You are viewing a plain text version of this content. The canonical link for it is here.
Posted to notifications@apisix.apache.org by GitBox <gi...@apache.org> on 2022/05/12 01:38:09 UTC
[GitHub] [apisix] juzhiyuan commented on a diff in pull request #7030: docs: update "Traffic" Plugin docs 1
juzhiyuan commented on code in PR #7030:
URL: https://github.com/apache/apisix/pull/7030#discussion_r870873912
##########
docs/en/latest/plugins/limit-conn.md:
##########
@@ -93,17 +99,19 @@ curl http://127.0.0.1:9080/apisix/admin/routes/1 -H 'X-API-KEY: edd1c9f034335f13
}'
```
-You also can complete the above operation through the web interface, first add a route, then add limit-conn plugin:
-
+<!-- 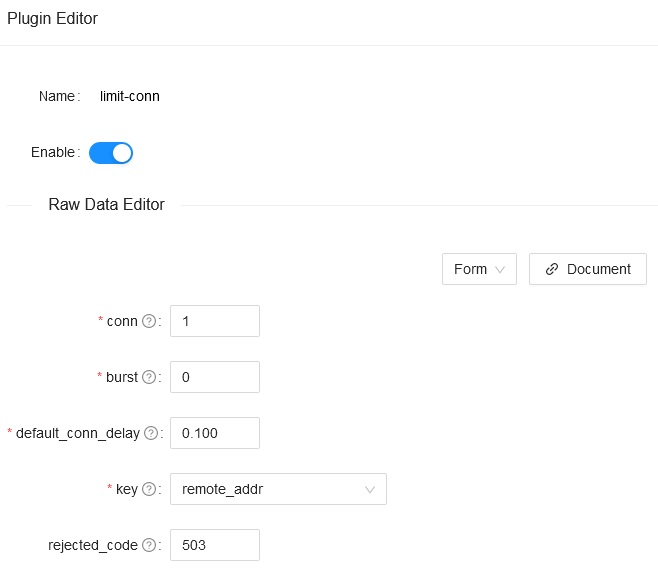 -->
Review Comment:
Do we need to keep this?
##########
docs/en/latest/plugins/limit-conn.md:
##########
@@ -93,17 +99,19 @@ curl http://127.0.0.1:9080/apisix/admin/routes/1 -H 'X-API-KEY: edd1c9f034335f13
}'
```
-You also can complete the above operation through the web interface, first add a route, then add limit-conn plugin:
-
+<!--  -->
-## Test Plugin
+## Example usage
-The parameters of the plugin enabled above indicate that only one concurrent request is allowed. When more than one concurrent request is received, will return `503` directly.
+The example above configures the Plugin to only allow one concurrent request. When more that one request is received, the Plugin will respond with a 503 status code:
Review Comment:
```suggestion
The example above configures the Plugin to only allow one concurrent request. When more than one request is received, the Plugin will respond with a 503 status code:
```
##########
docs/en/latest/plugins/limit-conn.md:
##########
@@ -93,17 +99,19 @@ curl http://127.0.0.1:9080/apisix/admin/routes/1 -H 'X-API-KEY: edd1c9f034335f13
}'
```
-You also can complete the above operation through the web interface, first add a route, then add limit-conn plugin:
-
+<!--  -->
-## Test Plugin
+## Example usage
-The parameters of the plugin enabled above indicate that only one concurrent request is allowed. When more than one concurrent request is received, will return `503` directly.
+The example above configures the Plugin to only allow one concurrent request. When more that one request is received, the Plugin will respond with a 503 status code:
```shell
curl -i http://127.0.0.1:9080/index.html?sleep=20 &
curl -i http://127.0.0.1:9080/index.html?sleep=20
+```
+
+```shell
Review Comment:
I'm not sure if using `shell` here is properly :)
##########
docs/en/latest/plugins/limit-count.md:
##########
@@ -23,33 +29,33 @@ title: limit-count
## Description
-Limit request rate by a fixed number of requests in a given time window.
+The `limit-count` Plugin limits the number of requests to your service by a given count per time.
## Attributes
-| Name | Type | Requirement | Default | Valid | Description |
-| ------------------- | ------- | --------------------------------------- | ------------- | ------------------------------------------------------------------------------------------------------- | ---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- |
-| count | integer | required | | count > 0 | the specified number of requests threshold. |
-| time_window | integer | required | | time_window > 0 | the time window in seconds before the request count is reset. |
-| key_type | string | optional | "var" | ["var", "var_combination", "constant"] | the type of key. |
-| key | string | optional | "remote_addr" | | the user specified key to limit the rate. If the `key_type` is "constant", the key will be treated as a constant. If the `key_type` is "var", the key will be treated as a name of variable. If the `key_type` is "var_combination", the key will be a combination of variables. For example, if we use "$remote_addr $consumer_name" as key, plugin will be restricted by two variables which are "remote_addr" and "consumer_name". If the value of the key is empty, `remote_addr` will be set as the default key.|
-| rejected_code | integer | optional | 503 | [200,...,599] | The HTTP status code returned when the request exceeds the threshold is rejected, default 503. |
-| rejected_msg | string | optional | | non-empty | The response body returned when the request exceeds the threshold is rejected. |
-| policy | string | optional | "local" | ["local", "redis", "redis-cluster"] | The rate-limiting policies to use for retrieving and incrementing the limits. Available values are `local`(the counters will be stored locally in-memory on the node), `redis`(counters are stored on a Redis server and will be shared across the nodes, usually use it to do the global speed limit), and `redis-cluster` which works the same as `redis` but with redis cluster. |
-| allow_degradation | boolean | optional | false | | Whether to enable plugin degradation when the limit-count function is temporarily unavailable(e.g. redis timeout). Allow requests to continue when the value is set to true, default false. |
-| show_limit_quota_header | boolean | optional | true | | Whether show `X-RateLimit-Limit` and `X-RateLimit-Remaining` (which mean the total number of requests and the remaining number of requests that can be sent) in the response header, default true. |
-| group | string | optional | | non-empty | Route configured with the same group will share the same counter |
-| redis_host | string | required for `redis` | | | When using the `redis` policy, this property specifies the address of the Redis server. |
-| redis_port | integer | optional | 6379 | [1,...] | When using the `redis` policy, this property specifies the port of the Redis server. |
-| redis_password | string | optional | | | When using the `redis` or `redis-cluster` policy, this property specifies the password of the Redis server. |
-| redis_database | integer | optional | 0 | redis_database >= 0 | When using the `redis` policy, this property specifies the database you selected of the Redis server, and only for non Redis cluster mode (single instance mode or Redis public cloud service that provides single entry). |
-| redis_timeout | integer | optional | 1000 | [1,...] | When using the `redis` or `redis-cluster` policy, this property specifies the timeout in milliseconds of any command submitted to the Redis server. |
-| redis_cluster_nodes | array | required when policy is `redis-cluster` | | | When using `redis-cluster` policy,This property is a list of addresses of Redis cluster service nodes (at least two). |
-| redis_cluster_name | string | required when policy is `redis-cluster` | | | When using `redis-cluster` policy, this property is the name of Redis cluster service nodes. |
-
-## How To Enable
-
-Here's an example, enable the `limit count` plugin on the specified route when setting `key_type` to `var` :
+| Name | Type | Required | Default | Valid values | Description |
+|-------------------------|---------|-------------------------------------------|---------------|----------------------------------------|------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------|
+| count | integer | True | | count > 0 | Maximum number of requests to allow. |
+| time_window | integer | True | | time_window > 0 | Time in seconds before `count` is reset. |
+| key_type | string | False | "var" | ["var", "var_combination", "constant"] | Type of user specified key to use. |
+| key | string | False | "remote_addr" | | User specified key to base the request limiting on. If the `key_type` attribute is set to `constant`, the key will be treated as a constant value. If the `key_type` attribute is set to `var`, the key will be treated as a name of variable, like `remote_addr` or `consumer_name`. If the `key_type` is set to `var_combination`, the key will be a combination of variables, like `$remote_addr $consumer_name`. If the value of the key is empty, `remote_addr` will be set as the default key. |
+| rejected_code | integer | False | 503 | [200,...,599] | HTTP status code returned when the requests exceeding the threshold are rejected. |
+| rejected_msg | string | False | | non-empty | Body of the response returned when the requests exceeding the threshold are rejected. |
+| policy | string | False | "local" | ["local", "redis", "redis-cluster"] | Rate-limiting policies to use for retrieving and increment the limit count. When set to `local` the counters will be locally stored in memory on the node. When set to `redis` counters are stored on a Redis server and will be shared across the nodes. It is done usually for global speed limiting, and setting to `redis-cluster` uses a Redis cluster instead of a single instance. |
Review Comment:
We have many cases like this: we need to describe each enum value's description. Do you have experience on how to show those descriptions better?
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: notifications-unsubscribe@apisix.apache.org
For queries about this service, please contact Infrastructure at:
users@infra.apache.org