credentials in the form of `org.apache.pulsar.client.api.AuthenticationDataProvider` and also leaves the chance to return different kinds of authentication token for different types of connection or by passing a certificate chain to use for TLS.
-You can find examples for client authentication providers at:
-
- * Mutual TLS Auth -- https://github.com/apache/pulsar/tree/master/pulsar-client/src/main/java/org/apache/pulsar/client/impl/auth
- * Athenz -- https://github.com/apache/pulsar/tree/master/pulsar-client-auth-athenz/src/main/java/org/apache/pulsar/client/impl/auth
+You can find the following examples for different client authentication plugins:
+ * [Mutual TLS](https://github.com/apache/pulsar/blob/master/pulsar-client/src/main/java/org/apache/pulsar/client/impl/auth/AuthenticationTls.java)
+ * [Athenz](https://github.com/apache/pulsar/blob/master/pulsar-client-auth-athenz/src/main/java/org/apache/pulsar/client/impl/auth/AuthenticationAthenz.java)
+ * [Kerberos](https://github.com/apache/pulsar/blob/master/pulsar-client-auth-sasl/src/main/java/org/apache/pulsar/client/impl/auth/AuthenticationSasl.java)
+ * [JSON Web Token (JWT)](https://github.com/apache/pulsar/blob/master/pulsar-client/src/main/java/org/apache/pulsar/client/impl/auth/AuthenticationToken.java)
+ * [OAuth 2.0](https://github.com/apache/pulsar/blob/master/pulsar-client/src/main/java/org/apache/pulsar/client/impl/auth/oauth2/AuthenticationOAuth2.java)
+ * [Basic auth](https://github.com/apache/pulsar/blob/master/pulsar-client/src/main/java/org/apache/pulsar/client/impl/auth/AuthenticationBasic.java)
### Proxy/Broker authentication plugin
On the proxy/broker side, you need to configure the corresponding plugin to validate the credentials that the client sends. The Proxy and Broker can support multiple authentication providers at the same time.
-In `conf/broker.conf` you can choose to specify a list of valid providers:
+In `conf/broker.conf`, you can choose to specify a list of valid providers:
```properties
# Authentication provider name list, which is comma separated list of class names
authenticationProviders=
```
-To implement `org.apache.pulsar.broker.authentication.AuthenticationProvider` on one single interface:
-```java
-/**
- * Provider of authentication mechanism
- */
-public interface AuthenticationProvider extends Closeable {
-
- /**
- * Perform initialization for the authentication provider
- *
- * @param config
- * broker config object
- * @throws IOException
- * if the initialization fails
- */
- void initialize(ServiceConfiguration config) throws IOException;
-
- /**
- * @return the authentication method name supported by this provider
- */
- String getAuthMethodName();
-
- /**
- * Validate the authentication for the given credentials with the specified authentication data
- *
- * @param authData
- * provider specific authentication data
- * @return the "role" string for the authenticated connection, if the authentication was successful
- * @throws AuthenticationException
- * if the credentials are not valid
- */
- String authenticate(AuthenticationDataSource authData) throws AuthenticationException;
-
-}
-```
+For the implementation of the `org.apache.pulsar.broker.authentication.AuthenticationProvider` interface, refer to [here](https://github.com/apache/pulsar/blob/master/pulsar-broker-common/src/main/java/org/apache/pulsar/broker/authentication/AuthenticationProvider.java).
-The following is the example for Broker authentication plugins:
+You can find the following examples for different Broker authentication plugins:
Review comment:
```suggestion
You can find the following examples for different broker authentication plugins:
```
##########
File path: site2/docs/security-oauth2.md
##########
@@ -153,6 +153,47 @@ params = '''
client = Client("pulsar://my-cluster:6650", authentication=AuthenticationOauth2(params))
```
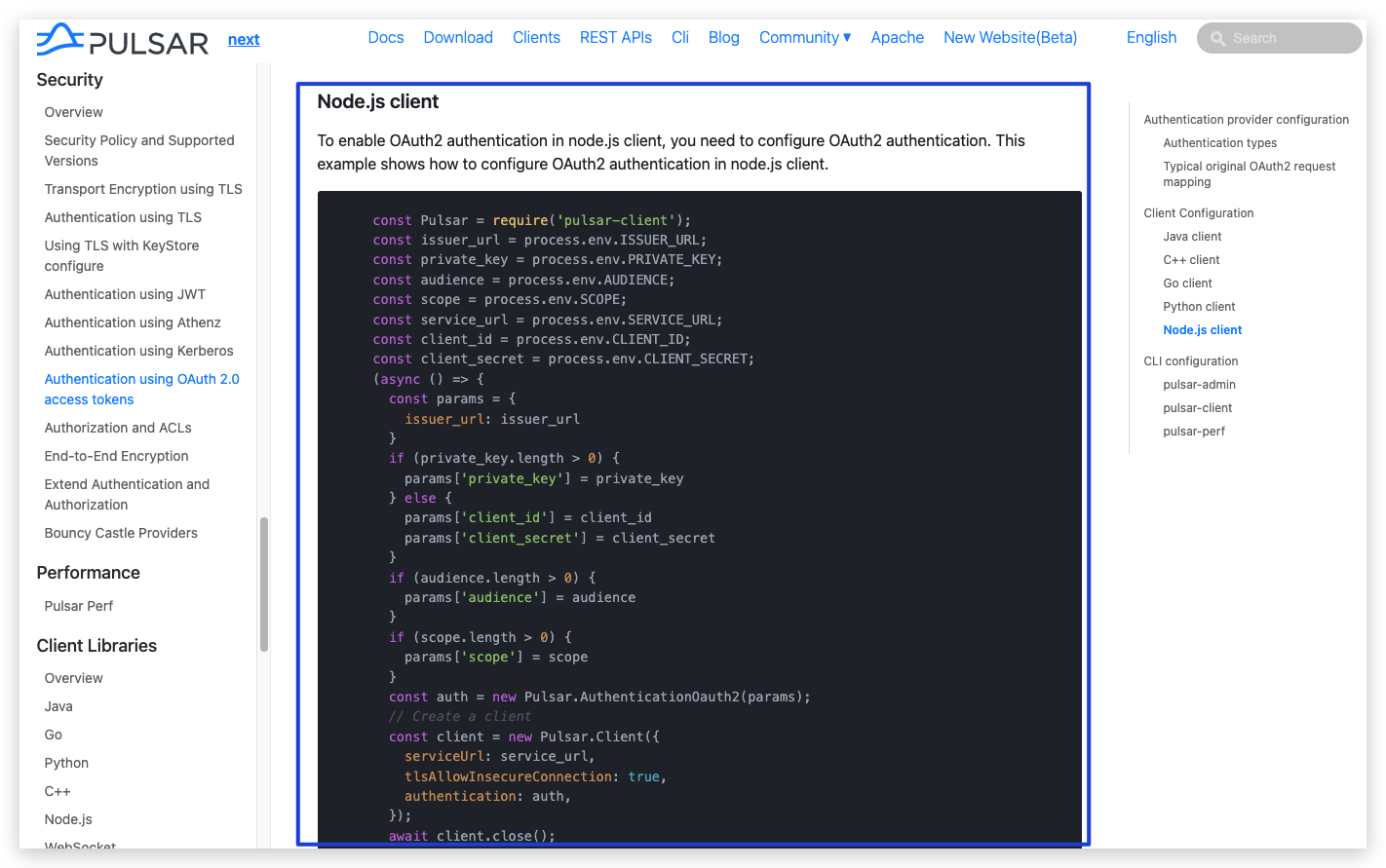
+### Node.js client
+
+To enable OAuth2 authentication in node.js client, you need to configure OAuth2 authentication.
Review comment:
```suggestion
To enable OAuth2 authentication in Node.js client, you need to configure OAuth2 authentication.
```
proper noun
##########
File path: site2/docs/security-extending.md
##########
@@ -23,173 +23,54 @@ PulsarClient client = PulsarClient.builder()
.build();
```
-You can use 2 interfaces to implement on the client side:
- * `Authentication` -> http://pulsar.apache.org/api/client/org/apache/pulsar/client/api/Authentication.html
- * `AuthenticationDataProvider` -> http://pulsar.apache.org/api/client/org/apache/pulsar/client/api/AuthenticationDataProvider.html
-
-
-This in turn needs to provide the client credentials in the form of `org.apache.pulsar.client.api.AuthenticationDataProvider`. This leaves the chance to return different kinds of authentication token for different types of connection or by passing a certificate chain to use for TLS.
+You can implement 2 interfaces on the client side:
+ * [`Authentication`](http://pulsar.apache.org/api/client/org/apache/pulsar/client/api/Authentication.html)
+ * [`AuthenticationDataProvider`](http://pulsar.apache.org/api/client/org/apache/pulsar/client/api/AuthenticationDataProvider.html)
+This in turn requires you to provide the client credentials in the form of `org.apache.pulsar.client.api.AuthenticationDataProvider` and also leaves the chance to return different kinds of authentication token for different types of connection or by passing a certificate chain to use for TLS.
-You can find examples for client authentication providers at:
-
- * Mutual TLS Auth -- https://github.com/apache/pulsar/tree/master/pulsar-client/src/main/java/org/apache/pulsar/client/impl/auth
- * Athenz -- https://github.com/apache/pulsar/tree/master/pulsar-client-auth-athenz/src/main/java/org/apache/pulsar/client/impl/auth
+You can find the following examples for different client authentication plugins:
+ * [Mutual TLS](https://github.com/apache/pulsar/blob/master/pulsar-client/src/main/java/org/apache/pulsar/client/impl/auth/AuthenticationTls.java)
+ * [Athenz](https://github.com/apache/pulsar/blob/master/pulsar-client-auth-athenz/src/main/java/org/apache/pulsar/client/impl/auth/AuthenticationAthenz.java)
+ * [Kerberos](https://github.com/apache/pulsar/blob/master/pulsar-client-auth-sasl/src/main/java/org/apache/pulsar/client/impl/auth/AuthenticationSasl.java)
+ * [JSON Web Token (JWT)](https://github.com/apache/pulsar/blob/master/pulsar-client/src/main/java/org/apache/pulsar/client/impl/auth/AuthenticationToken.java)
+ * [OAuth 2.0](https://github.com/apache/pulsar/blob/master/pulsar-client/src/main/java/org/apache/pulsar/client/impl/auth/oauth2/AuthenticationOAuth2.java)
+ * [Basic auth](https://github.com/apache/pulsar/blob/master/pulsar-client/src/main/java/org/apache/pulsar/client/impl/auth/AuthenticationBasic.java)
### Proxy/Broker authentication plugin
On the proxy/broker side, you need to configure the corresponding plugin to validate the credentials that the client sends. The Proxy and Broker can support multiple authentication providers at the same time.
-In `conf/broker.conf` you can choose to specify a list of valid providers:
+In `conf/broker.conf`, you can choose to specify a list of valid providers:
```properties
# Authentication provider name list, which is comma separated list of class names
authenticationProviders=
```
-To implement `org.apache.pulsar.broker.authentication.AuthenticationProvider` on one single interface:
-```java
-/**
- * Provider of authentication mechanism
- */
-public interface AuthenticationProvider extends Closeable {
-
- /**
- * Perform initialization for the authentication provider
- *
- * @param config
- * broker config object
- * @throws IOException
- * if the initialization fails
- */
- void initialize(ServiceConfiguration config) throws IOException;
-
- /**
- * @return the authentication method name supported by this provider
- */
- String getAuthMethodName();
-
- /**
- * Validate the authentication for the given credentials with the specified authentication data
- *
- * @param authData
- * provider specific authentication data
- * @return the "role" string for the authenticated connection, if the authentication was successful
- * @throws AuthenticationException
- * if the credentials are not valid
- */
- String authenticate(AuthenticationDataSource authData) throws AuthenticationException;
-
-}
-```
+For the implementation of the `org.apache.pulsar.broker.authentication.AuthenticationProvider` interface, refer to [here](https://github.com/apache/pulsar/blob/master/pulsar-broker-common/src/main/java/org/apache/pulsar/broker/authentication/AuthenticationProvider.java).
-The following is the example for Broker authentication plugins:
+You can find the following examples for different Broker authentication plugins:
- * Mutual TLS -- https://github.com/apache/pulsar/blob/master/pulsar-broker-common/src/main/java/org/apache/pulsar/broker/authentication/AuthenticationProviderTls.java
- * Athenz -- https://github.com/apache/pulsar/blob/master/pulsar-broker-auth-athenz/src/main/java/org/apache/pulsar/broker/authentication/AuthenticationProviderAthenz.java
+ * [Mutual TLS](https://github.com/apache/pulsar/blob/master/pulsar-broker-common/src/main/java/org/apache/pulsar/broker/authentication/AuthenticationProviderTls.java)
+ * [Athenz](https://github.com/apache/pulsar/blob/master/pulsar-broker-auth-athenz/src/main/java/org/apache/pulsar/broker/authentication/AuthenticationProviderAthenz.java)
+ * [Kerberos](https://github.com/apache/pulsar/blob/master/pulsar-broker-auth-sasl/src/main/java/org/apache/pulsar/broker/authentication/AuthenticationProviderSasl.java)
+ * [JSON Web Token (JWT)](https://github.com/apache/pulsar/blob/master/pulsar-broker-common/src/main/java/org/apache/pulsar/broker/authentication/AuthenticationProviderToken.java)
+ * [Basic auth](https://github.com/apache/pulsar/blob/master/pulsar-broker-common/src/main/java/org/apache/pulsar/broker/authentication/AuthenticationProviderToken.java)
## Authorization
Authorization is the operation that checks whether a particular "role" or "principal" has permission to perform a certain operation.
-By default, you can use the embedded authorization provider provided by Pulsar. You can also configure a different authorization provider through a plugin.
-Note that although the Authentication plugin is designed for use in both the Proxy and Broker,
-the Authorization plugin is designed only for use on the Broker however the Proxy does perform some simple Authorization checks of Roles if authorization is enabled.
+By default, you can use the embedded authorization provider provided by Pulsar. You can also configure a different authorization provider through a plugin. Note that although the Authentication plugin is designed for use in both the Proxy and Broker, the Authorization plugin is designed only for use on the Broker.
Review comment:
```suggestion
By default, you can use the embedded authorization provider provided by Pulsar. You can also configure a different authorization provider through a plugin. Note that although the Authentication plugin is designed for use in both the Proxy and Broker, the Authorization plugin is designed only for use on the Broker.
```
why capitalize Broker? it is not a proper noun. (we can update the original text if it is not accurate)
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: commits-unsubscribe@pulsar.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org